Vulnerability Scanning With Nmap Network Scanning
Vulnerability Scanning with Nmap: Network Scanning

What is Nmap and which problems does it solve in Cybersecurity?
Nmap (Network Mapper) is a powerful open-source network scanning and host discovery tool used in cybersecurity. It allows security professionals and ethical hackers to assess the security posture of computer networks by identifying open ports, services running on those ports, and potential vulnerabilities. Nmap is a versatile and essential utility in the arsenal of cybersecurity experts for conducting network reconnaissance and penetration testing.
Nmap provides the following capabilities and benefits:
- Network Scanning. It sends packets to target hosts and analyzes the responses to determine which ports are open, closed, or filtered. By discovering open ports, administrators can assess potential vulnerabilities and take appropriate security measures.
- Host Discovery. Nmap can efficiently discover hosts on a network by sending specific packets to determine which IP addresses are active and reachable. This feature aids in creating an inventory of devices on the network and identifying unauthorized or rogue systems.
- OS Fingerprinting. Nmap can perform OS fingerprinting by analyzing how a target responds to certain packets. By identifying the underlying operating system, security professionals gain insight into potential security weaknesses specific to that OS.
- Version Detection. The tool can determine the version and service details of applications running on open ports. Knowing the specific service version helps in identifying known vulnerabilities associated with that version.
- Scripting Engine. Nmap features a powerful scripting engine called NSE (Nmap Scripting Engine). This enables users to create custom scripts or use existing ones to automate tasks, gather more information, or perform advanced network scanning techniques.
- Cybersecurity Applications. In cybersecurity, Nmap plays a vital role in various scenarios:
- Network Security Audits: Nmap helps assess the security of a network by revealing potential entry points and vulnerabilities that attackers could exploit.
