The Art of Reconnaissance in Cybersecurity
The Art of Reconnaissance: A Critical Tool in Cybersecurity

Welcome to Day 4 of my 100 Days of Cybersecurity Challenge. As I progress through this intensive learning journey, I’m thrilled to share some insights into one of the most critical aspects of cybersecurity: reconnaissance.
Reconnaissance in the digital realm is akin to an intelligence-gathering mission that precedes any strategic battle. This initial phase is about collecting exhaustive information regarding a potential target, which could range from a network to an entire organization’s online presence.
The Defensive Edge of Reconnaissance
For those of us on the defensive side of cybersecurity, reconnaissance is not just a task but an advantage. It allows us to scan for and scrutinize the data that’s publicly available about our systems. We’re talking about unraveling vulnerabilities and weak links that could be fortified to ward off cyber threats. By doing so, we preemptively shield our digital assets from nefarious attacks and secure the cyber fortresses we safeguard.
The Offense Uses It Too
However, it’s a double-edged sword. Bad actors are also employing reconnaissance to scope out soft spots in cyber defenses. They meticulously gather data, seeking out open ports or mining personal details that could be woven into the fabric of sophisticated social engineering and phishing exploits. It’s a chilling reminder of the constant vigilance required in our field.
Tools of the Trade
My hands-on learning session had me engaging with the essential tools of cybersecurity reconnaissance. I investigated domain ownership through WHOIS, conducted DNS queries using nslookup and dig, and searched for internet-connected devices with Shodan. I also probed the Google Hacking Database to discover security gaps that are exposed via search queries. Additionally, other resources like the Threat Intelligence Platform, viewdns.info, and Censys offered me a comprehensive overview of internet assets and their potential vulnerabilities.
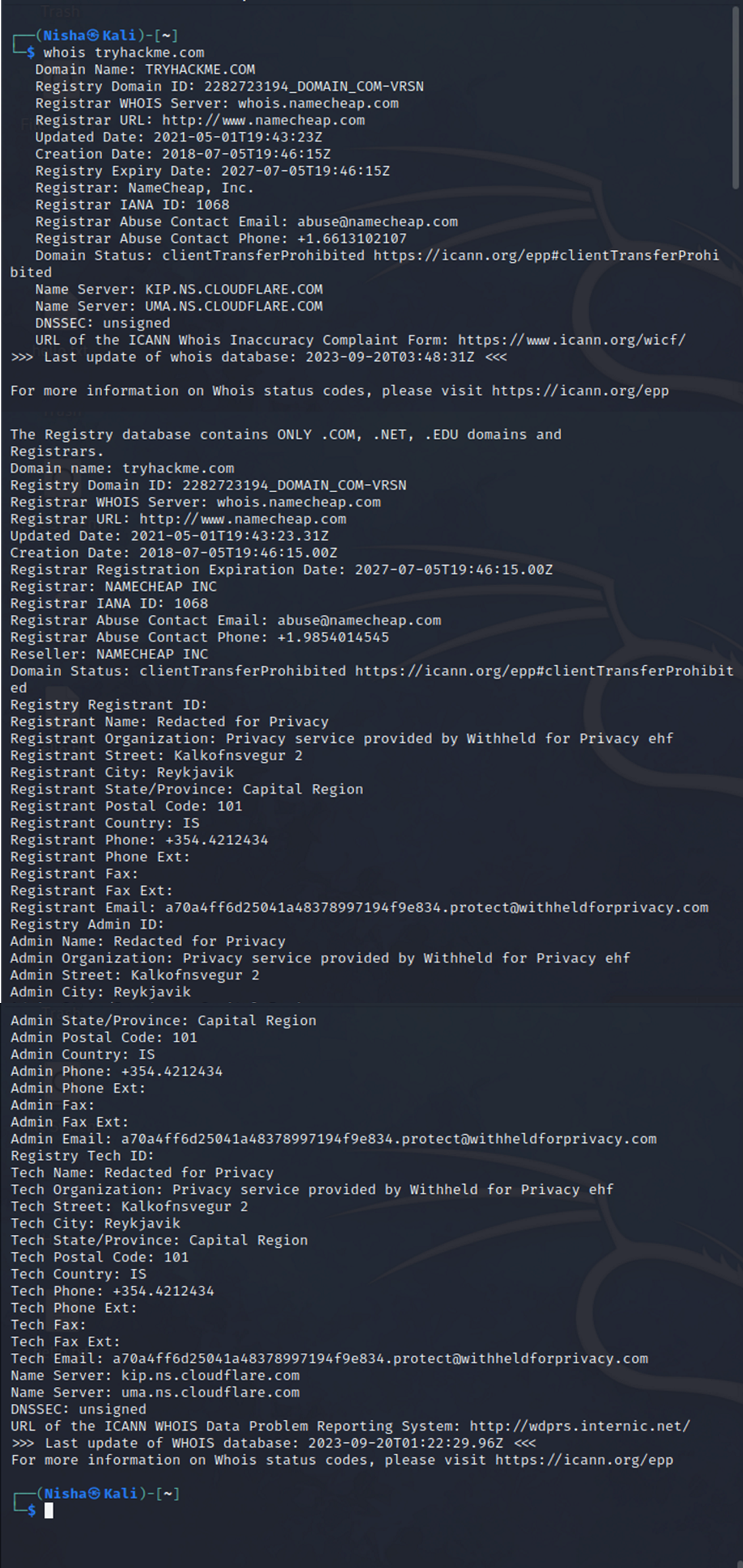
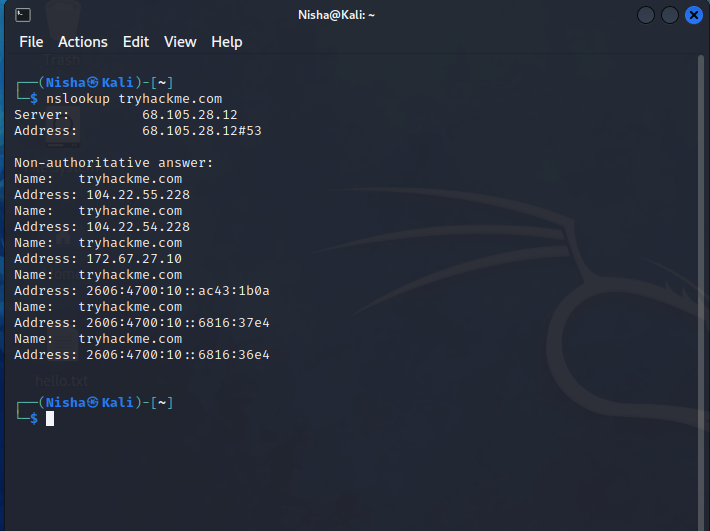
