Vulnerability Scanning With Openvas Unveiling Cybersecurity Insights
Vulnerability Scanning with OpenVAS: Unveiling Cybersecurity Insights
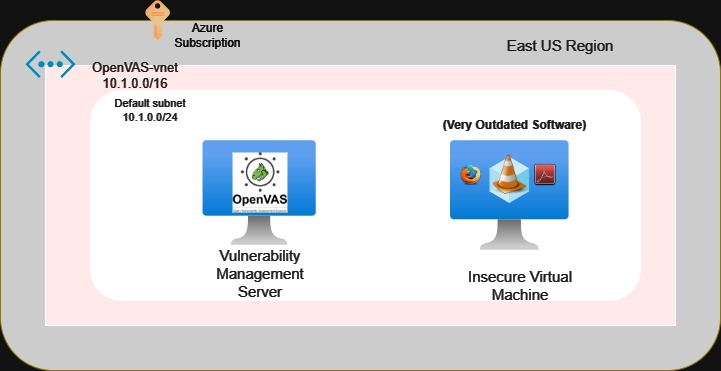
In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is paramount. This is where tools like OpenVAS (Open Vulnerability Assessment System) come into play, offering a powerful solution for identifying and mitigating vulnerabilities within your network. In this article, we will explore the world of OpenVAS, its purpose, and the critical differences between unauthenticated and credentialed scans. Join us on a journey through the realm of vulnerability management.
What is OpenVAS?
OpenVAS, an open-source vulnerability scanner, is a robust tool designed to detect and assess security vulnerabilities within a network. It’s a vital component of any organization’s cybersecurity arsenal. With its comprehensive database of known vulnerabilities and a range of scanning techniques, OpenVAS empowers security professionals to proactively identify weaknesses before malicious actors can exploit them.
The Purpose of OpenVAS
At its core, OpenVAS serves several essential purposes:
1. Vulnerability Identification
OpenVAS scans your network, searching for known vulnerabilities in software, configurations, and systems. By pinpointing these weak spots, you can take proactive measures to address them before they are exploited by cybercriminals.
2. Risk Mitigation
Once vulnerabilities are identified, OpenVAS provides actionable insights to help prioritize and mitigate risks. This allows organizations to allocate resources efficiently and focus on addressing the most critical security issues first.
3. Compliance
Many industries and regulatory bodies require organizations to conduct regular vulnerability assessments as part of compliance efforts. OpenVAS helps meet these requirements by providing detailed reports on vulnerabilities and their remediation status.
Unauthenticated vs. Credentialed Scans: Unmasking the Difference
One crucial aspect of vulnerability scanning with OpenVAS is understanding the distinction between unauthenticated and credentialed scans. Let’s delve into this difference:
Unauthenticated Scans
Unauthenticated scans, also known as remote scans, are conducted without providing any login credentials to the target systems. These scans are akin to an external perspective and can identify vulnerabilities that are visible to an attacker with no special access.
Credentialed Scans
Credentialed scans, on the other hand, involve providing login credentials (such as usernames and passwords) to the target systems. This approach grants OpenVAS deeper access, allowing it to inspect the system from an internal perspective. Credentialed scans can uncover vulnerabilities that are not visible externally, such as misconfigurations or weak security settings.