- Penetration Testing: Ethical hackers use Nmap during penetration testing to identify weak points in a network's defenses, simulating real-world attack scenarios.
- Incident Response: In the event of a security breach, Nmap can assist in understanding the scope and impact of the incident by scanning affected systems.
- Network Mapping: Nmap aids in creating visual representations of network topologies, allowing administrators to manage and secure the network effectively.
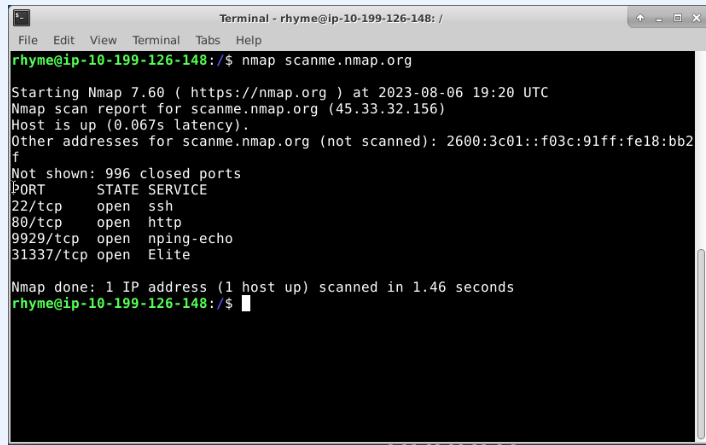
Perform a Basic Ping Scan Using the Hostname scanme.nmap.org
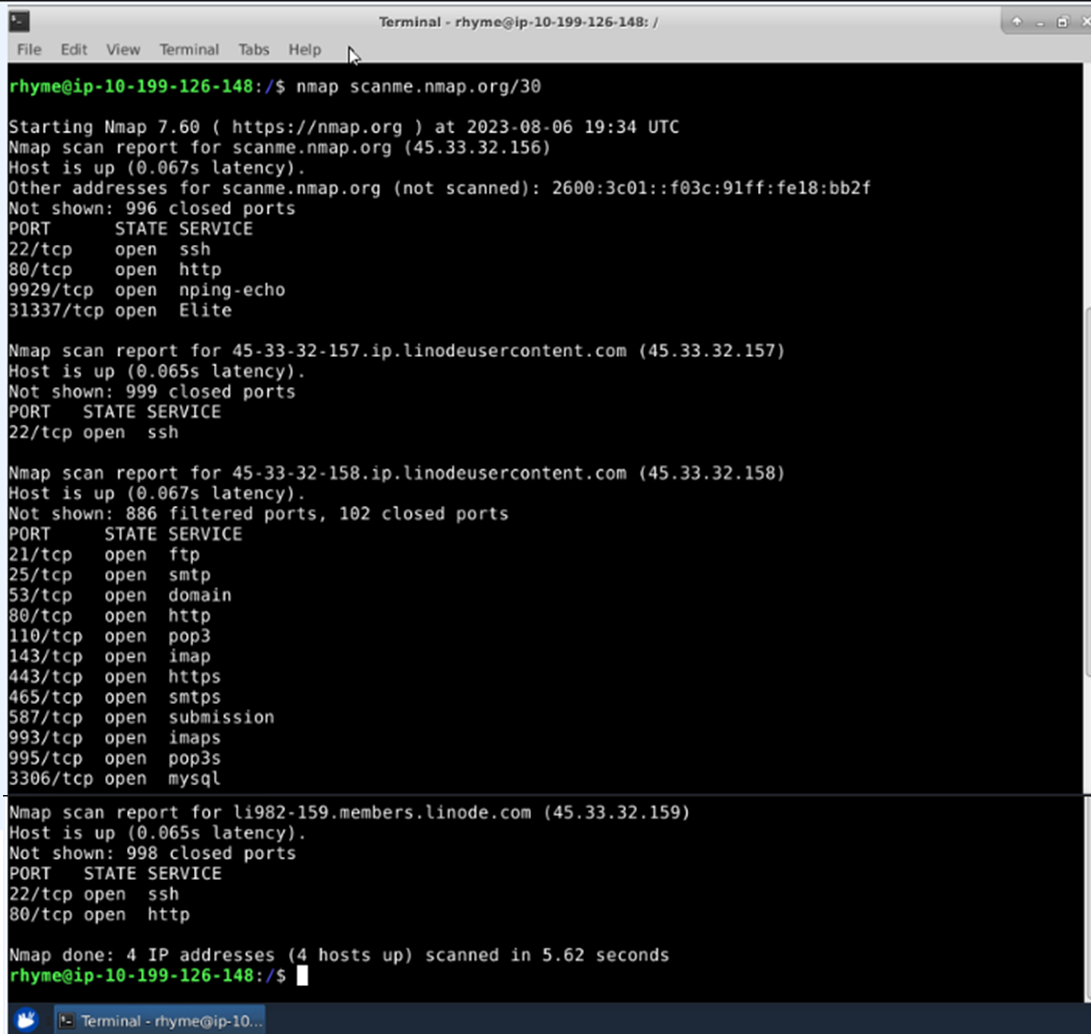
Perform a Scan of all four IP addresses of a Web Server’s /30 Subnet
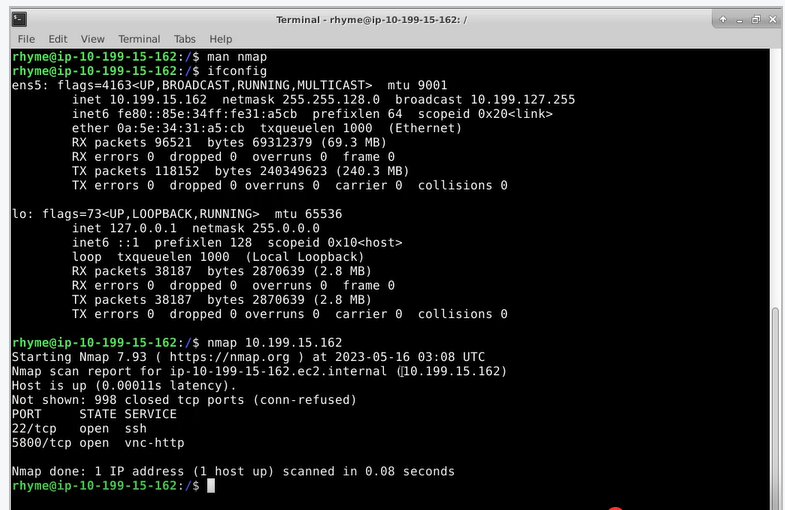
#### Run an Nmap Scan on an Authorized Target and Reference the Man Page as needed
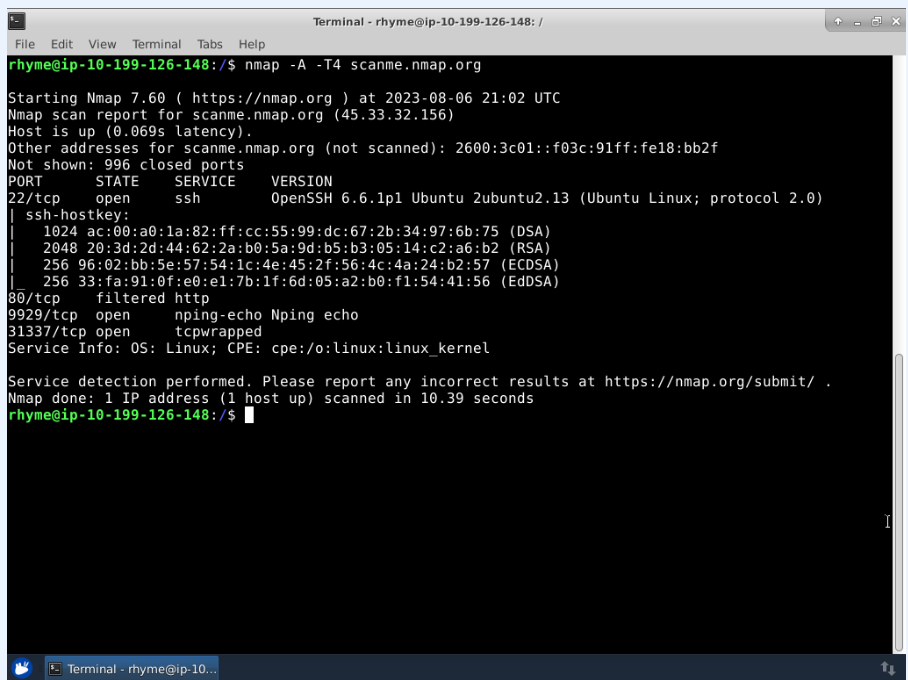
#### Perform an Nmap Scan Using Options to Further Assess the Network
#### Output Nmap Scan Results to a File
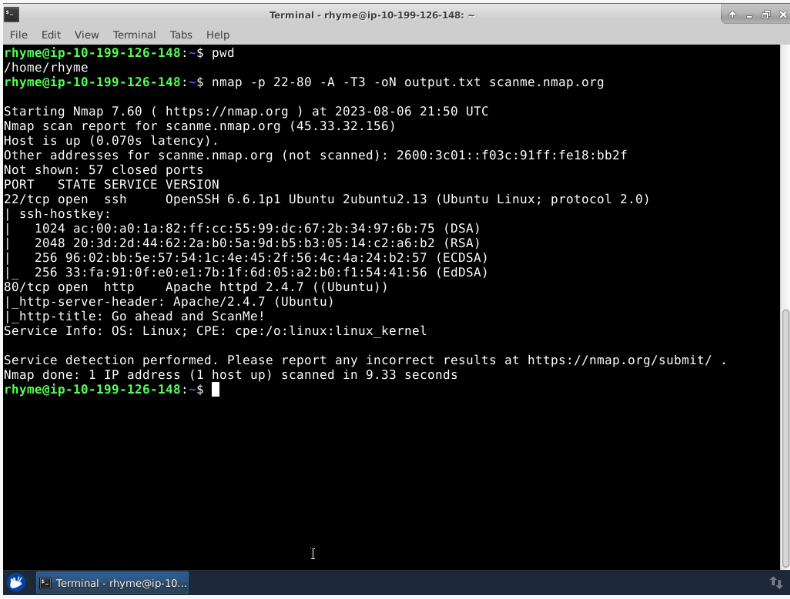
- Nmap option P for port. Here I specified scanning of port 80 only
- Option A to enable OS detection, version detection, script scanning, and trace route.