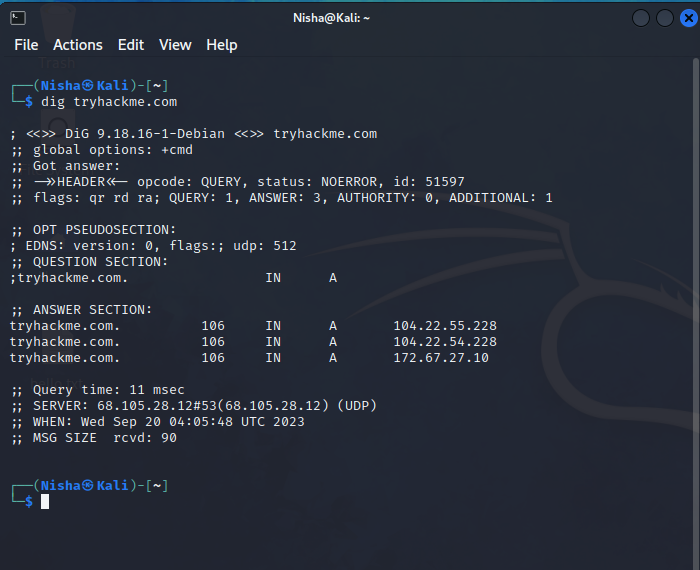
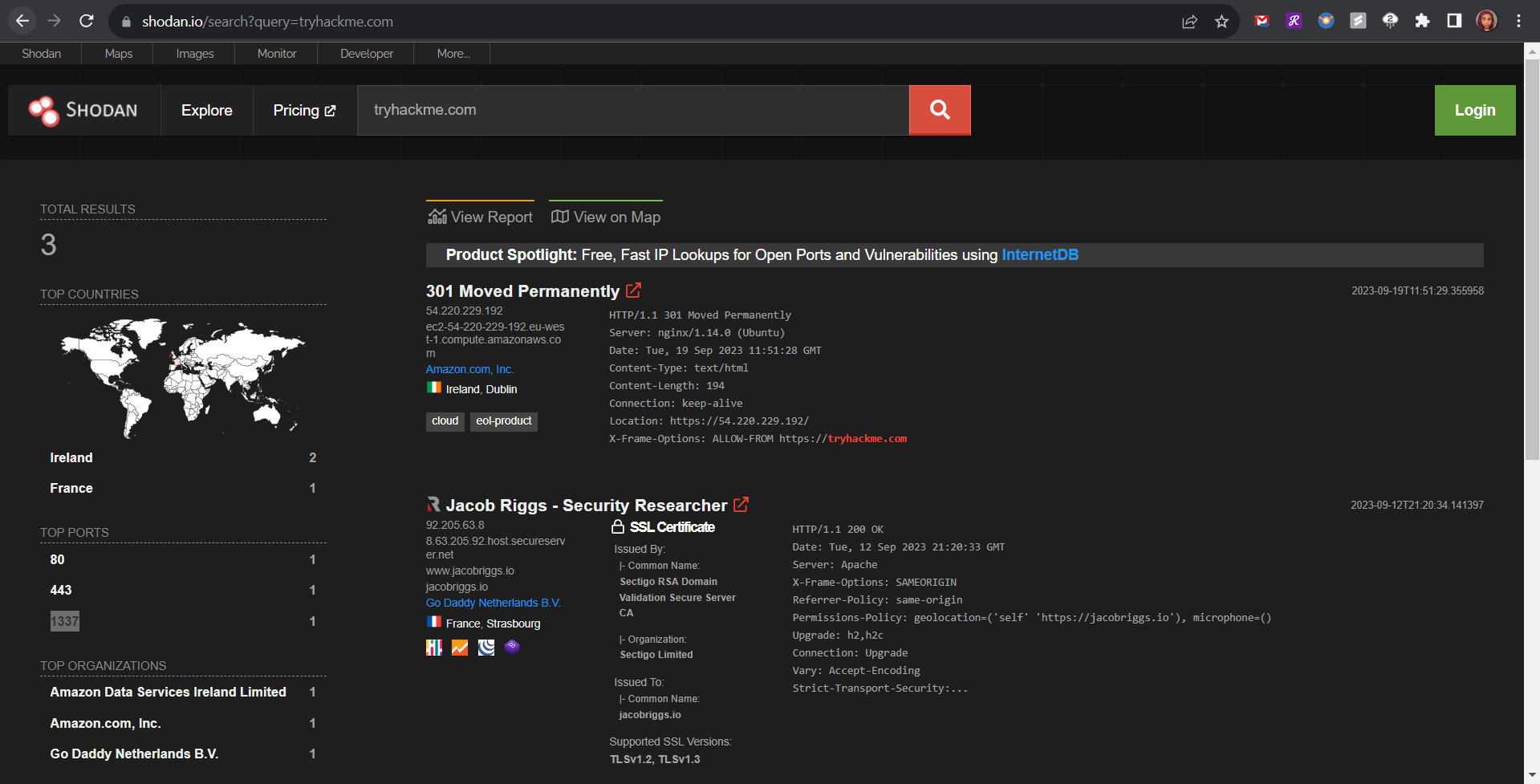
Resources and Moving Forward
I’ve also been fortunate to access remarkable resources to bolster my reconnaissance skills. Platforms like Cisco Skills for All offer an ‘Ethical Hacker’ course, while ‘The Cyber Mentor’ provides a comprehensive ‘Ethical Hacking in 15 Hours’ training. For a more focused approach, TryHackMe’s ‘Passive Reconnaissance’ module was particularly insightful.

As I continue on this challenge, my excitement only grows. I’m committed to deepening my understanding of cybersecurity and amping up my skills to stay ahead in this ever-evolving cyber battleground. Stay tuned for more updates as I venture through the #100DaysOfCybersecurity.
Until then, stay secure and vigilant in the cybersecurity quest!
Connect with me on LinkedIn: https://www.linkedin.com/in/nishaprudhomme/
#NotesbyNisha #cybertechdave100daysofcyberchallenge #cyversity #Womenintech #blackwomenintech #womenincybersecurity #Reconnaissance #CybersecurityDefense #StaySecure #cybersecurity



