Vulnerability Scanning Nessus
Vulnerability Scanning with Tenable Nessus
🚀 Day 3 of my #100DaysOfCybersecurity challenge is all about getting hands-on with Tenable Nessus! 🕵️♂️

Just dived into this powerful cybersecurity tool developed by Tenable, Inc. It’s a go-to solution for vulnerability assessment and management.
Here’s a peek at what I was able to accomplish:
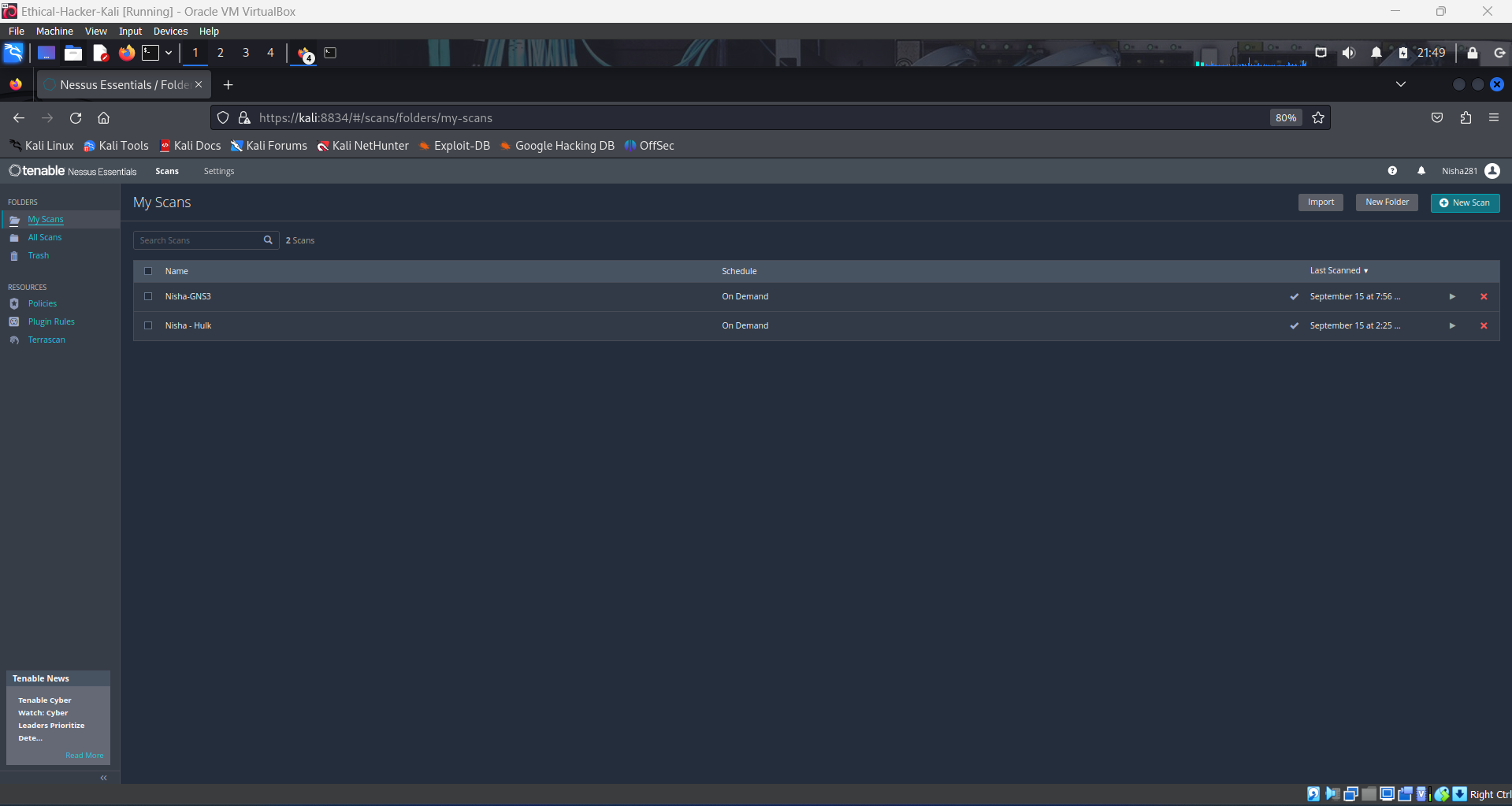
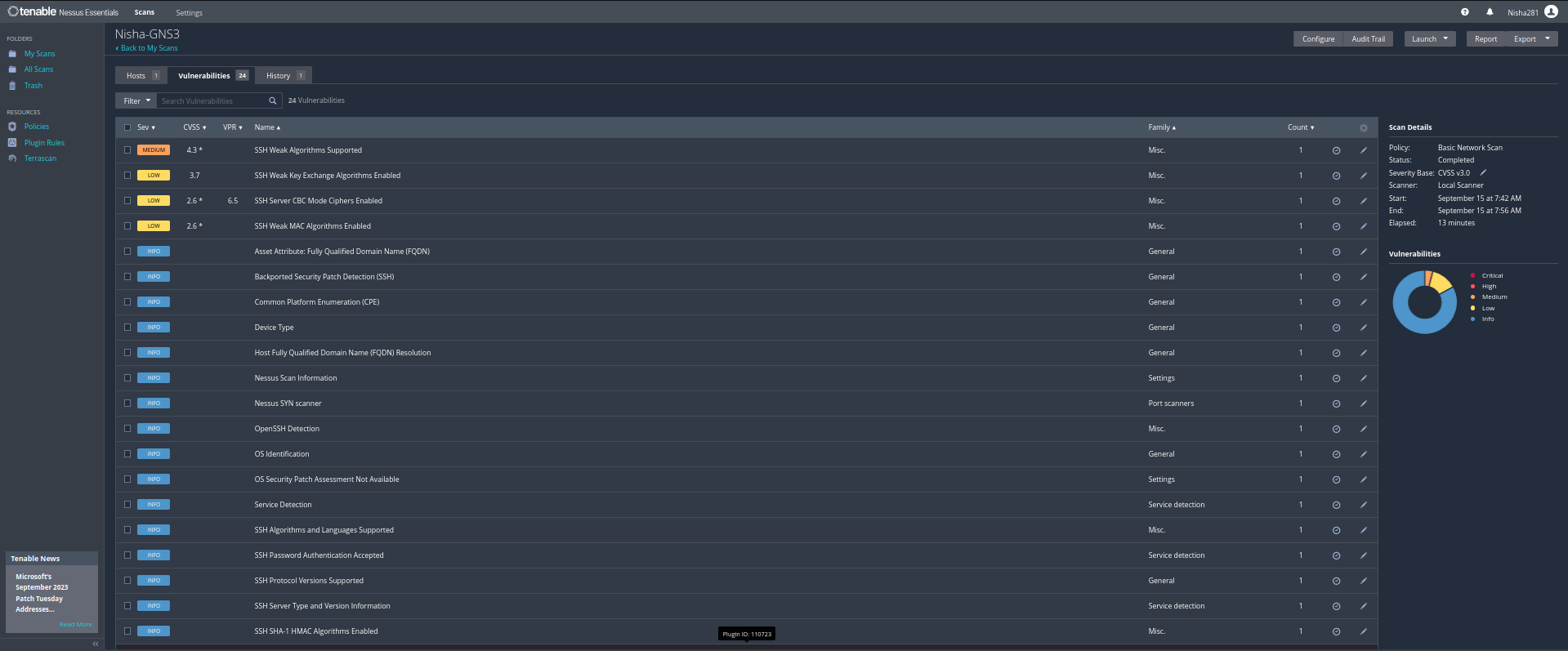
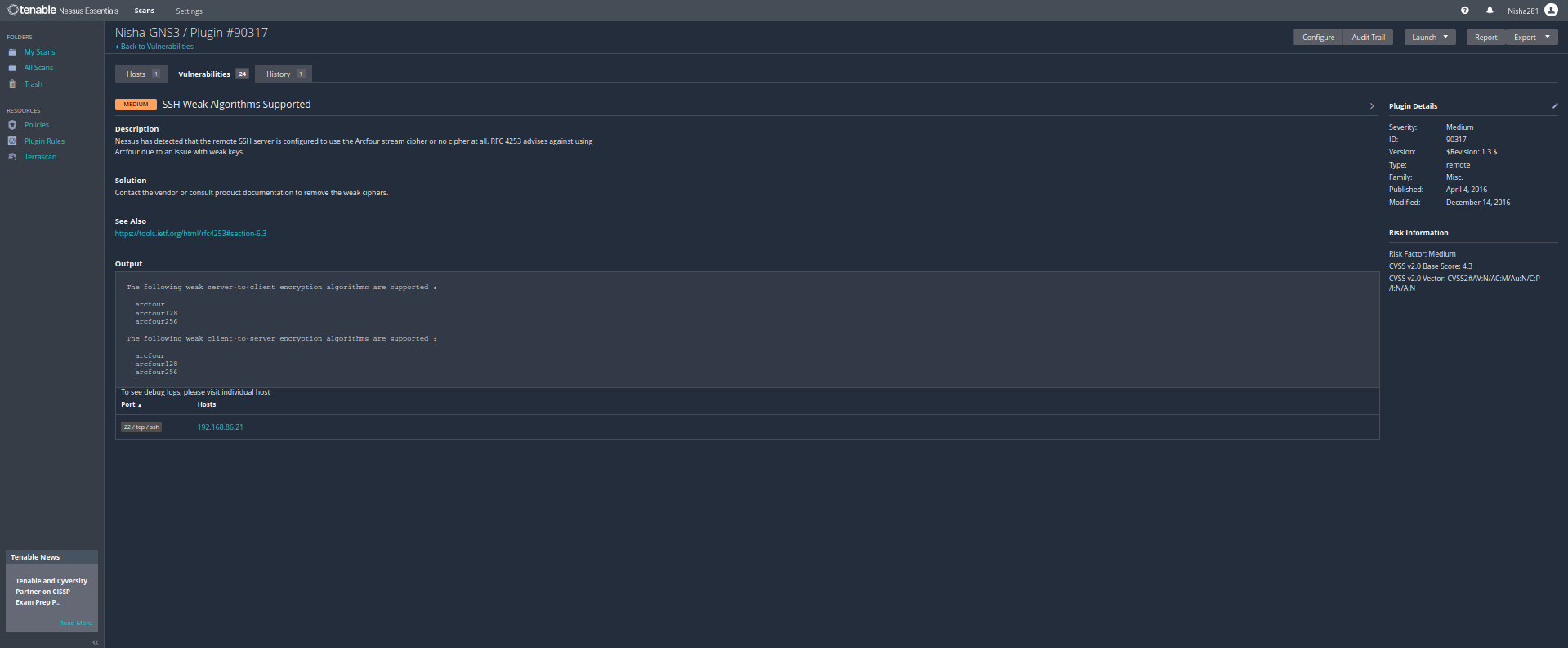
- I downloaded and installed Nessus as a tool on my Kali Linux VM and then I initiated Basic Scans against two other devices on my home network:
