Room Link: https://tryhackme.com/r/room/defensivesecurity
Task 1 - Introduction to Defensive Security
Learning Objectives: Offensive security primarily aims at breaking into systems through various methods like exploiting bugs, abusing insecure setups, and bypassing access control policies. This is the realm of red teams and penetration testers.
On the other hand, defensive security focuses on two key tasks:
- Preventing intrusions from occurring.
- Detecting intrusions when they happen and responding appropriately.
Blue teams are central to the defensive security field, and their responsibilities include:
- User Cyber Security Awareness: Training users to protect against attacks targeting their systems.
- Documenting and Managing Assets: Keeping track of systems and devices to manage and protect them effectively.
- Updating and Patching Systems: Ensuring all systems are updated and patched to defend against known vulnerabilities.
- Setting Up Preventative Security Devices: Implementing firewalls and intrusion prevention systems (IPS) to control and block network traffic based on rules and attack signatures.
- Setting Up Logging and Monitoring Devices: Monitoring the network to detect malicious activities and intrusions, such as unauthorized devices appearing on the network.
- Security Operations Center (SOC)
- Threat Intelligence
- Digital Forensics and Incident Response (DFIR)
- Malware Analysis
Answer: Blue Team
Task 2 - Areas of Defensive Security
Areas of Defensive Security: An Overview
In the "Intro to Defensive Security" room, two primary topics are covered:
- Security Operations Center (SOC) and Threat Intelligence
- Digital Forensics and Incident Response (DFIR), including Malware Analysis
Security Operations Center (SOC)
A Security Operations Center (SOC) is a team of cybersecurity experts who monitor network systems to detect and respond to malicious activities. Key areas of focus for a SOC include:
- Vulnerabilities: Identifying and patching system weaknesses to prevent exploitation.
- Policy Violations: Ensuring compliance with security policies, such as preventing the unauthorized uploading of sensitive data.
- Unauthorized Activity: Detecting and blocking unauthorized access, such as stolen login credentials.
- Network Intrusions: Identifying and mitigating intrusions, whether through malicious links or exploited servers.
SOC responsibilities also include threat intelligence, which involves gathering information on potential threats to prepare and defend against adversaries.
Threat Intelligence
Threat intelligence involves collecting and analyzing data on actual and potential threats to inform a company’s defense strategies. This process includes:
- Data Collection: Gathering information from network logs and public sources.
- Data Processing and Analysis: Organizing data for analysis to understand attackers' motives and tactics.
- Actionable Insights: Developing recommendations to mitigate threats and enhance security.
- Understanding adversaries' tactics helps predict and counteract their actions effectively.
Digital Forensics and Incident Response (DFIR)
DFIR encompasses the following areas:
1. Digital Forensics: Investigating and analyzing digital evidence to understand attacks and identify perpetrators. Key areas include:
- File System Analysis: Examining storage for programs, files, and deleted content.
- System Memory Analysis: Investigating system memory for malicious programs.
- System Logs: Reviewing logs for activity and traces of attacks.
- Network Logs: Analyzing network traffic to detect ongoing or past attacks.
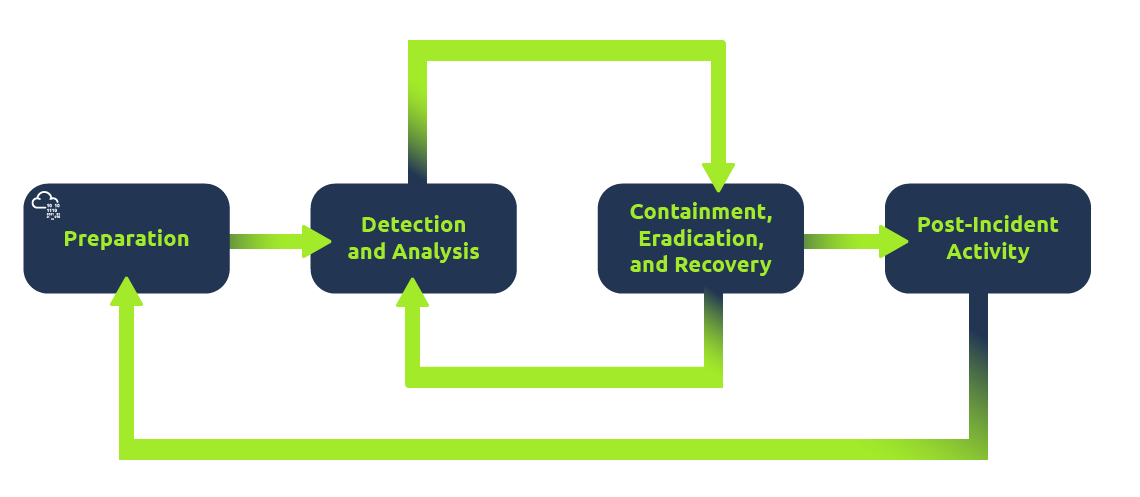
2. Incident Response: Managing and responding to cyber incidents to minimize damage and recover quickly. The incident response process includes:
- Preparation: Training teams and implementing preventive measures.