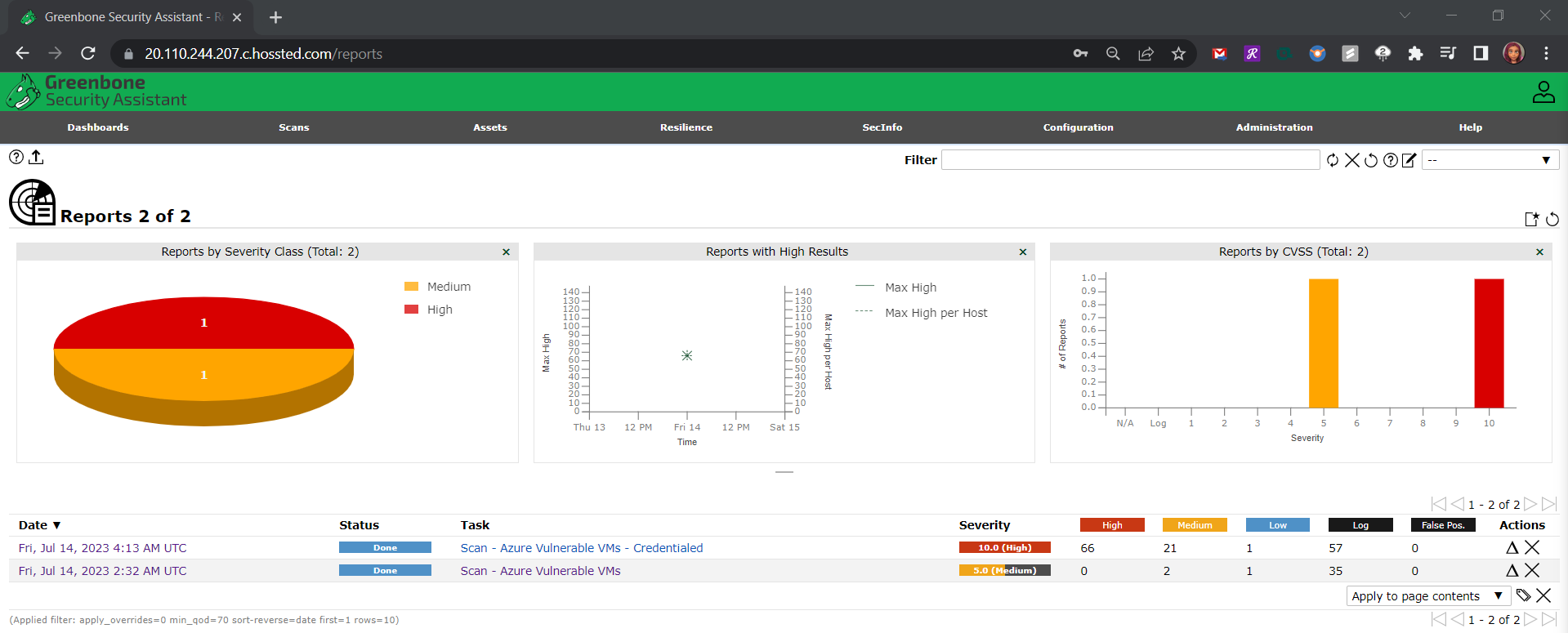
Leveraging OpenVAS in Vulnerability Management
Vulnerability management is an essential aspect of cybersecurity, and OpenVAS plays a pivotal role in this process. Here’s how:
1. Detection
OpenVAS helps organizations detect vulnerabilities by scanning their network and systems regularly. This proactive approach allows for early detection and mitigation, reducing the window of opportunity for potential attackers.
2. Prioritization
Not all vulnerabilities are created equal. OpenVAS assists in prioritizing remediation efforts by categorizing vulnerabilities based on their severity and potential impact. This ensures that resources are allocated to address the most critical issues first.
3. Remediation
Once vulnerabilities are identified, OpenVAS provides guidance on how to remediate them effectively. After implementing remediation measures, subsequent scans can verify the success of these actions.
4. Compliance Reporting
For organizations subject to regulatory requirements, OpenVAS generates compliance reports that demonstrate adherence to security standards and provide evidence of vulnerability assessment efforts.
In a world where cyber threats are constantly evolving, OpenVAS stands as a formidable ally in the battle to secure your digital assets. By understanding its purpose, the difference between unauthenticated and credentialed scans, and its role in vulnerability management, you can harness the power of OpenVAS to safeguard your organization’s cybersecurity posture.
With OpenVAS as part of your arsenal, you’re not just reacting to threats; you’re proactively securing your network, one vulnerability at a time.
So, are you ready to take the next step in bolstering your cybersecurity defenses with OpenVAS? Dive in and discover the vulnerabilities lurking within your network, and let OpenVAS be your guide to a safer digital future.
For a detailed step-by-step guide on setting up and using OpenVAS, check out my project walkthrough on GitHub: Azure Vulnerability Management