- 💻 Hulk - a Windows 10 VM that is being used as a Universal Forwarder for sending WinEvent logs to my Splunk server
- 💻 GNS3 Server VM - a network simulator application that is running on a Linux Server VM
 </br>
</br>
 </br>
</br>
Here's what #Nessus can do:
💪 Benefits and Solutions:
- 🔍 Vulnerability Assessment: It scans and assesses your systems, devices, and apps to pinpoint security weaknesses, known vulnerabilities, and misconfigurations. From servers to routers, it's got you covered.
- ✔ Compliance Check: Helps meet regulations like PCI DSS, HIPAA, and NIST by finding non-compliance vulnerabilities.
- ✳ Risk Analysis: Rates vulnerabilities by severity, so you can tackle the big problems first.
- 📈Asset Management: Keeps your asset inventory current, making management and security easier.
- 👊🏽 Action Time: After scanning, prioritize, remediate, and monitor vulnerabilities.
The following resources were helpful for my learning activities:
- 📽 Josh Madakor's Nessus Scanning Tutorial: https://lnkd.in/ga7tCUNA
- 📽 The Cyber Mentor's Nessus Scanning Tutorial: https://lnkd.in/gQCF6hKP
- 📽 TryHackme: Nessus Scanning Lab: https://lnkd.in/guym5RV9
Stay tuned for more of my cybersecurity adventures! Follow me on LinkedIn!