- Detection and Analysis: Identifying and assessing incidents.
- Containment, Eradication, and Recovery: Stopping the spread, eliminating threats, and restoring systems.
- Post-Incident Activity: Reporting and learning from incidents to prevent future occurrences.
Malware Analysis
Malware analysis involves studying malicious software to understand its behavior and impact. Types of malware include:
- Virus: Code that spreads by altering files.
- Trojan Horse: Malicious software disguised as a legitimate program.
- Ransomware: Software that encrypts files and demands a ransom for decryption.
Analysis methods include:
- Static Analysis: Inspecting malware without executing it, often requiring knowledge of assembly language.
- Dynamic Analysis: Running malware in a controlled environment to observe its behavior.
By understanding malware, security professionals can develop strategies to detect, prevent, and respond to such threats effectively.
Question: What would you call a team of cyber security professionals that monitors a network and its systems for malicious events?
Answer: Security Operations Center
Question:What does DFIR stand for?
Answer: Digital Forensics and Incident Response
Question:Which kind of malware requires the user to pay money to regain access to their files?
Answer: ransomware
Task 3 - Practical Example of Defensive Security
By understanding malware, security professionals can develop strategies to detect, prevent, and respond to such threats effectively.
By understanding malware, security professionals can develop strategies to detect, prevent, and respond to such threats effectively.
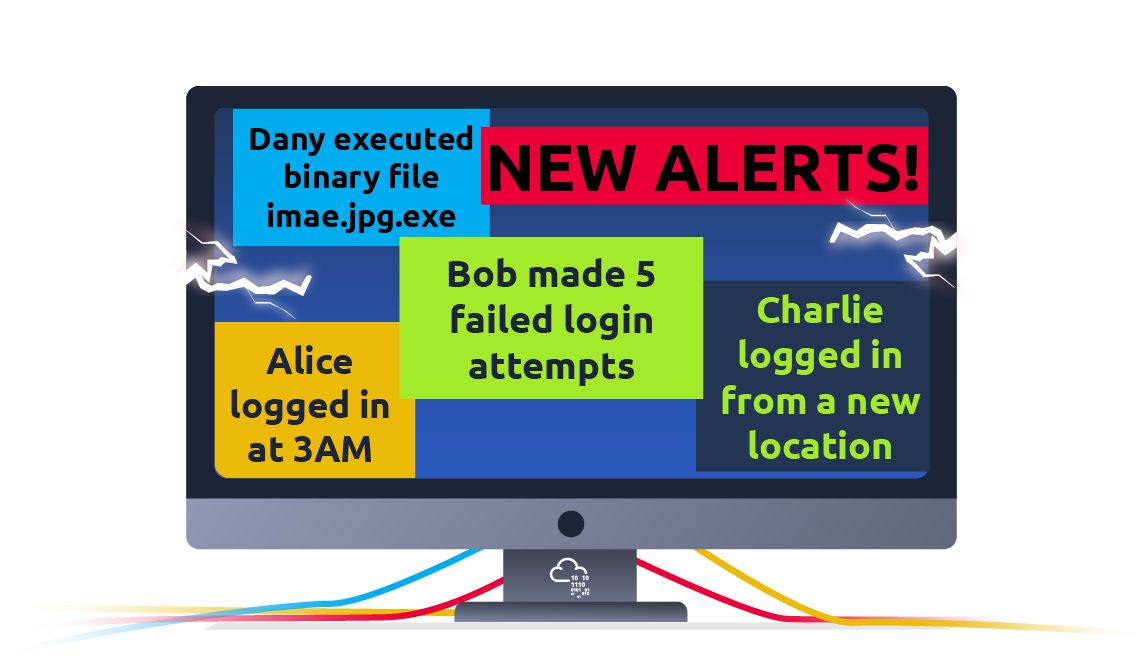
In this exercise, we will interact with a SIEM to monitor the different events on our network and systems in real-time. Some of the events are typical and harmless; others might require further intervention from us. Find the event flagged in red, take note of it, and click on it for further inspection.