- We are enabling option oN to output the scan results to a text file named scan.txt
- The hostname followed by the /30 subnet specification, scanme.nmap.org /30
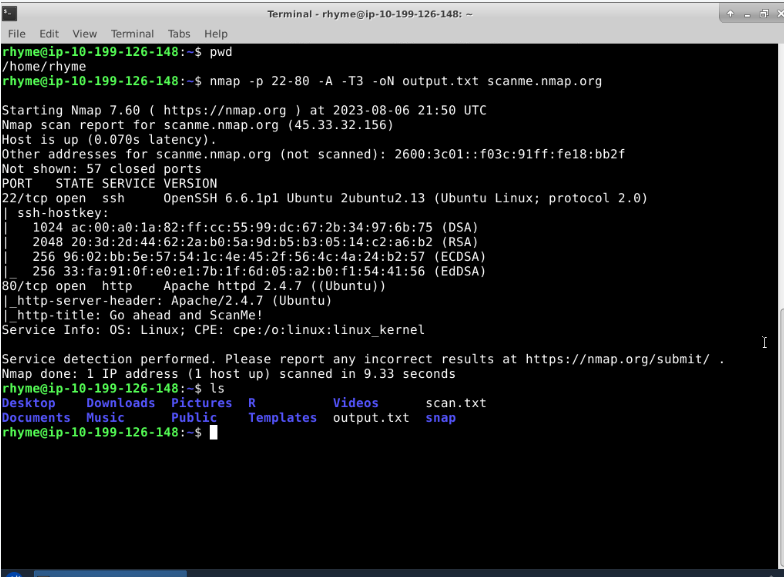
#### Verification of Output File
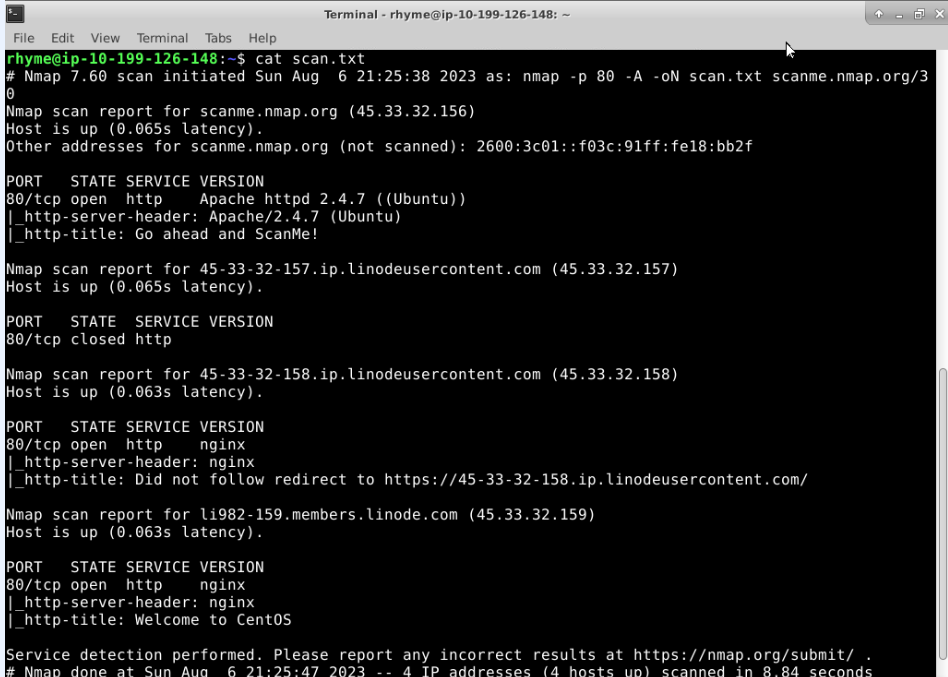
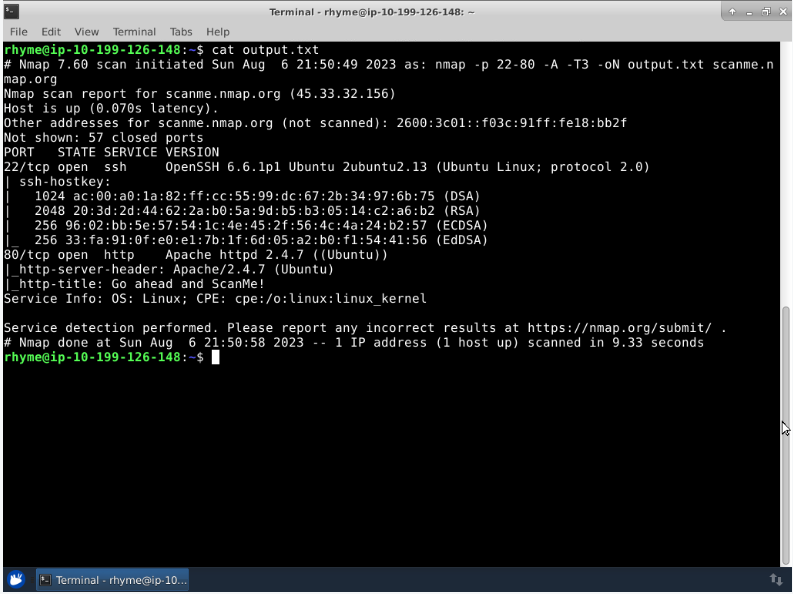
#### Read the Contents of the Output File
#### Scenario: Evaluate the security of a company’s web server to ensure that it is secure against potential attacks. We can perform a scan to collect information about its configuration, running services, and open ports.