Next, we want to learn more about the suspicious activity or event. The suspicious event might have been triggered by an event, such as a local user, a local computer, or a remote IP address. To send and receive postal mail, you need a physical address; similarly, you need an IP address to send and receive data over the Internet. An IP address is a logical address that allows you to communicate over the Internet. We inspect the cause of the trigger to confirm whether the event is indeed malicious. If it is malicious, we need to take due action, such as reporting to someone else in the SOC and blocking the IP address.
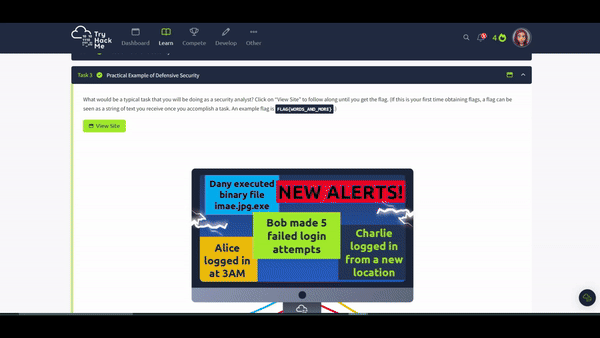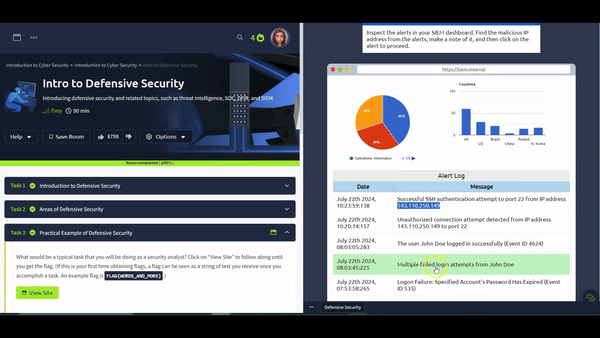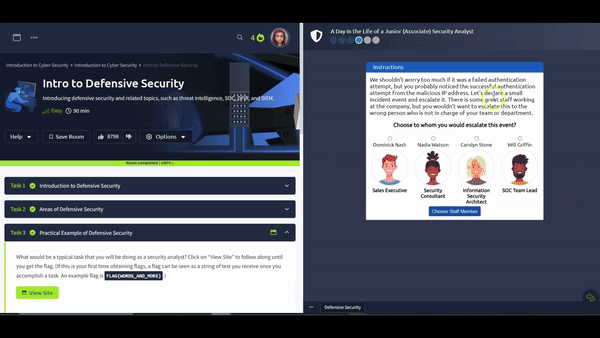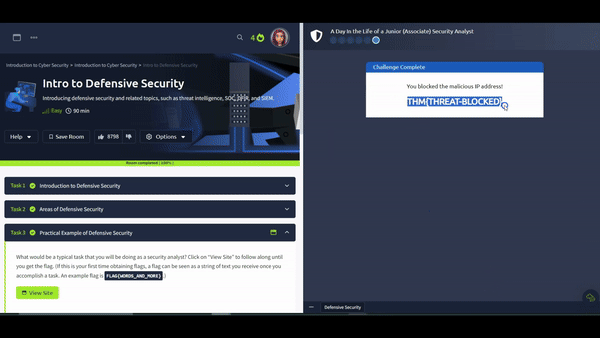
Question: What is the flag that you obtained by following along?
Answer: THM{THREAT-BLOCKED}