This process can help us to assess the state of the server’s security to uncover any issues that can potentially expose it to threats. As a followup to our assessment, we can determine next steps to enhance the security of the web server and create a baseline for future assessments.
- Initiate a scan only on port 80, the default HTTP port
- - A option for the aggressive scan option will enable multiple features including OS detection, version detection, and script scanning.
- This option allows us to gather as much information as possible about the server to identify potential vulnerabilities or misconfigurations related to the web service running on port 80.
- Target is the /30 CIDR range of the web server at domain scanme.nmap.org /30
- -oN option with scan.txt will save the output of the scan to a file named scan.txt so that it will be accessble for later review
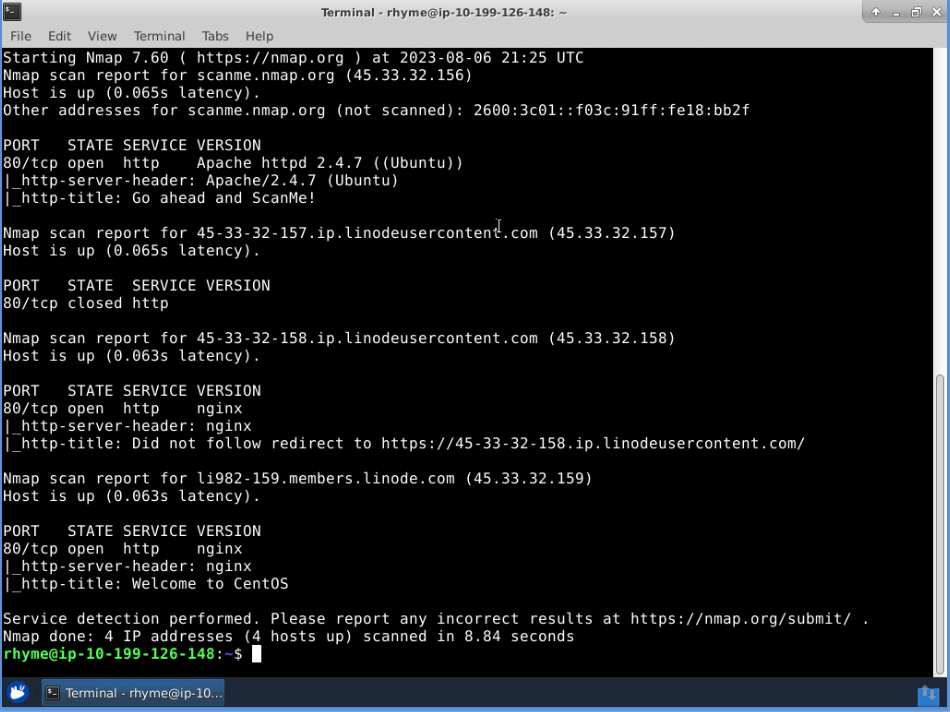
Based on the scan results:
We observe that there is a particular IP address that is showing port 80 running HTTP as filtered. This indicates that Nmap is not a ble to determine if the port is in an open or closed state. This may be due to a firewall, an Intrusion Prevention System (IPS), a router, or another security appliance that is blocking or filtering the probe packets being sent by Nmap.
We observe that NGINX is associated with a few IP addresss. It is common for NGINX to be open and running on port 80, as it is often used as a web server, a reverse proxy server, or a load balancer. Having the service run on port 80 allows it to serve websites and applications to clients using standard HTTP connections.
It is critical to maintain regular updates to NGINX to the latest patch versions and to perform any OS hardending features to ensure proper configuration that will help mitigate potential vulnerabilities.
We observe that this this server is also running on a CentOS machine. Knowing the OS is helpful in allowing to provide tailored recommendations to the security team for securing the system with any specific configuration settings or services and features that need to be disabled or enabled to provide the greatest level of protection.
Run a Customized Scan on a Target Host
Reference: Nmap Port Scanning Optionss Guide



